What Is SASE Network Security? A Beginner’s Guide

Quick Links
In this guide, we’ll cover everything you need to know about SASE network security, including how it works, how it can benefit your organization, and how to get started with implementation.
What is SASE network security?
SD-WAN uses intelligent routing policies to identify cloud-destined traffic and automatically route that traffic through the SASE security stack in the cloud. This reduces the load on the primary firewall which improves latency on the enterprise network. Plus, thanks to cloud-based security technology like Firewall as a Service (FWaaS) and Cloud Access Security Broker (CASB), SASE network traffic can be protected by the same policies and controls as enterprise network traffic.
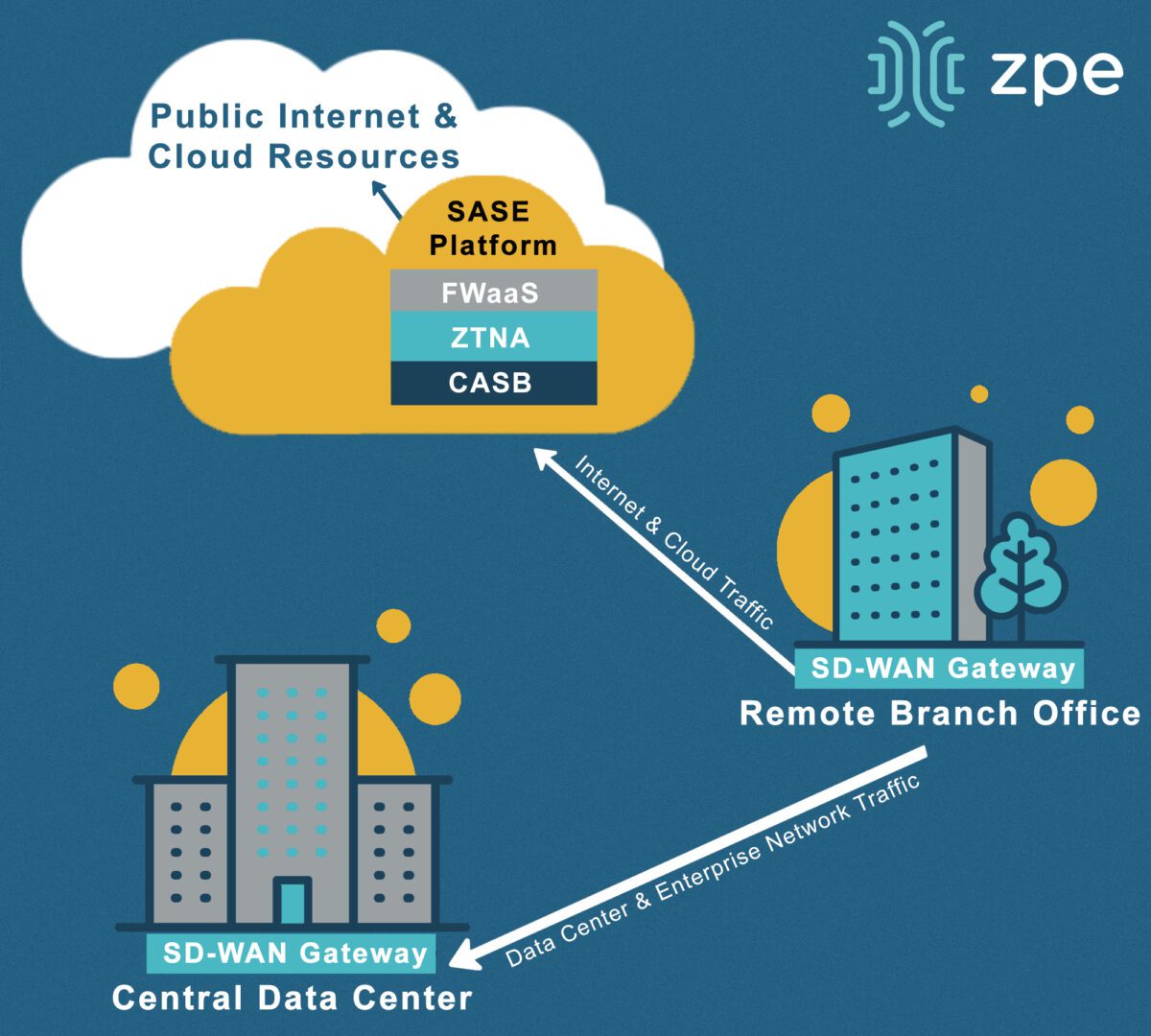
What are the key components of SASE?
To better illustrate how SASE network security works, let’s discuss the five major components of a SASE solution.
1. Software-defined wide area networking (SD-WAN)
SD-WAN separates the control and management processes from your underlying WAN hardware and virtualizes them as software or script-based configurations. It uses intelligent and application-aware routing to directly connect users to cloud and SaaS resources, passing through SASE’s network security stack first. SD-WAN is the networking backbone of SASE because it provides an onramp to cloud-based security services.
2. Cloud access security broker (CASB)
One of the cloud-based security services included in SASE is a cloud access security broker, or CASB. This is essentially a software gatekeeper that sits between the enterprise network and the cloud and ensures that traffic flowing between the two complies with established security policies. A CASB itself is usually a combination of multiple security technologies, including:
- User and entity behavior analytics (UEBA) – Detects unusual account behavior and enforces security policies on traffic flowing between the enterprise and the cloud.
- Cloud application discovery – Identifies cloud applications in use by the enterprise and provides risk analyses of those applications and the users accessing them.
- Data loss prevention (DLP) – Uses established data governance policies to prevent the exfiltration of sensitive and proprietary data.
- Adaptive access control – Analyzes the context of access requests, looking at factors such as user location and the time/date of the request to determine risk.
- Malware detection – Identifies and blocks malicious files and software (i.e., malware) such as viruses and ransomware.
3. Secure web gateway (SWG)
A secure web gateway, or SWG, is a network security service that acts as an intermediary between enterprise users and the web. Whenever a user tries to access a website, they’re passed through the SWG first to ensure that acceptable use policies are applied. The SWG also detects malicious code on websites and provides application controls for web apps like Zoom and Microsoft Teams.
Traditionally, the SWG lives in a box in the data center, but SASE network security uses cloud-based SWG technology instead. That means that remote, web-destined traffic doesn’t need to be backhauled through the data center just to enforce enterprise security and acceptable use policies.
4. Firewall as a Service (FWaaS)
Firewall as a Service, or FWaaS, delivers advanced firewall capabilities as a cloud-based service. In addition to typical stateful firewall features like packet filtering, IP mapping, and network monitoring, FWaaS also uses next-generation firewall technology like deep packet inspection (DPI) and machine-learning traffic analysis. Since the SASE network security stack includes FWaaS, you can ensure the security of remote, cloud-destined traffic without needing to route it through the primary firewall in the data center or deploy security hardware at each remote site.
5. Zero trust network access
Zero trust network access, or ZTNA, provides secure and reliable remote access to enterprise and cloud resources from outside of the enterprise network. Whenever a remote user, device, application, or service attempts to connect to resources within your enterprise or cloud infrastructure, ZTNA verifies their identity and gives them only the specific access they need to perform their function.
ZTNA is more secure than VPNs, which give remote users the same level of access to your network as if they were logging in from the main office. ZTNA prevents remote users from seeing or interacting with any network or cloud resources they haven’t specifically requested access to. This decreases your attack surface if a malicious actor uses a compromised account to access your infrastructure remotely.
SASE network security combines SD-WAN, CASB, SWG, FWaaS, and ZTNA into a single technology stack that optimizes WAN traffic and delivers robust security functionality.
Learn more in Understanding Key SASE Components and Benefits.
What’s the difference between SASE and SSE?
Another popular cloud-based security acronym you may have come across is SSE, or Security Service Edge. SASE and SSE are similar in more than just their names – in fact, SSE is technically a component of SASE. SSE is the security portion of the SASE stack, containing the services listed above such as FWaaS and ZTNA. However, SSE does not include SD-WAN technology, which provides the “access” portion of Secure Access Service Edge.
SSE = Security Service Edge
SASE = Secure Access Service Edge = SSE + SD-WAN
Choosing between SASE and SSE
There are situations in which you may not need the SD-WAN access portion of SASE, in which case an SSE solution would be the most economical choice for network security. SSE is primarily aimed at providing secure connectivity for end users who are working remotely. SASE covers that use case as well, but it also provides security for branch offices and other remote locations with dedicated network hardware.
For example, during the remote work surge at the start of the COVID-19 pandemic, many companies adopted SSE to allow their employees to work remotely. IT teams (or even the end-users themselves) simply installed a client on their laptop or phone, which connected them to the cloud-based SSE stack where security could be enforced. As people return to offices and branches, these companies may opt to install SD-WAN devices in these established remote locations, adding access to the SSE equation and resulting in SASE.
Learn more in SASE vs. Security Service Edge: What’s the Difference?
Who provides SASE and SSE?
Since SASE is just SSE with SD-WAN, that means all SASE vendors are also SSE vendors. The differentiator is that SSE-only vendors don’t have the hardware required to send traffic from remote sites to their cloud-based SSE service. They must rely on third-party SD-WAN on-ramps to SSE, such as ZPE Systems Nodegrid. SASE vendors offer hardware as a key component of their solution but may also have a Switzerland strategy (vendor-neutral) to allow the use of third-party SD-WAN. As an example, here are the top 5 vendors in no particular order:
| SASE | SSE | |
| Cloudflare One | N/A | Yes |
| Palo Alto Prisma Access | Yes | Yes |
| Fortinet FortiSASE | Yes | Yes |
| Zscaler | N/A | Yes |
| Netskope | N/A | Yes |
What are the benefits of SASE network security?
SASE provides numerous networking and security benefits, including:
| Reduced Latency | Streamlined Management | Consistent Security |
| Since remote, cloud-destined traffic doesn’t need to flow through the primary firewall, there are fewer bottlenecks which reduces latency for the entire enterprise. | SASE combines all the security components described above into a single cloud-based service, reducing management complexity even in complex and distributed network environments. | SASE makes it easy to extend enterprise security policies to remote traffic and cloud resources to ensure consistent protection across the entire architecture. |
| Easy Scaling | Improved User Experience | Centralized Orchestration |
| Since SASE resides in the cloud, you can easily scale up or down to meet business requirements without worrying about additional hardware deployments. | SASE provides remote users with fast, seamless, and secure access to enterprise and cloud resources from anywhere in the world. | SASE gives network teams a single pane of glass from which to control both SD-WAN and security, enabling holistic management and centralized automation and orchestration. |
Learn more in The SASE Model: Key Use Cases & Benefits
How to implement SASE
Implementing SASE requires careful planning and a comprehensive understanding of the existing infrastructure, business requirements, and pain points. There are six essential steps involved.
Step 1: Identify your SASE use case, goals, and requirements
The first step in planning a SASE implementation is to identify why your organization needs SASE network security. What problems are you hoping to solve, and what benefits are you hoping to gain? Creating a clearly defined list of goals will help with all the steps that follow.
It’s important to recognize that SASE is a service, which means you consume security processing in somebody else’s cloud instead of handling it with your own infrastructure. For many organizations, this is beneficial because it removes a lot of the responsibility for things like hardware upgrades that are expensive and time-consuming. However, this does mean you lose some control over security and privacy – you don’t necessarily know who has access to sensitive or regulated data, and you can’t force the provider to use the specific technology that’s right for your specific needs. So, before jumping into SASE, it’s important to understand exactly why you’re implementing it, what you’ll gain, and what you’ll lose.
Step 2: Thoroughly assess the existing environment
Next, perform a thorough assessment of the existing network infrastructure and security solutions to determine your organization’s SASE readiness. For example, do you already have SD-WAN implemented at all your remote sites, or will you need to upgrade? Does your SD-WAN solution easily integrate with your chosen SASE or SSE service? If not, you’ll have a harder time with SASE deployment and may have ongoing operational issues. Does your staff have the knowledge, skills, and experience to implement and support SASE, or will they need training? An honest assessment will ensure that you have a complete understanding of what you’ll need to purchase, change, or implement to achieve a successful SASE deployment.
Step 3: Research SASE solutions
Now it’s time to research SASE technology vendors and compare solutions. Use the information gathered in the previous two steps to look for solutions that address your specific problems, goals, and technological gaps. There are a few mature SASE solutions that include both the SD-WAN backbone and the cloud security stack, or you can mix-and-match various networking and security services together to create a fully customized solution. If you take the latter route, you need to ensure that all these services work well together and can be integrated into a centralized management platform.
Cost also needs to be a consideration, as the pricing for SASE solutions is often different from hardware-based security solutions. SASE is usually charged on a per-user basis, which makes it easier to count users for remote access. It’s also common to pay based on bandwidth usage for branches and remote offices. SASE can get much more expensive than purchasing an appliance, so you need to make a value-based calculation to determine whether it’s worthwhile for your organization.
Another thing to consider is that, since SASE is service-based, it’s not very customizable. If your chosen provider only allows a certain number of IP addresses, for instance, you’re unlikely to get extras just because your business is growing. Many SASE solutions also have bandwidth caps that can limit performance, which means you’ll essentially trade one bottleneck (the central firewall) for another (the cloud-based SASE stack). What this all means is that you need to be sure your chosen solution offers you everything you need out of the box with plenty of room for growth, because you may not be able to change things later.
Another option is to start with an open cybersecurity service delivery platform, and then choose the cloud-based security apps that work best for your requirements, essentially building your own SASE solution. If you outgrow one of your apps or run into unexpected limitations, you can swap out that single service instead of needing to replace the entire SASE stack.
Step 4: Train, stage, and test
Once you’ve chosen and purchased your SASE solutions, it’s time to prepare for deployment. This preparation should include staff training on how to configure, use, and support your new technology. It’s also recommended to create a staging and testing environment that’s identical to your production environment, so you can perform thorough integration and user acceptance training before going live. However, many SASE solutions don’t provide the ability to create staging and testing environments unless you purchase multiple instances, which gets expensive and unwieldy. This is another scenario where an open cybersecurity service delivery approach may be a better option than an out-of-the-box SASE solution.
Step 5: Cutover, troubleshoot, and support the SASE deployment
The next step is to go live with your SASE deployment. Major technology deployments like this will always have issues, so make sure you have plans and staff in place to handle user complaints and troubleshoot technical problems. However, it’s important to understand that many SASE issues will be beyond your control to troubleshoot, so you’ll essentially be at the mercy of the SASE vendor to fix many problems. Depending on your vendor, those fixes could take a week or more, during which time you and your customers will be left in the dark. This makes it challenging for organizations to build a resilient network infrastructure that supports uptime SLA requirements. Again, the open platform approach (or “build your own SASE™”) may be a better choice for organizations that want the security benefits of SASE but need more reliability and control over their infrastructure.
Step 6: Monitor, optimize, and evolve
The last step of SASE implementation involves continuously monitoring your deployment to look for issues and identify ways to improve and optimize. In addition, your business requirements will likely change over time, as will the features and technologies available in the SASE landscape. That means you can continuously evolve your SASE deployment to maintain optimal performance and protection.
Learn more in SASE Implementation: A Step-by-Step Guide for Businesses.
Build your own SASETM with Nodegrid
All of the current SASE offerings have challenges and limitations, while the solutions are still evolving and changing. For enterprise customers, that means there will be potential issues, such as initial deployment hiccups, or outgrowing the capabilities of the SASE service. The Nodegrid platform from ZPE Systems can help organizations overcome these issues and simplify SASE management.
Nodegrid serial consoles and branch gateway routers provide robust, secure, Gen 3 out-of-band (OOB) management capabilities. These boxes can be deployed alongside physical SASE or SD-WAN appliances to ensure 24/7 remote management access even during outages and service interruptions. Nodegrid’s redundant network interfaces (which include 5G options) provide both OOB and failover capabilities, so during an ISP or WAN outage, for example, you can keep your SASE/SD-WAN appliance online until service is restored.
Nodegrid boxes are also completely vendor-neutral, which means you can use them to directly host your SD-WAN, SASE, or SSE applications to converge and simplify your branch infrastructure. That means you can pick and choose the cloud-based security services that best serve your requirements and build your own SASETM, without needing to install and manage a bunch of different devices. Nodegrid’s converged branch gateway solutions combine many different networking capabilities into a single device, including routing, switching, and OOB serial console management, further simplifying branch network management.
Plus, Nodegrid provides a single, unified, vendor-neutral orchestration platform from which you can control the entire edge networking and security architecture. Nodegrid’s platform can monitor, deploy, and manage any SASE solution that’s hosted on or connected to a Nodegrid device. This gives organizations a much greater degree of control over both their SASE security services and their SD-WAN infrastructure, so they can maintain data privacy and meet SLAs.
