ShellShock UNIX Bash Bug – Introduction
You’ve heard about the ShellShock Unix Bash “ghost user” exploit at least 13 times by now. This discovery of a hurtful secret within a deep, trusted friendship (ubiquitous reliance upon generally stable Open Source software) reminds us that IT Security is like any long-term relationship – constantly evolving.
Did you and your colleagues have a fire drill this week reacting to the ShellShock news? If it felt like one over the past week, where everybody ran around patching servers and semi-anxiously diagnosed what else might be vulnerable, then you’ve come to the right triage center. ZPE Systems provides a solution which helps sysadmins avoid the ShellShock bug’s malicious ghost users in the first place. Feeling lucky?
Lucky or Forward Thinking?
Enterprise INFOSEC admins who already had NodeGrid Manager installed before this latest problem merely had to patch one user portal. After this, said admins were able to leisurely patch the thousands of systems safely nestled behind NodeGrid Manager at their own pace. In fact, they could wait until Christmas and feel quite zen, although we don’t recommend it. Just because you can do something doesn’t mean you should. Our existing customers are already benefiting from NodeGrid’s intrinsic built-in Firewall capabilities.
This “Firewall capability” of NodeGrid Manager isn’t something we’ve trumpeted much before. By placing NodeGrid in front of all your devices, you effectively firewall user access to your varied, globally distributed IT assets. Widespread damage by users is highly reduced in a NodeGrid environment. Upon login to NodeGrid, users are authenticated against your existing enterprise AD/LDAP database for access. Then, users are further authorized based on their existing profiles with specific access rights to specific IT assets. No user will have direct access to every shell in the house without your explicit authorization.
Your Way, the Right Way
In this way, Joe, a senior engineer within the IT Security team, only has access to specific switches, routers, servers and smart PDU infrastructure to which he is authorized. Joe’s world consists of only those machines to which he is authorized access to from within NodeGrid. He won’t have access to or even see Marketing VMs, Development storage and server hardware or Finance servers and switches. Joe is protected, and his colleagues in other departments are also protected.
Another Use Case:
- Samuel’s “internal and trusted” corporate Dell laptop has been hacked/infected by a Shellshock type attack.
- Sam’s laptop tries to connect to NodeGrid without encrypted user credentials – is unceremoniously blocked – and can’t hack the rest of the network.
- Multiple layers of NodeGrid security prevent collateral damage.
NodeGrid can help to improve the security and reduce the exposure to vulnerabilities by allowing network separation between critical systems and the users. NodeGrid’s “FireTrail” secure tunneling through Firewalls feature explicitly limits IT asset exposure to outside elements. Users receive secure locked-down access to authorized devices behind sensitive Firewalls without ever needing to know Firewall credentials. Deploying NodeGrid is almost like having two extra Firewalls.
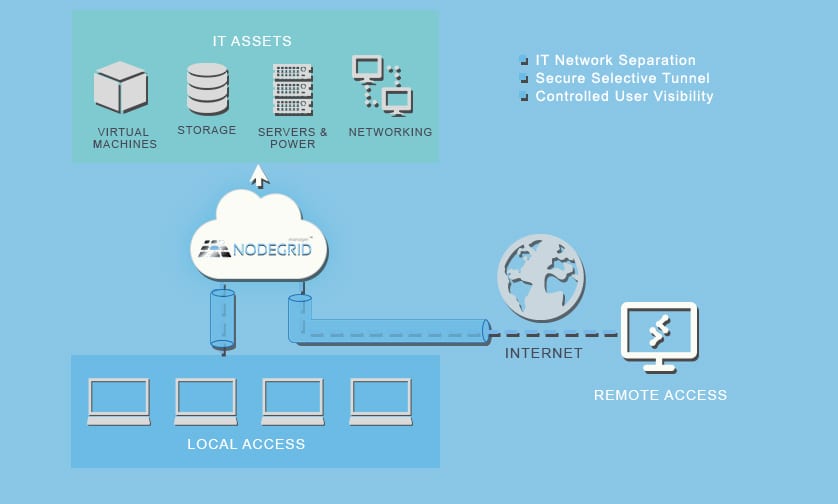
Illustration of NodeGrid’s FireTrail secure tunneling IT asset protection feature.
In a NodeGrid managed device scenario, there is no direct connection to the bash of the target managed devices. NodeGrid works as the entry point, redirecting authorized users to a secondary network connection established exclusively between NodeGrid and your target managed devices. Also, by limiting the access availability to the serial console port of managed devices or access only within the management network (not production), sysadmins can improve the security of critical devices.
Get the Protection You Need Right Now
If you’d like to be doubly protected from future ShellShock bash bug type attacks, or any other attacks on your infrastructure based upon compromised user logins or exposed IT assets, contact us today. As you know, NodeGrid can act as a second firewall, or moat, around your IT castle — either in front of your existing firewall appliance or behind it.
In celebration of Halloween this month, we continue to offer terrifyingly good weekly demo sessions in person and via Webex. Register now to watch an overview of NodeGrid and learn how it can help save your IT bacon. You’re also welcome to download an evaluation copy of NodeGrid.
We look forward to helping enterprises and the global Internet become more secure and stable places to conduct business.
Warm wishes,
Kenneth Ott
Partnership Development
Kenneth Ott is Partnerships Manager at ZPE Systems and began using shell accounts in the late ’90s. He conducts initial consultations with organizations seeking simplified IT infrastructure management options. Outside of work, Kenneth enjoys hiking and camping throughout California.
