The European Union’s Digital Operational Resilience Act (DORA) creates a regulatory framework for information and communication technology (ICT) risk management and network resilience. It entered into EU law on 16 January 2023 and took effect on 17 January 2025, applying to any firm operating within the European financial sector. This guide outlines the technical requirements for DORA compliance and provides tips and best practices to streamline implementation.
Citation: Digital Operational Resilience Act (DORA)
Which organizations does DORA affect, and what are the consequences of non-compliance?
DORA applies to financial entities operating in the European Union, including:
- Financial services
- Payment institutions
- Crypto-asset service providers
- Crowdfunding service providers
- Investment firms
- Insurance companies
- Data analytics and audit services
- Fintech companies
- Trading venues
- Credit institutions
- Credit rating agencies
Crucially, DORA also applies to third-party digital service providers that work with financial institutions, such as colocation data centers and cloud service providers.
Once DORA takes effect, each EU state will designate “competent authorities” to enforce compliance. Each state determines its own penalties, but potential consequences for non-compliance include fines, remediation, and withdrawal of DORA authorization.
ICT service providers (such as cloud vendors) labeled “critical” by the European Commission face additional oversight and non-compliance penalties, including fines of up to 1% of the provider’s average daily worldwide turnover the previous business year. Overseers can levy fines on a provider every day for up to six months until compliance requirements are met. These steep penalties make it essential for service providers to ensure their systems and processes are DORA-compliant.
What are DORA’s technical requirements?
ICT risk management
DORA requires financial institutions to develop a comprehensive ICT risk management framework containing strategies and tools for business resilience, recovery, and communication. In addition to written policies and documented procedures, financial entities must implement technology such as security hardware and software, redundancies and backups, and resilience systems. Best practices for DORA-compliant risk management technologies include:
ICT third-party risk management
Financial organisations in the EU must manage the risk of working with third-party vendors to prevent supply chain attacks such as the MOVEit breach. ICT third-party risk management (TPRM) involves performing vendor due diligence to validate compliance with security standards and ensuring contractual provisions are in place to hold vendors accountable for security failures. On the technical side, financial entities should implement security policies and controls to limit third-party access and use monitoring tools that detect vulnerabilities, apply patches, and identify suspicious account behavior. Best practices for DORA-compliant TPRM technologies include:
Digital operational resilience testing
DORA requires financial entities to establish a resilience testing program to validate their security defenses, backups, redundancies, and recovery systems once per year. Examples of resilience tests include vulnerability scans, network security assessments, open-source software analyses, physical security reviews, penetration testing, and source code reviews. Financial entities deemed “critical,” as well as their critical ICT providers, must also undergo threat-led penetration testing (TLPT) every three years. DORA stipulates that these tests be performed by independent parties, though they can be internal so long as the organization takes steps to eliminate any conflict of interest. Technical best practices include:
ICT incident reporting
DORA streamlines and consolidates the incident reporting requirements that are currently fragmented across EU states. The takeaway from this section is a requirement for financial firms to submit a root cause report within one month of a major incident. Technical best practices for meeting this requirement involve using AIOps for:
Information sharing
This is less of a requirement than a suggestion, but DORA both allows and encourages financial institutions to share cyber threat information within the community to help raise awareness and mitigate risks. Best practices involve using (anonymized) logs from some of the technologies mentioned above, such as UEBA and AIOps.
Oversight of critical third-party providers
DORA requires “critical” digital service providers to follow the same compliance rules as the financial institutions they work with. Regulators may deem a provider critical if a large number of financial entities rely on them for business continuity or if they are difficult to replace/substitute when a failure occurs. Any cloud vendors, colocation data centers, or other digital service providers working in the EU’s financial sector should prepare for DORA by implementing:
Best practices for DORA compliance
Some of the technologies that can help simplify DORA compliance for financial institutions and critical service providers include:
Control/data plane separation
Separating the data plane (i.e., production network traffic) from the control plane (i.e., management and troubleshooting traffic) simplifies DORA compliance in two key ways:
- It isolates the management interfaces used to control ICT systems, making them inaccessible to malicious actors who breach the production network and aiding in resilience.
- It prevents resource-intensive automation, security monitoring, and resilience testing workflows from affecting the speed or availability of the production network.
The best practice for control and data plane separation is to use Gen 3 out-of-band (OOB) serial consoles, such as the Nodegrid product line from ZPE Systems. Gen 3 OOB provides a dedicated network for management traffic that doesn’t depend on production network resources, ensuring remote teams always have access, even during outages or ransomware attacks. It’s also vendor-neutral, allowing administrators to deploy third-party monitoring, automation, security, troubleshooting, and testing tools on the isolated control plane. Gen 3 OOB helps financial institutions and ICT service providers meet resilience and testing requirements cost-effectively.
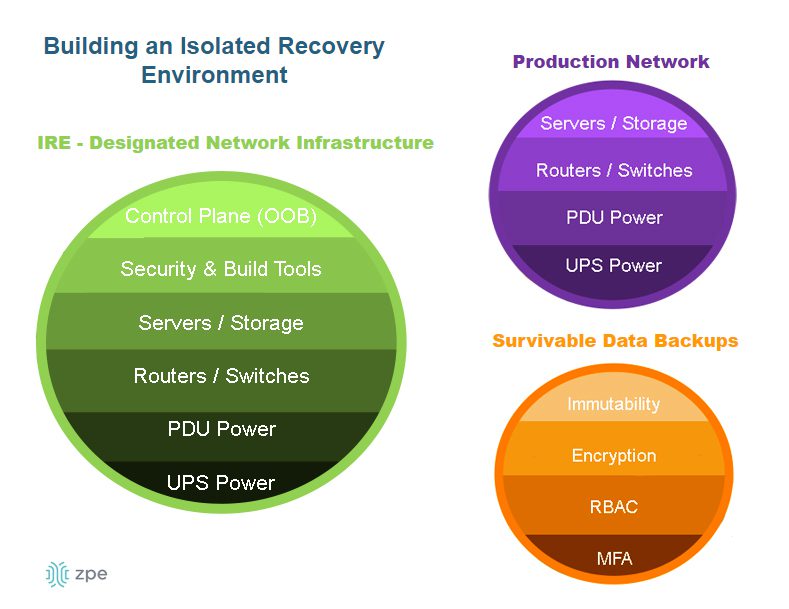
Isolated recovery environments
Ransomware continues to be one of the biggest threats to resilience, with ransomware cases increasing by 73% in 2023 despite heightened awareness and additional cybersecurity spending. Preventing an attack may be nearly impossible, and full recovery often takes weeks due to the high rate of reinfection. The best way to reduce recovery time and meet DORA resilience requirements is with an isolated recovery environment (IRE) that’s fully separated from the production infrastructure.
An IRE contains systems dedicated to recovering from ransomware and other breaches, where teams can rebuild and restore applications, data, and other resources before deploying them back to the production network. It uses designated network infrastructure that’s completely separate from the production environment to mitigate the risk of malware reinfection. It also contains technologies like Retention Lock, role-based access control, and out-of-band management so teams can quickly and safely recover critical services and reduce DORA penalties.
Automated patch management
Cybercriminals often breach networks by exploiting known vulnerabilities in outdated software and firmware, as happened with 2023’s Ragnar Locker attacks. For large financial institutions and critical ICT providers, manually tracking and installing patches for all the third-party hardware and software used across the organization is too difficult and time-consuming, leaving potential vulnerabilities exposed for years. The best practice for meeting DORA’s third-party risk management requirement is to use an automated, vendor-agnostic patch management solution.
Automatic patch management tools discover all the software and devices used by the organization, monitor for known exploited vulnerabilities, and notify teams when vendors release updates. They centralize patch management for the entire network to simplify TPRM and aid in DORA compliance.
AIOps
AIOps uses artificial intelligence technology to automate and streamline IT operations. AIOps collects and analyses all the data generated by IT infrastructure, applications, monitoring tools, and security solutions to help identify significant events and make “intelligent” recommendations. AIOps helps with DORA compliance by providing:
- Anomaly detection – Artificial intelligence analyses logs and detects outlier data points that could indicate an in-progress data breach or other problematic event.
- Incident management – AIOps automatically generates, triages, and assigns service desk tickets to the appropriate team for resolution, significantly accelerating incident response.
- Root-cause analysis – AIOps combs through all the relevant logs to determine the most likely cause of adverse events, making it easier to meet DORA’s root-cause reporting requirements.
How ZPE streamlines DORA compliance
The Nodegrid out-of-band management platform from ZPE Systems helps financial institutions and critical service providers meet DORA resilience requirements without increasing network complexity. Vendor-neutral Nodegrid serial consoles and integrated edge services routers deliver control plane isolation, centralized infrastructure patch management, and Guest OS/container hosting for third-party security, recovery, and AIOps tools. The Nodegrid platform provides a secure foundation for an isolated recovery environment that contains all the technology needed to get services back online and stay DORA compliant.
Download our 3 Steps to Ransomware Recovery whitepaper to learn how to improve network resilience with Nodegrid.
Download the Whitepaper
See how Nodegrid helped one of the EU’s largest banks meet modern security and compliance requirements.
Read the case study
Looking to replace your discontinued, EOL serial console with a Gen 3 out-of-band solution?
Looking to replace your discontinued, EOL serial console with a Gen 3 out-of-band solution? Nodegrid can expand your capabilities and manage your existing solutions from other vendors.