Do you know what to avoid when choosing a VPN? These virtual private networks are commonly promoted as the key to online privacy and security, as they employ dedicated point-to-point connections, tunneling protocols, and encryption. With the sharp increase in distributed workforces and Ransomware outbreaks during 2020, it’s no wonder why consumers and enterprises alike showed significantly more interest in VPNs last year.
But before we dive into what you should avoid when choosing a VPN, here’s a brief refresher on this decades-old technology.
What is a VPN, and what is it used for?
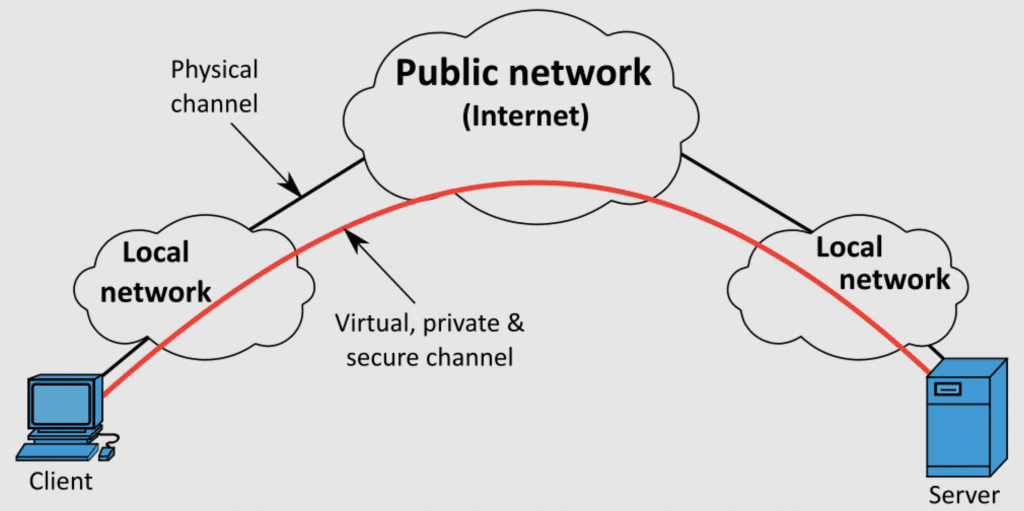
A VPN, or virtual private network, is a private network that allows users to send and receive data over a public or shared network, without having to establish a physical connection with the private network. Essentially, a VPN uses a dedicated tunnel that connects through the Internet and to a private network, such as a company’s intranet.
Here’s an example:
The year is 2020, and you’ve just been sent home to work remotely. On your personal computer, you open a browser tab and try to access your everyday business applications, but to no avail. Then you remember the VPN instructions sitting in your inbox. You use them to set up your computer with a VPN configuration, which includes selecting the appropriate protocol and entering your authentication credentials. Once you finish, you turn on the VPN connection, and suddenly you gain access to your applications as if you were sitting at the office.
Of course, there’s more work involved when setting up on the business side, such as selecting the right services and/or components. But once you have these in place, you can start configuring and using your VPN for access to the resources you need.
Enterprises commonly use VPNs to allow their workers to remotely access their private networks and their connected resources, as in the example above. For enterprise IT staff, such as a data center network technician, a VPN gives them access to important data center management tools without exposing their actions or data to the unsecured public internet.
Enterprises also use VPNs to connect multiple networks or offices to each other and/or to a data center location. This is called a site-to-site configuration. Site-to-site configurations can involve multiple sites owned by one organization, called intranet site-to-site; or multiple sites owned by multiple organizations, called extranet site-to-site.
Enterprises are drawn to using VPNs because they can provide several advantages. They offer a convenient way for staff to remotely access resources, but also hide users’ IP addresses and can encrypt sensitive data for added security.
However you should be aware that not all VPN services are created equal. It’s really quite the opposite, so whether you already use one or are ready to shop around, keep in mind these four things to avoid when choosing a VPN.
4 things to avoid when choosing a VPN
False sense of security
Aside from providing remote access capabilities, a VPN’s purpose is to help you communicate securely without exposing your data to public or shared networks. However, VPN (as its name implies) is about privacy, not security. Many VPN service providers give you a false sense of security when in fact your data can still contain malware and spread to your peers. Many VPN vendors also leak and log your data. Aside from connection logs, which typically contain usage data used for optimizing the provider’s operations, there are IP address and traffic logs that some providers employ. Data like your IP address, browsing history, and even recent online purchases can be stored in these logs, which means they could potentially be sold to advertisers, or worse — attackers. When you’re considering a VPN provider, be sure to read the fine print in their service agreement and see whether they log IP addresses, usage, traffic, or other sensitive information.
Slow speeds
Imagine your data center technician is trying to resolve a critical issue and uphold your stringent service level agreement (SLA). Recent social distancing guidelines restrict the technician from resolving the issue on site, so they must connect via VPN for remote troubleshooting. The problem is, it’s peak usage time and the public network is overloaded. What would have been a five-minute job turns into an hour-long waiting game punctuated by unresponsive experiences.
Slow speeds are common with VPNs. That’s because data packets need to be re-routed and encrypted through a VPN server. The farther this server is located from your users, the longer it will take for your data to reach this server. This slowness is exacerbated when you opt for a free VPN service or plan, as these likely don’t offer or prioritize high-speed connections. When considering a VPN, be sure to get a free trial that will enable you to check your speeds.
Potential abuse
If instead of setting up your own VPN architecture, you opt to use a VPN service, keep in mind that there are many providers on the market. And if you choose a provider whose services are operated and maintained in a country where regulation is minimal, such as in China or Russia, you need to understand that your data is vulnerable to abuse. Providers who offer bulletproof hosting (BPH) services in foreign countries, for example, often serve as safe havens for criminals and cyberattackers. Because these operations are typically well insulated against judicial action from governing bodies in the U.S. and other western nations, there’s no legal remedy for customers who suffer from abuse. When considering a VPN service, always choose a trusted provider who operates in a well-regulated country, so you can have the confidence that your data won’t be abused.
Potential abuse
If instead of setting up your own VPN architecture, you opt to use a VPN service, keep in mind that there are many providers on the market. And if you choose a provider whose services are operated and maintained in a country where regulation is minimal, such as in China or Russia, you need to understand that your data is vulnerable to abuse. Providers who offer bulletproof hosting (BPH) services in foreign countries, for example, often serve as safe havens for criminals and cyberattackers. Because these operations are typically well insulated against judicial action from governing bodies in the U.S. and other western nations, there’s no legal remedy for customers who suffer from abuse. When considering a VPN service, always choose a trusted provider who operates in a well-regulated country, so you can have the confidence that your data won’t be abused.
All for the money
This somewhat reiterates the first point above, but can’t be understated. The fact is that with thousands of VPN providers to choose from, many exist solely to make money.
Trusted providers may use RAM-based servers that don’t have the ability to log any of your data. To further protect you, they typically encrypt your traffic using 256-bit encryption or higher, which makes it impossible to hack your sensitive information. These are just a couple features that reliable VPN services provide in order to keep your data private and secure, but unfortunately there are many providers who lack these basic components.
Some providers turn on logs temporarily to identify suspicious users. This can be beneficial in preventing abuse, cybercrime, and illegal activities, but also puts the average user’s data at risk, especially if the provider retains all logged data. Some of the worst VPN providers don’t even employ VPN servers, and instead use peer-to-peer connections, which forces users to share bandwidth and use each other’s IP addresses. Insecure practices like these show that companies don’t truly have their customers’ best interests in mind, and are instead focused mostly on minimizing infrastructure costs in order to make more money.
When choosing a VPN, opt for a trusted provider who can provide secure service to your remote users as well as your branch office employees. Or simply deploy ZPE Systems’ Nodegrid portfolio of flexible branch routers, which serve as your on-ramp to VPN-as-a-service. These make it easy to secure your connections, because you can deploy virtual machines directly on Nodegrid devices and run apps from security leaders like Palo Alto Networks or Fortinet. You could also use Nodegrid routers simply as your access to Secure Service Edge (SSE) providers like Zscaler or CloudFlare, and easily build your Secure Access Service Edge architecture.
Don’t fall into VPN traps
Your IT infrastructure’s integrity is a top priority, especially with cybercrime on the rise and expected to cost $10.5 trillion by 2025. Your staff need secure remote connectivity to maintain network and business operations. But with so many options available, it can be difficult to choose the best approach — VPN or otherwise.
To make sure you don’t expose your staff or your business to unsafe services, contact one of our experts today. We can show you the most secure way to gain remote access to your IT infrastructure, with or without using a VPN! You can take a free tour of ZPE Cloud, which gives you VPN-less access to your distributed infrastructure, and provides completely secure, end-to-end encryption to and from the cloud. Get in touch for a first-hand look.