This blog describes five potential edge computing use cases in retail and provides more information about the benefits of edge computing for the retail industry.
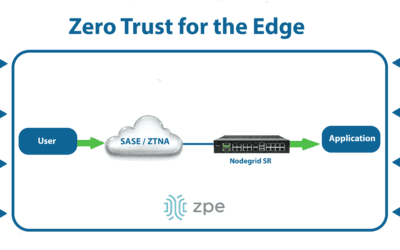
Zero Trust Security
Why Securing IT Means Replacing End-of-Life Console Servers
Rene Neumann, Director of Solution Engineering, discusses why it’s crucial to replace end-of-life console servers to protect IT.
Edge Computing Use Cases in Healthcare
This blog describes six potential edge computing use cases in healthcare that take advantage of the speed and security of an edge computing architecture.
The CrowdStrike Outage: How to Recover Fast and Avoid the Next Outage
The CrowdStrike outage on July 19, 2024 affected millions of critical organizations. Here’s how to recover fast and avoid the next outage.
Benefits of Edge Computing
This blog discusses the five biggest benefits of edge computing, providing examples and additional resources for companies beginning their edge journey.
Improving Your Zero Trust Security Posture
This blog provides advice for improving your zero trust security posture with a multi-layered strategy that mitigates weaknesses for complete coverage.
Edge Computing vs Cloud Computing
This guide compares edge computing vs cloud computing to help organizations choose the right deployment model for their use case.
Edge Computing Architecture Guide
This edge computing architecture guide provides information and resources needed to ensure a streamlined, resilient, and cost-effective deployment.
Critical Entities Resilience Directive
With limited time to demonstrate compliance with the Critical Entities Resilience Directive, organizations should begin preparing now.
PCI DSS 4.0 Requirements
This guide summarizes all twelve PCI DSS 4.0 requirements across six categories and describes the best practices for maintaining compliance.