
Security Service Edge. Is it just another fancy networking term? After all, we’ve already got SASE (Secure Access Service Edge), so why throw another buzzword into the mix?
The truth is, there’s a big difference between Security Service Edge (SSE) and SASE. SSE is a foundational element of SASE, but there’s another necessary component you need to be aware of. In this article, we’ll break down the differences between these two acronyms so you can understand how to achieve better security for your distributed users and devices.
But first, let’s quickly recap why networking and security have become decentralized.
Security Service Edge: An evolving need
The modern workforce is increasingly distributed. In fact, Gartner research shows that demand for remote work will increase 30% by 2030, as Gen Z fully enters the workforce. Another factor is the ongoing coronavirus pandemic, which has forced companies worldwide to accommodate off-site staff.
But the need for distributed networking goes back much earlier than the previous 18 months.
Connectivity and network architectures used to be simple. In the 1990s and 2000s, companies centralized data in the data center, connected branch offices to the data center, and set up simple security measures in between. Most staff worked from the office, which made it easy to provide secure access to and from these enterprise locations and resources.
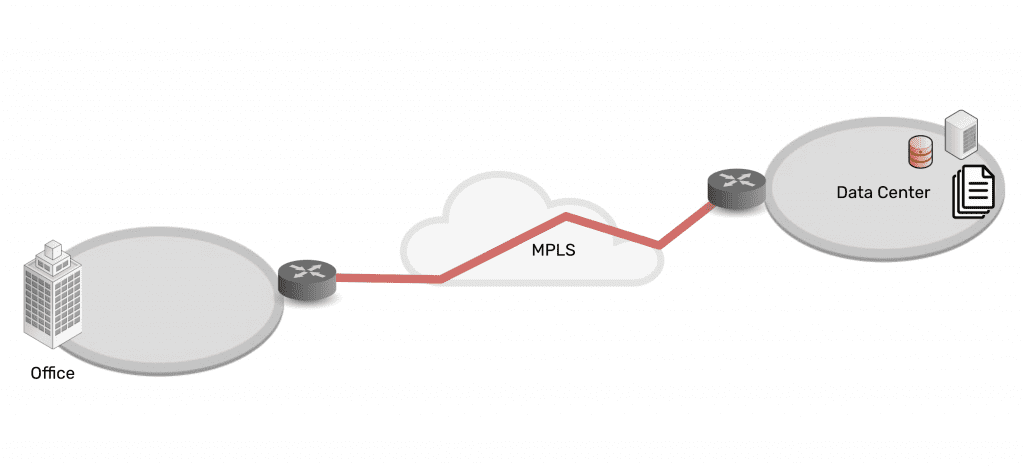
As technologies advanced, companies and their employees discovered that it was becoming easier to work outside of the office. Cloud, SaaS, and edge offerings emerged to create a hybrid infrastructure, as everything moved from being centralized to highly distributed. Now data, security, networking, and computing are everywhere and comprise a complex web of services — owned by enterprises themselves as well as third parties. Securing it all has been an impossible feat for more than a decade.
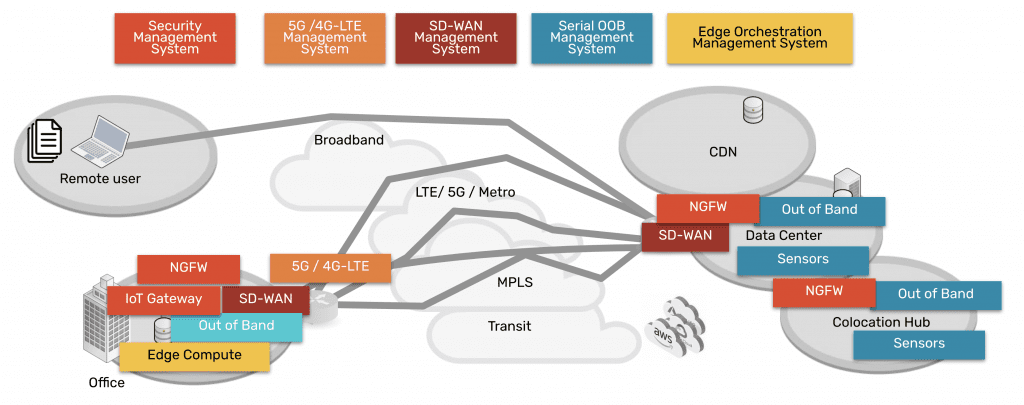
Fortunately, Security Service Edge and SASE are models that can address this challenge.
SASE vs Security Service Edge (SSE)
Security Service Edge is a main component of SASE. In the simplest terms, SASE is the architecture that organizations strive to build. It involves delivering networking and security via the cloud, directly to the end user, device, office, etc. instead of having to backhaul through the company’s data center. Aside from SSE, the other main component of SASE is the access portion, which allows the edge services to be deployed and managed. This access portion includes the physical hardware required to connect ‘network’ the edges and services.
Therefore, SASE breaks down into two main components:
- Security Service Edge, and
- Access
Keep reading for a detailed explanation of each and why they have been separated out into two pieces now.
Security Service Edge
Security Service Edge (SSE) is the security component of SASE. As Gartner states, SSE ensures secure access to the web, cloud services, and applications. SSE is delivered via the cloud and offers several capabilities, including threat protection, security monitoring, and data security.
Security Service Edge capabilities are available from companies who provide NGFWs (next generation firewalls), SWGs (secure web gateways), and CASBs (cloud access security brokers).
- NGFWs: Next generation firewalls are implemented to not only secure networking components and services, but also to protect against modern threats that exploit weaknesses in applications. This type of service secures all the traffic even traffic that’s UDP and also non web based applications including malware exploits.
- SWGs: Secure web gateways are self explanatory. They are placed between the user and the web, serving as a gateway that provides secure access to the web. Basic functions of SWGs include blocking access to certain websites, preventing unauthorized transfers of data, and inspecting for malicious content. As its name implies this type of service is limited to web traffic and is used in specific use cases.
- CASBs: Cloud access security brokers are software that sit between cloud users and cloud applications, to monitor activity and enforce security policies. This software keeps a close eye on data as it moves between cloud environments, SaaS, and users, and enforces security policies to block malware, protect sensitive data, and maintain compliance. This type of service also has a specific use case of only examining specific cloud applications as its name suggests.
Access for Security Service Edge
In order to use the capabilities of Security Service Edge, you need the physical hardware to deploy services at your locations. This hardware is the access component, and includes SD-WAN capabilities. When deployed, it connects your location to a variety of services (NGFWs, SWGs, CASBs mentioned above) in order to make those services available to your location.
SASE = Security Service Edge + Access
A simple way to think about the SASE concept and its components is to imagine a skyscraper.
Imagine SSE capabilities live in the clouds, and you’d like to bring them down to your enterprise. You’ve got the blueprints to build a skyscraper (SASE) that can connect you to these cloud-based capabilities. But before you can do any of that, you need a sturdy foundation (the access portion) on which to build it all. In other words, your investment in cloud services needs a solid access onramp to those services.
With the right access component, your employees can shuffle in and out of your skyscraper, and easily perform their job functions using SSE capabilities in the cloud. And if you deploy a more robust access solution such as ZPE Systems’ Nodegrid, you’ll be able to maintain your SASE architecture no matter how the clouds change.
How to implement SASE: Focus on Access
When you’re considering implementing SASE architecture, you might be inclined to go to a SASE company to buy everything. But Gartner states that companies that offer the two segments have more mature offerings.
Therefore, you should focus on purchasing the right solution for the access portion, since it serves as the foundation of your infrastructure at the edge, and then marry this to the right SSE solution for your company. This separation of vendors gives you flexibility to manage several IT systems, and eliminates vendor tie in.
Nodegrid puts the Access in SASE
The Nodegrid SR family of edge routers serves as the access portion in your SASE architecture. A single Nodegrid SR device is a powerful, cost-effective solution to connecting sites to Security Service Edge providers.
The onboard Intel CPU and Linux-based Nodegrid OS offer speed and flexibility. Orchestrate freely across vendors to activate service licenses, spin up VMs, and get your SSE solutions up and running automatically. Additional RAM and storage also help you deploy edge computing for data thinning, de-duplication, monitoring, and other edge workloads.
On top of this, Nodegrid gives you out-of-band management capabilities so you can remotely manage your SASE architecture from anywhere. If you need to optimize bandwidth, investigate data logs for security, or simply power cycle an edge device, you don’t have to get out of your pajamas. Nodegrid gives you secure access to everything via your web browser.
To summarize, the reason SSE has been separated from SASE is that many SD-WAN vendors began to confuse the market by advertising that they offered SASE. This prompted Gartner to point out that there are security-savvy companies that give you more mature security solutions, and to consider such solutions from vendors like zScaler, Netskope, and Acreto, for example. Regarding the Access component, vendors like ZPE Systems provide more capable and robust solutions for connectivity to cloud services, when compared to SD-WAN companies that claim to offer SASE.
Don’t miss out on valuable SSE content. Make sure to sign up for our newsletter using the form below.
If you have questions or would like to speak with an expert, feel free to contact us.
