Edge Computing in Healthcare: Benefits and Best Practices
Modern healthcare is powered by data. There are roughly 10 billion IoT (internet of things) medical devices used in healthcare today, such as pacemakers, insulin pumps, and heart rate monitors. These devices generate a lot of data, which is processed and analyzed by software applications to help clinicians provide better care. Typically, the data collected from these remote devices must be sent somewhere else to be processed – often to an application hosted in a centralized data center or the cloud. However, this is proving too inefficient for the real-time data processing needed in the healthcare industry, where doctors and patients need fast, accurate care solutions. Edge computing in healthcare is the practice of moving computing power and data processing systems closer to the sources of medical data so it can be analyzed at the speed needed to save lives and improve patient outcomes.
To learn more about implementing edge computing in your healthcare organization, reach out to the experts at ZPE Systems.
Cloud computing vs. edge computing in healthcare
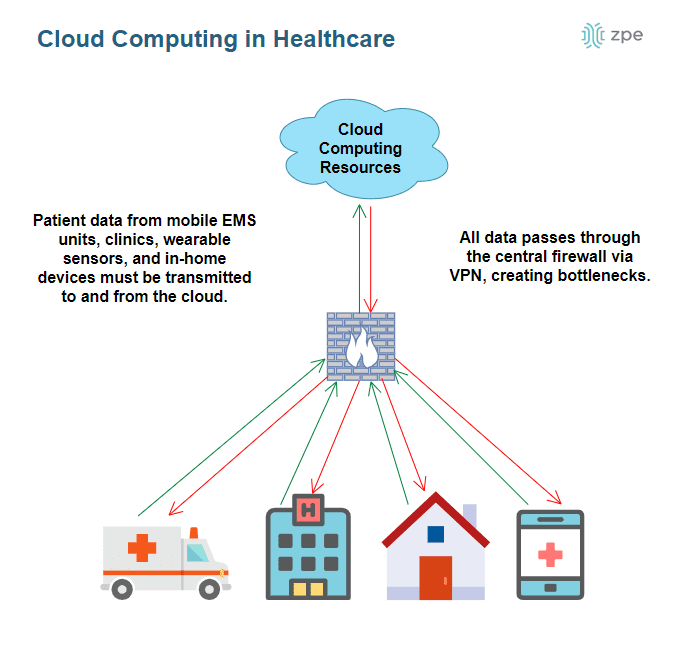
There are a large number of sensors used in a healthcare setting to monitor patient health, including in pacemakers, MRI machines, insulin pumps, and ultrasound imaging devices. These sensors generate large quantities of data that must be processed and analyzed, which requires a lot of computing power. Many organizations have moved away from on-premises data centers and offloaded their computing requirements to the cloud, which saves them from needing to purchase and maintain their own hardware.
However, in a cloud computing model, patient data must be transmitted to and from the cloud for processing, which adds latency and presents additional security challenges. For example, mobile EMS devices and wearable sensors often use cellular networks to connect to cloud computing resources on the internet. However, transmitting patient data over the public internet creates security risks, which is why many healthcare organizations use VPNs to pass that data through the central firewall before it’s sent to the cloud. The firewall turns into a bottleneck that adds additional latency to data transmissions, which prevents real-time data transformation or computation and creates potentially harmful delays.
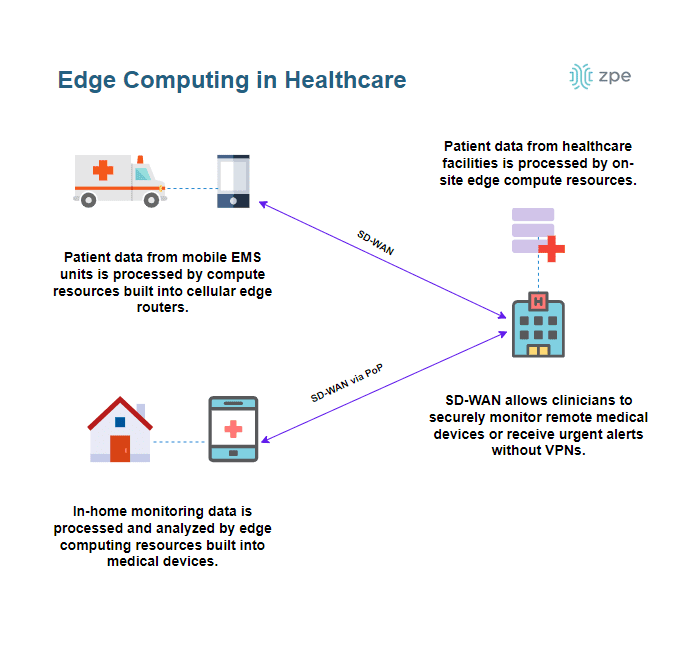
In contrast, the edge computing model processes patient data using computing resources that are on the same LAN, which significantly reduces transmission time. For example, a clinic may have edge computers in the same rack as their networking equipment, or an ambulance may have an all-in-one cellular edge router with data processing capabilities stowed in a small compartment. In some cases, edge computing processors are built into the medical devices themselves, so data collection and data processing happen virtually simultaneously.
Processing health data at the edge reduces latency, which improves the performance and accuracy of the applications using that data. In addition, keeping the data on the local network decreases the risk that it will be intercepted in transit, making security and HIPAA compliance easier. Plus, using SD-WAN (software-defined wide area networking) technology, clinicians can securely monitor and access remote patient health data without the use of VPNs, which means they’re alerted to urgent issues much faster.
In contrast, the edge computing model processes patient data using computing resources that are on the same LAN, which significantly reduces transmission time. For example, a clinic may have edge computers in the same rack as their networking equipment, or an ambulance may have an all-in-one cellular edge router with data processing capabilities stowed in a small compartment. In some cases, edge computing processors are built into the medical devices themselves, so data collection and data processing happen virtually simultaneously.
ZPE Systems can help you simplify your edge.
To learn more, watch our Avoiding Downtime with a Better Edge Infrastructure video.
The benefits of edge computing in healthcare
- Improved remote patient care – The data generated by wearable sensors and other remote health monitoring devices are analyzed in near-real-time, which allows patients and clinicians to respond to potential issues before they become major emergencies.
- Speed and performance – EMS patient data can be processed and analyzed by 5G devices in the ambulance for faster treatment recommendations, or that data can be transmitted to the receiving hospital in real-time so they can better prepare for the patient’s arrival.
- Workload efficiency – Data from monitors and wearables is analyzed in real-time to provide faster insights into diagnostic and treatment options. Plus, data can be automatically prioritized and sent to the relevant clinicians to reduce handoff delays and miscommunications.
- Security – Since patient data is processed on-site instead of being sent to the cloud, it’s easier to maintain HIPAA compliance and prevent interception by malicious actors without needing to use slow, buggy VPNs.
- Diagnostic accuracy – Latency in data transmission can impact the accuracy and precision of diagnostic applications. Running analyses on-site with edge machine learning and big data applications reduces the risk of errors and ensures faster results.
- Lower costs – Big data applications deployed at the edge can provide business insights that help healthcare organizations reduce waste and make fewer mistakes, saving money and lowering the cost per patient without lowering the standards of care.
Best practices for edge computing in healthcare
The following best practices will help you implement and secure an edge computing model in healthcare.
SD-WAN
SD-WAN, or software-defined wide area networking, uses software abstraction to more efficiently manage and operate WANs. The network logic and configurations are decoupled from the underlying WAN hardware infrastructure, which frees healthcare organizations from some of the limitations of traditional WAN.
For example, the patient data collected by machines in the back of an ambulance can be processed by an edge computer built into a cellular SD-WAN router and then securely transmitted to the receiving hospital without a VPN. This can be done even though the ambulance is using cellular internet and isn’t connected to the MPLS backbone of the hospital’s WAN thanks to SD-WAN’s software abstraction.
SD-WAN can also give clinicians a secure and reliable way to monitor wearable and in-home medical devices, even when patients live in remote locations. SD-WAN uses points-of-presence, or PoPs, which are deployed in key geographic areas to provide a means for remote devices to connect to the WAN.
In either case, devices are connected to the main organization’s network, which means enterprise security policies and controls can be applied without the use of VPNs (more on that below). And, since most data is still processed on-site by edge computing resources, there’s significantly less bottlenecking.
Security
Processing patient health data at the edge reduces security risks, but it doesn’t eliminate them altogether. The same goes for SD-WAN; it’s safer than having patient data transmitted to the cloud across the open internet, but SD-WAN architectures often still rely on the public internet for the last mile between the PoP and the end user or device. Patient health and billing data is a valuable target for malicious actors, and there are potential HIPAA violation fines to deal with if edge computing architectures aren’t properly secured. That’s why security needs to be built into edge computing in healthcare from the ground up.
- Zero trust security is a best practice for every industry, but it’s especially important in the heavily-regulated healthcare sector. The zero trust methodology is based on the principle of “never trust, always verify.” That means access rights are granted to accounts on a role-based or least-privileged basis, and trust is continuously re-evaluated as an account tries to access additional data or resources. This prevents lateral movement on the network if, say, the service account for a wearable sensor is compromised.
Zero trust security is established through granular access policies and security controls that are specific to the edge resources being protected. These policies are enforced through identity and access management (IAM) solutions as well as edge security technologies like SASE. Trust is evaluated with tools like user and entity behavior analytics (UEBA) which use customizable baselines and machine learning algorithms to provide context-based analysis of the trustworthiness of an account.
For example, if a device service account is behaving suspiciously by logging in from an odd location, UEBA can take immediate action by blocking access and triggering the IAM solution to ask for identity re-verification. In this context, that might mean the patient receives a text message on a verified mobile phone asking them to confirm that they (and the device) are in the same location the device is logging in from. If not, the account password can be changed to prevent the malicious actor from gaining access to sensitive patient data or potentially jumping to the main hospital network.
- SASE, or Secure Access Service Edge, combines SD-WAN technology with a stack of cloud-based cybersecurity services that are designed to protect the network edge. SD-WAN routes traffic to and from edge computing resources through the SASE tech stack, which allows zero trust security policies and controls to be extended to the last mile.
For example, SASE uses a technology called Zero Trust Network Access (ZTNA) to provide a secure connection between edge devices and resources on the central network. Whenever an edge device or account attempts to connect to the main network – say, to deliver data analytics to an on-premises dashboard application – ZTNA verifies its identity and gives it the specific access it requested.
With ZTNA, the edge device or account cannot see or interact with any resources on the network other than what it specifically requires for its present function and must make a new request (and verify its identity again) to access something else. This decreases the attack surface if a malicious actor compromises an edge account – they have to pass through many different identity verification hurdles to move around the network, and every action they take has the potential to trigger UEBA.
Speaking of UEBA, that’s another security service that’s frequently offered by SASE providers. Other common security technologies include malware detection, data loss prevention (DLP), and Firewall as a Service (FWaaS). Learn more about the SASE technology stack in What Is SASE Network Security? A Beginner’s Guide.
Automation
Edge computing can increase the complexity of a network, making it challenging for administrators to manage it efficiently without increasing the risk of human error. However, the model we’ve described so far for edge computing in healthcare lends itself very well to automation.
For example, healthcare organizations can use SD-WAN’s software abstraction to centralize the management of the entire extended architecture behind a single orchestration platform. This platform can be used to create, deploy, and update network automation scripts and workflows, significantly reducing manual workloads. For instance, SD-WAN can be configured to use application- and context-aware routing rules to determine which remote traffic should be sent through the SASE stack instead of the primary firewall.
In addition, as we’ve touched on above, the vast amounts of data generated by remote health devices can be used to power big data and machine learning applications on the edge. This data can also be used by AIOps solutions for more “intelligent” networks and IT automation. AIOps – artificial intelligence for IT operations – analyzes sensor and device data and provides recommendations that administrators can use to better maintain and optimize remote medical systems and networks. AIOps can even use its analysis to predict future outcomes, make decisions, and solve problems automatically. Learn more about AIOps in Using AIOps and Machine Learning to Manage Automated Network Infrastructure.
Vendor-neutral platforms
All of the benefits and best practices listed above are much easier to achieve using vendor-neutral management platforms. The goal of a vendor-neutral platform is to reduce management complexity so that administrators can efficiently operate and secure the entire extended network architecture. Ideally, this platform will unify SD-WAN orchestration, security monitoring, edge device management, and automation behind a single pane of glass.
This reduces the number of management systems that admins need to learn how to configure, operate, and optimize. The fewer moving parts to deal with, the fewer mistakes will be made, which will improve the reliability of the edge architecture. In addition, vendor-neutral platforms enable admins to monitor every device, application, and network workflow from a single place, giving them a more holistic understanding of the health and security posture of the network. This opens up more opportunities for optimization and innovation while also preventing any issues from slipping between the cracks.
Simplifying edge computing in healthcare with Nodegrid
Nodegrid simplifies edge computing by providing a completely open, vendor-neutral platform that you can use to manage or host any other solution on your network. For example, you could install the Mini SR edge gateway router in ambulances to provide mobile SD-WAN access, remotely monitor and manage edge devices, and even host edge computing applications, all on a device roughly the size of an iPhone. Plus, you can use the Nodegrid management platform to host, deploy, and orchestrate your choice of third-party automation solutions including healthcare AIOps applications.
