What Is Security Service Edge (SSE)? Everything You Need to Know
What is security service edge (SSE)? It’s an emerging cybersecurity methodology introduced by Gartner in their 2021 Hype Cycle. SSE combines cloud-centric security technologies such as zero trust network access (ZTNA), secure web gateway (SWG), cloud access security broker (CASB), and firewall as a service (FWaaS) to provide secure remote access to cloud and enterprise resources.
But what is SSE exactly? How is it different from similar security concepts such as secure access service edge (SASE)? Here is everything you need to know about security service edge.
What is security service edge (SSE)?
Essentially, SSE combines and integrates multiple cloud-based security technologies into a single solution for securing your network edge. A network edge consists of any systems that are not part of the main data center or enterprise network, such as branch offices or retail stores. Historically, IT teams have had to strike a difficult balance between providing convenient, high-performance remote access to critical resources and securing those remote connections. SSE provides the security part of the equation while integrating with SD-WAN technologies that provide high-performance remote access.
Security service edge can use a variety of cloud-based security technologies. Still, four of the most common—and most effective—are ZTNA, SWG, CASB, and FWaaS. Let’s take a closer look at how each of these components works.
Zero trust network access (ZTNA)
Zero trust network access, or ZTNA, is a cloud security service that applies zero trust security principles to remote traffic. Whenever a remote network entity—a user, device, application, etc.—attempts to access a resource within an enterprise or cloud infrastructure, ZTNA verifies their identity and gives them limited access to the specific resource in question.
With ZTNA, the remote user can’t see or interact with anything else on the network without being verified again, limiting their lateral movement. This might sound like a bug, but it’s a beneficial feature. Imagine a hacker compromises that remote account. The damage the hacker could do to your infrastructure will be limited to the few systems they gained access to through their remote ZTNA session. Every time they need to reverify their identity, they’re increasing their chances of getting caught.
ZTNA uses adaptive, context-based access control policies to determine the active risk of allowing a remote account to access a resource. You can create ZTNA policies to analyze factors such as the user or device’s location, the time and date of the request, and the user’s previous activity to determine whether a request is legitimate. For example, you can create location-based policies that block remote access if a user or device leaves a certain geographic area.
ZTNA gives branch and remote users access to the resources they need while isolating them from the enterprise network and continuously verifying their identities. When combined with other SSE technologies, ZTNA allows you to keep the edge secure without sacrificing performance.
Secure web gateway (SWG)
A secure web gateway, or SWG, acts as an intermediary between users and the web. Before a user can access a website, they’re passed through the SWG first—where your enterprise’s acceptable use policies are applied to prevent them from accessing restricted websites. The SWG also provides malicious code detection and application controls for web apps such as Zoom and Teams.
Traditionally, a secure web gateway was an appliance in the data center. If you wanted to protect the remote, web-destined traffic, you would need to backhaul it through the SWG at the data center, causing bottlenecks and slowing down the network.
As part of an SSE solution, the SWG is cloud-based, which means your remote and branch office traffic can altogether bypass the enterprise data center. Instead, that traffic is routed through the cloud SWG, so you can enforce the same security and acceptable use policies without impacting the enterprise network’s performance.
Cloud access security broker (CASB)
A cloud access security broker, or CASB, is like a software gatekeeper between an on-premise network and a cloud infrastructure that enforces enterprise security policies on traffic between the two. The CASB performs numerous functions, including:
Cloud application discovery—identifying all the cloud applications your enterprise is using and analyzing which apps and users are high-risk
Data loss prevention (DLP)—using your enterprise’s data governance policies to prevent the exfiltration of sensitive and proprietary data
User and entity behavior analytics (UEBA)—monitoring traffic between your enterprise and cloud to detect unusual behavior and enforce security policies
Malware detection—using firewall technology to monitor traffic, identify malware and block it from entering the enterprise network
Access control—analyzing the context of access requests to determine risk before allowing access
CASBs enhance SSE solutions by providing cross-platform security policy management and enforcement. That means you can use the SSE CASB to apply and enforce enterprise policies across your entire cloud infrastructure from one unified control panel.
Firewall as a service (FWaaS)
Firewall as a service, or FWaaS, rolls up firewall technology into a cloud-based service that can protect cloud infrastructure without needing to route traffic through a physical appliance at a data center. FWaaS solutions provide all the typical stateful firewall features such as URL filtering, intrusion detection and prevention, network monitoring, and IP mapping. It also comes with advanced, next-generation firewall (NGF) capabilities, including:
Deep packet inspection (DPI)
Traditional firewalls inspect the header of all data packets for information like the source and destination IP address to determine whether they’re malicious. DPI goes even further by analyzing the entire range of metadata and data connected with every packet that passes through the FWaaS.
Machine learning
Firewall threat detection is traditionally signature-based, which means it relies on a database of known threats that the firewall can refer to. If a malicious packet or program doesn’t match anything in that database—for instance, because it’s a zero-day exploit that has never been used or encountered before—the firewall will let it through. FWaaS uses machine learning to analyze network traffic, user behavior, and other data to look for indications of a breach that may not match up with established patterns in a database. This allows the FWaaS solution to detect potential threats with greater accuracy than signature-based systems.
FWaaS solutions for SSE are easily scalable and customizable; consequently, you can add or subtract features or easily protect new branch locations and cloud services with the click of a button. You get all the functionality of a next-generation firewall but without the hassle of deploying and managing hardware at every branch office or the performance issues that come from backhauling remote traffic through a single appliance at the primary data center.
Security service edge (SSE) combines multiple cloud security technologies that protect your edge without affecting the network performance or enterprise productivity. Zero trust network access, secure web gateways, cloud access security brokers, and firewall as a service are four of the key components of most SSE implementations.
What’s the difference between SSE and SASE?
SSE shares many characteristics with the cloud security methodology called secure access service edge, or SASE. This has led to some confusion over the difference between SSE and SASE. The truth is, they aren’t mutually exclusive.
Remember, SSE is the combination of security controls that protects your network edge. Still, it does not include the technology to connect the edge to an enterprise and cloud infrastructure or cloud security services. SASE is security service edge, but also includes access technology, which turns the security service edge into a secure access service edge.
SASE combines SSE’s cloud security services with software-defined wide area network (or SD-WAN) technology. SD-WAN uses intelligent and application-aware routing to connect remote users and branch offices directly and securely to the cloud, SaaS, and SSE resources. For example, you can route remote traffic through cloud-based SWG rather than backhauling it through the enterprise network.
SD-WAN separates the control and management processes from an underlying WAN hardware and makes them available as software. Then, you can layer SSE’s cloud-based security stack on top of that SD-WAN backbone. When combining security service edge with SD-WAN, the result is SASE.
How can my enterprise implement SSE?
SSE is technically a cybersecurity methodology, not a technology solution. That means you can mix-and-match providers for ZTNA, FWaaS, and other key components for achieving SSE.
There are also SSE vendors who roll up all these cloud security technologies into a unified solution. Some examples include Palo Alto Prisma Access and VMWare. You might notice that both of these solutions are marketed as complete SASE platforms, but that’s not entirely accurate, because neither of them provides the access part of the equation.
That’s why you need an SD-WAN solution that integrates with your SSE platform, like ZPE Systems’ Nodegrid.
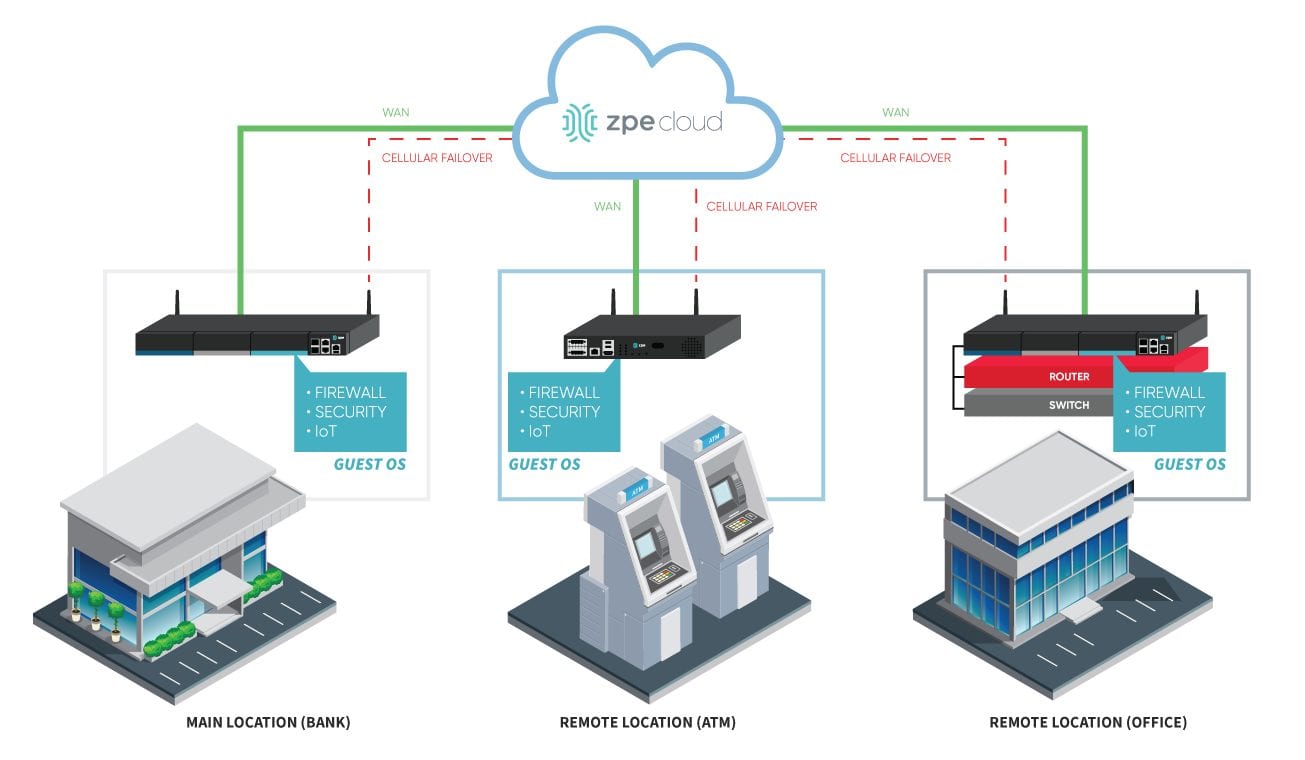
How does Nodegrid bring access to SSE?
The Nodegrid family of hardware and software provides SD-WAN solutions to fit various use cases and business needs.
For example, you can install Nodegrid Network Edge Routers in your branch offices, retail stores, and other remote locations that need SD-WAN access. These powerful devices provide remote users with secure and reliable connections to enterprise and cloud resources, in addition to enabling access to security service edge solutions.
Recommended: Nodegrid Net Services Router—an all-in-one solution with a modular design so you can create a custom solution to suit your SD-WAN and branch infrastructure management needs
Learn more about Nodegrid Gate Services Router—Nodegrid Bold Services Router —Nodegrid Link Services Router
Discover even more about security service edge (SSE) with ZPE Nodegrid
Security service edge (SSE) is a collection of integrated, cloud-based security technologies to protect your network edge. SSE combines security controls such as zero-trust network access (ZTNA), secure web gateway (SWG), cloud access security broker (CASB), and firewall as a service (FWaaS). When you integrate this cloud-based security stack with an SD-WAN solution like ZPE Nodegrid, you end up with SASE or secure access service edge.
For answers to more questions like, what is security service edge (SSE)? Reach out to ZPE Systems online or call 1-844-4ZPE-SYS.
