Modern network management involves a wide variety of distributed technologies. Because of this, enterprises have progressively moved towards the Security Access Service Edge (SASE) model to provide remote users with secure cloud-based services. Even though these services came together to form a comprehensive network and security stack, several providers made inaccurate claims that their products offered an all-in-one solution.
Consequently, the SASE model has undergone a rebranding. The new and improved focus on Security Service Edge (SSE) programs has confused those interested in transitioning to a remote structure. This article will help you understand SSE, its components, and how SSE differs from SASE.
In addition, we will discuss how you can implement SSE into networks and start your journey towards the SSE architecture suited for your enterprise.
What is Security Service Edge (SSE)?
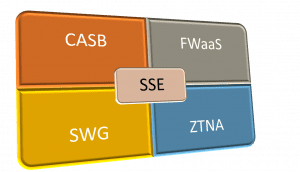
SSE is a combination of cloud-based security technologies designed to protect your edge network. With all its programs combined, it forms half of the SASE framework. SSE provides cloud-based security and SaaS programs to the edge network perimeter, allowing remote users to access these services without being in the office.
What are the key SSE components?
To understand how SSE works, you need to understand its components and how they come together to form a more cohesive edge computing architecture.
Let’s dive deeper into each SSE component to understand them better.
Zero Trust Network Access (ZTNA)
Zero trust is one of the most important aspects of a robust SSE architecture. Zero trust is a security framework that operates on the central principle that “no device is trustworthy.” This includes devices within a company’s perimeter, which traditional “castle and moat” models ignore.
While zero trust exists as a general security architecture involving a variety of principles, zero trust network access (ZTNA) is the practice of applying zero trust principles to a comprehensive SSE security stack. When applied correctly, ZTNA uses features such as:
- Uniform security policies
- Identity-based authentication
- Centralized visibility
- Granular access
- Threat monitoring following access
ZTNA emphasizes “granular” access since it limits who can access and to what. In this way, it helps prevent the possibility of cyberattacks and minimizes their effects if they happen.
Cloud Access Security Broker (CASB)
CASB works as a form of cloud-based security. Whereas ZTNA focuses on the granular task of monitoring individual points of access, CASB focuses on tracking data transference from one cloud environment to another. When we talk about CASB, it is essential to specify that we mean integrated CASB instead of traditional CASB, which only offers piecemeal security protocols that solely cover data already in the cloud.
Integrated CASB uses an API-based security system that communicates between various SaaS applications commonly used by SSE networks. The significant advantage of taking this approach towards cloud security is updating and automatically possessing integration capabilities as new SaaS programs are introduced. With the rise of SaaS usage by large and small enterprises alike, CASB is undoubtedly a central need for any strong SSE network.
Secure Web Gateway (SWG)
As SSE networks exist almost entirely on the premise of edge computing, it makes sense that users want to emphasize a well-secured access terminal. The purpose of SWG is to provide this terminal in a remote location that exists on the edge of the security perimeter. Secure web gateways protect user access by:
- Limiting website access once accessed
- Enforcing security policies
- Protecting data transfer
By limiting and restricting access, remote users will be less likely to access materials that could contain malware or ransomware, for which Palo Alto cites the ransom amounts having climbed by 82% in the first half of 2020. SWG makes up an integral part of the SSE security stack, providing the access terminal through which users begin to interact with the other programs.
Firewall as a Service (FWaaS)
FWaaS uses a SaaS service structure to provide firewall services for clients. FWaaS offers large and small enterprises with cloud-based firewalls, which they can customize to work around company applications or cloud-based services; without needing to route traffic through a physical firewall appliance at a data center.
The main advantage of FWaaS is adaptability—since it is constantly updated to integrate with new and existing services commonly used in SSE networks. With FWaaS, you avoid all the hassle of deploying and managing hardware at every branch office or the performance issues that come from backhauling remote traffic through a single appliance at the primary data center.
SSE vs. SASE: What is the Difference?
The transition to SSE networks might seem confusing for network administrators who have been working on the SASE model in recent years. This is an understandable confusion, but the differences between them are significant and merit some studies. The basic breakdown is as follows:
- SASE = Secure Access Service Edge
- SSE = Security Service Edge
This distinction seems odd on its face. The difference between the two is just the element of access. That essentially means SASE=SSE+Access. The access portion of SASE is also a collection of several components itself. SD-WAN, routers, and gateway all play essential roles in granting remote users access to the programs offered by the SSE stack. Together, the two create the comprehensive SASE architecture, which has become the benchmark for remote access over the last few years.
Why Does “Access” Matter as an SSE Component?
It’s easy to look at the equation above and think that enterprises are losing something with the move to SSE, since SASE seems to have something (access) that SSE does not. This is why it’s important to remember that SASE is a collection of programs and is not offered as an all-in-one system anywhere. This has not stopped various SD-WAN network providers from claiming to provide a SASE connection, confusing the market and necessitating the move in distinction to SSE.
What SSE components can do for your organization
Whether you plan on switching over to an SSE network entirely, the fact remains that many SSE components are good tools to have in your security stack. Even if your company has not gone remote and operates using a traditional “castle and moat” model, things like ZTNA, CASB, and SWG still have a lot to offer in making your business more secure.
For enterprises wishing to switch over to a SASE framework, ZPE’s Nodegrid series of routers offers options for both SD-WAN solutions and Zero Trust Network Access, making it the perfect start on your SASE journey.
Want to learn more?
Contact us for more information on how we can help get your enterprise on the right track.