“Zero trust” is a security methodology designed to reduce the risk of attack through network segmentation, granular access policies, and advanced security technologies. Many organizations use zero trust to protect their IT networks, but it’s just as critical to the safeguarding of operational technology. This post defines zero trust security before explaining how to implement zero trust for OT.
| Table of Contents: |
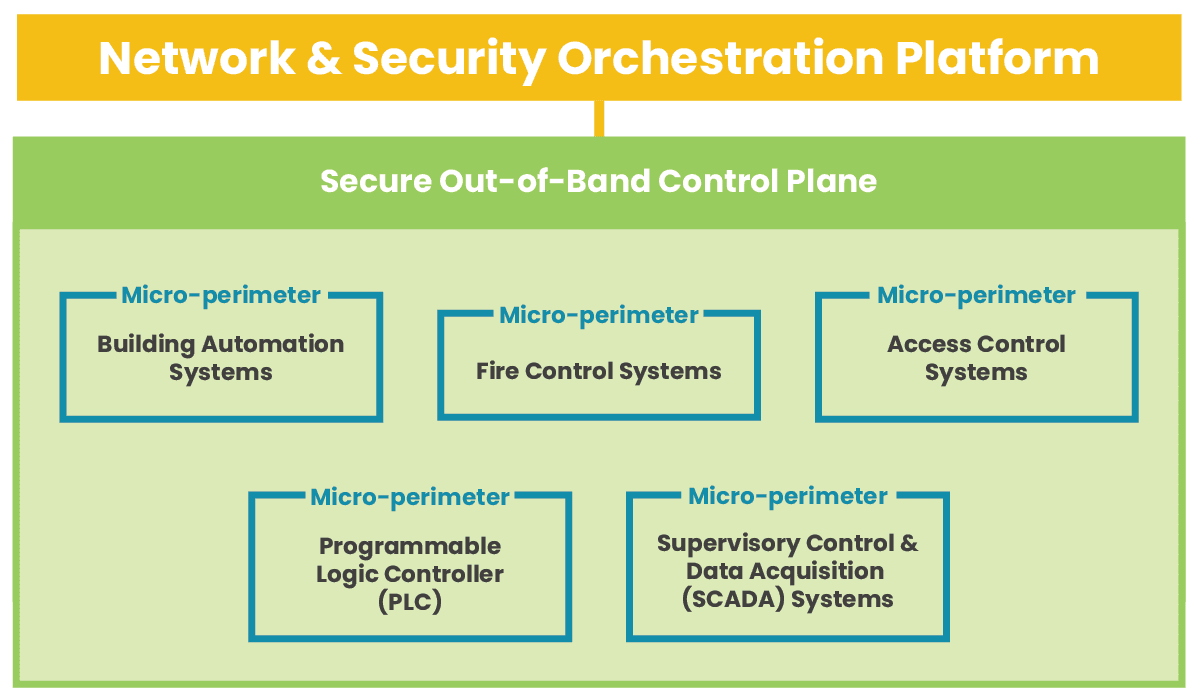
What is zero trust for OT?
According to recent research by Barracuda Networks, more than 90 percent of manufacturing organizations saw cyberattacks hit their production or energy supply in 2021 alone. OT is a frequent target because of how devastating an attack can be on business operations and because it often lacks the same security policies and controls that protect IT infrastructure. To solve this problem, teams need to apply zero trust security principles, policies, and technology to their OT networks. The zero trust security methodology follows the motto “never trust, always verify.” That means operating under the assumption that no users or devices should be trusted, even if they’re logging in from within the main office. Achieving a zero-trust architecture means segmenting IT and OT networks and creating micro-perimeters of highly specific security policies and controls to protect each segment. Zero trust often uses advanced security technologies like AIOps and machine learning to enforce those policies, identify subtle signs of compromise, and quickly resolve security incidents.
|
How to implement zero trust for OT
Let’s discuss the requirements and best practices for implementing zero trust for OT.
Isolate critical systems with segmentation
Zero trust requires custom-tailored security policies and controls to protect specific network resources. That means network teams must logically segment the network based on which resources need to be protected by which policies and technologies, a practice known as micro-segmentation.
OT is often grouped together into a single micro-segment under the assumption that all OT needs the same protection. However, not all OT is created equally, especially in the eyes of a would-be attacker. For example, a programmable logic controller (PLC) gives cybercriminals control over manufacturing processes, but compromising an access control system lets them physically infiltrate the building. Some organizations take zero trust even further by using nano-segmentation to isolate individual systems, applications, or containers to create extremely effective micro-perimeters to address specific vulnerabilities.
Micro- and nano-segmentation are the backbone of a zero-trust architecture, enabling the creation of micro-perimeters using granular access policies and security controls customized for the protected resources.
Create and enforce strong security policies
Zero trust security policies determine who can pass through each micro-perimeter and who can access each OT resource. These policies should follow a least-privilege approach, meaning everyone gets the bare minimum privileges required to complete their workflows and nothing more. The best practice is to use role-based access control (RBAC), categorizing individual accounts based on their role (e.g., system administrators or machine operators) and giving each role least-privilege access to the resources required for that job.
The best way to create and enforce zero trust security policies is with an identity and access management (IAM) solution. A zero-trust IAM solution monitors each micro-perimeter to verify the identities of all accounts requesting access and attempts to establish an account’s trustworthiness using methods like two-factor authentication (2FA). Some advanced IAM solutions even use machine learning technology like user and entity behavior analytics (UEBA) to monitor account activity on the network and spot anomalous behavior that could indicate compromise.
- IAM = Identity and Access Management: Creates and deploys policies, verifies identities, and establishes trustworthiness.
- 2FA = Two-Factor Authentication: Requires an additional form of identity verification (besides the username and password), such as a code sent to an authorized mobile device.
- UEBA = User and Entity Behavior Analytics: Uses machine learning to monitor account activity, creates baselines for normal behavior, and identifies anomalies that could mean an account is compromised.
Strong, granular security policies and zero-trust IAM solutions help protect OT by limiting account privileges and preventing compromised accounts from accessing network resources.
Leverage advanced security technologies
There are additional security technologies that support or enhance zero trust for OT. For example, a next-generation firewall (NGFW) makes network segmentation easier and includes advanced features such as application-aware filtering and deep-packet inspection. Secure access service edge (SASE) delivers zero trust security solutions to the network edge, safeguarding OT at remote branch sites with the same policies and controls as the central enterprise network. AIOps uses artificial intelligence for better threat detection and faster incident recovery.
Organizations use advanced security technologies to fortify micro-perimeters, extend zero trust to the edge, and gain enhanced detection and recovery capabilities.
Implement zero trust for OT with Nodegrid
Zero trust security protects operational technology using network segmentation to create micro-perimeters of strong security policies and advanced security technologies custom-tailored to each individual resource’s requirements and vulnerabilities. Achieving zero trust is typically a long and tedious process because of how many solutions and devices you must deploy.
The Nodegrid solution from ZPE Systems alleviates this challenge by providing a vendor neutral platform capable of hosting and deploying all your zero trust security technologies. For example, Nodegrid network edge routers deliver all the networking capabilities required to spin up an OT branch and can directly host your choice of third-party security solutions. Nodegrid reduces hardware expenses by consolidating network functionality onto fewer devices while unifying network and security management under a single umbrella for greater operational efficiency.
In fact, Nodegrid is an entire Services Delivery Platform that you can deploy anywhere in your network architecture to host your critical third-party SaaS (software as a service) solutions. That means you can create a customized branch-in-a-box that combines gateway routing, switching, out-of-band (OOB) management, NGFW, SASE, infrastructure automation, and more in a single device.
Ready to Learn More?
Contact ZPE Systems to learn more about implementing and enhancing zero trust for OT with the Nodegrid Services Delivery Platform.