Cut the Ransomware Kill Chain with Isolated Management Infrastructure
Social engineering and weak systems are the biggest ransomware threat vectors. Rather than focusing on defense, organizations need the ability to go on the offensive when ransomware strikes. This can only be done through what CISA calls the Isolated Management Infrastructure (IMI). IMI helps you:
- Stop the spread: Bring affected devices and infrastructure offline
- Recover fast: Clean and restore from secure, isolated backups
- Close threat vectors: Fully segment admin networks and implement automated patching
ZPE Systems’ Network Automation Blueprint gives you a step-by-step walkthrough to setting up your IMI. Download the blueprint now to make sure you can cut the ransomware kill chain.

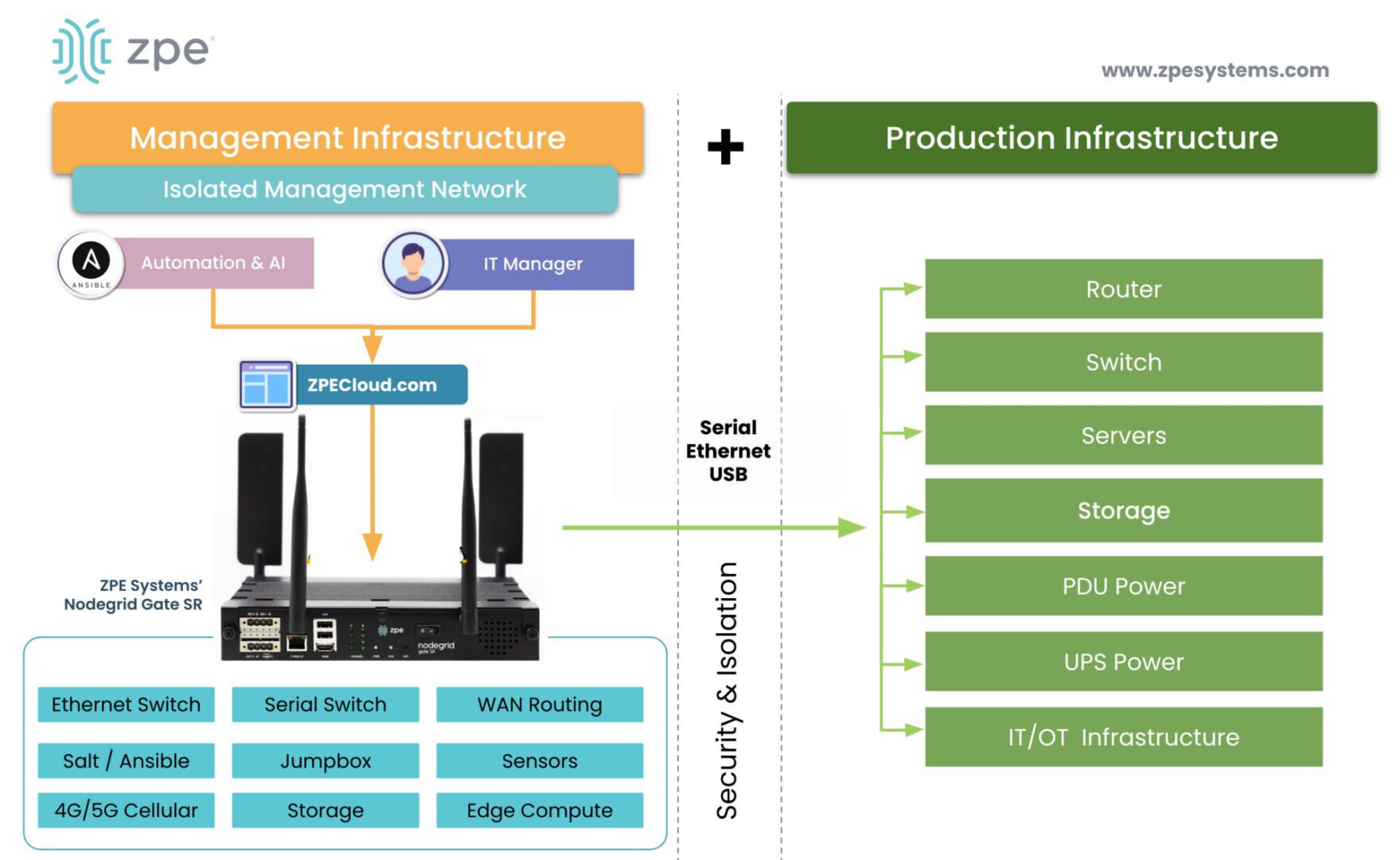
The IMI fully separates the management network from the production network, so that production is not directly managed and that management does not depend on production infrastructure. Additionally, the IMI calls for segmenting the management network, and routing BMC and IPMI ports to terminate on top-of-rack switches, which prevents the creation of a wide and exposed IT network. This architecture also incorporates zero trust using NetDevOps processes. In order for changes to be made, change requests must be reviewed and approved by a committee.
The Isolated Management Infrastructure (IMI) offers the following benefits:
- No more automation anxiety: The IMI is an environment where staff can build their automation skills, without worrying whether they’ll break the production network.
- No more outdated systems: The IMI is where staff can build end-to-end pipelines for automated patching, so their systems are always up to date.
- No more collateral damage: The IMI incorporates zero trust security and segmentation. If an attack slips through the cracks, it can’t spread beyond the entry point.
- And more…

