
This article was written by James Cabe, CISSP, whose cybersecurity expertise has helped major companies including Microsoft and Fortinet.
MOVEit over SolarWinds — The largest and most successful ransomware attack ever recorded is happening. Right now. It’s attacking healthcare and financial institutions with high rates of success, and recently stole sensitive data of 4 million more healthcare patients. It uses something called CL0P ransomware, and the threat actor is a well-known criminal group with the name FIN11. Many organizations are finding it difficult to stop the attack because they have no way to access infected devices, take them offline, patch, or even replace them. So, what exactly is going on?
The group responsible for the attack
FIN11 is a cybercriminal group that has been active since 2016 or before, originating from the Commonwealth of Independent States (CIS). While the group has historically been associated with widespread phishing campaigns, their focus has shifted towards other initial access vectors. FIN11 often runs high-volume operations targeting industries in North America and Europe for data theft and ransomware deployment, primarily leveraging CL0P (aka CLOP).
FIN11 is responsible for multiple widespread, high-profile intrusion campaigns leveraging zero-day vulnerabilities, and the group likely has access to the networks of many more organizations than it is able to successfully monetize. Despite this, they’re currently attacking MOVEit, a well-known SaaS provider who relies on a file transfer appliance called Accellion lFile Transfer Appliance (FTA). This legacy product remains unpatched, which has led to the breach of many Fortune 100 companies and state and federal agencies.

How did the ransomware attack start?
The ransomware attack began with several Accellion FTA customers, including those in industries like healthcare, legal, finance, retail, and telecom. Companies such as Jones Day Law, Kroger, Singtel, and many others had no idea that they had been attacked, because the initial breach was quiet and headless.
Their only indication came after receiving a threatening email aimed at extortion.
In this email, the group threatened to publish stolen data on the “CL0P^_- LEAKS” .onion website, according to an investigation from Accellion. The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) are releasing this joint CSA to disseminate known CL0P ransomware IOCs and TTPs identified through FBI investigations as recently as June 2023.
According to the investigation, four zero-day security holes were exploited in the attacks:
- CVE-2021-27101 – SQL injection via a crafted Host header
- CVE-2021-27102 – OS command execution via a local web service call
- CVE-2021-27103 – SSRF via a crafted POST request
- CVE-2021-27104 – OS command execution via a crafted POST request
And, the published victim data appears to have been stolen using a “WEB SHELL”. These web shells give remote administrative access to the web server and create a jumping off point to attack the rest of the internal network. Mandiant, a well-known cyber investigation arm of Google, added, “The exfiltration activity has affected entities in a wide range of sectors and countries” (Threatpost). Exfiltration is the unauthorized removal of important or damaging data from an organization.
However the biggest problem is that these web shells are what researchers call “PERSISTENCE”. This means that an attacker can remain in your network indefinitely to continue damaging and attacking your resources. Researchers call these “APTs,” or Advanced Persistent Threats.
Why is the ransomware attack still going strong?
The ransomware attack is still going strong because there’s no patch available. According to open source information, beginning on May 27, 2023, CL0P Ransomware Gang began exploiting a previously unknown SQL injection vulnerability (CVE-2023-34362) in Accelion’s appliance that is the backbone of a solution known as Progress Software’s MOVEit Transfer service. Internet-facing MOVEit Transfer web applications were infected with a web shell named LEMURLOOT, which was then used to steal data from underlying MOVEit Transfer databases. In similar spates of activity, TA505, which is the group responsible for the Dridex trojan and Locky ransomware, conducted zero-day-exploit-driven campaigns against Accellion FTA devices in 2020 and 2021, and Fortra/Linoma GoAnywhere MFT servers in early 2023.
What most organizations want to know is: How do you quickly respond to issues like these? How can you be properly prepared to respond to an issue you didn’t cause or didn’t expect?
Patching is a good response. However, it takes an average of 205 days to patch a recently known zero-day exploit like the MOVEit vulnerability. While patching alone is typically the ideal response, it isn’t automatic nor can it be done quickly.
Another approach involves removing the offending software or appliance, or cutting off access to the software or appliance. But once you remove this access, how do you continue normal operations, and how can you easily bring the software/appliance back online? Without adequate infrastructure in place, physically deploying to each site is not practical, especially for distributed organizations.
CISA and the FBI encourage organizations to implement the recommendations in the Mitigations section of this CSA to reduce the likelihood and impact of CL0P ransomware and other ransomware incidents. The Mitigations section describes many approaches, including patching, removing software/appliance access, and implementing a recovery plan. But all of these take too much time and too many resources, which leaves organizations vulnerable as they scramble to create an adequate response.
The great news is, organizations can cover all their bases without having to reinvent the wheel. This approach is recommended in one of CISA’s recent directives, and gives organizations somewhat of a silver bullet that allows them to quickly defeat ransomware and remain prepared for any future attack.
What approach does CISA recommend to address ransomware attacks?
CISA’s recent directive (23-02), which addresses the vulnerability of Internet-exposed management interfaces, calls for organizations to create an isolated management infrastructure (IMI) via out-of-band connectivity. This is a drop-in solution that the military, telcos, and hyperscalers/cloud companies use to respond to widespread ransomware and other issues impacting security and resilience. This approach — which ZPE Systems has perfected in the last decade with the help of Big Tech — gives organizations a completely separate control plane through which they can monitor and manage their entire IT infrastructure in a safe and dedicated fashion.
What is isolated management infrastructure?
Isolated management infrastructure consists of the hardware and software that create a management network that’s fully separate from other production and management networks. The key to this is in out-of-band connectivity, which is defined as connectivity other than TCP/IP. Out-of-band can include direct USB, serial, or even non-routed zero-trust connections to crown-jewel assets.
Essentially, the IMI gives an organization complete oversight and control of their widespread IT infrastructure, in a way that is secure and accessible only to their IT teams.
In this diagram, the production infrastructure (blue ring) sits at each distributed location. The out-of-band infrastructure for LAN (OOBI-LAN) is the green ring and surrounds the production infrastructure with one layer of isolated management. The OOBI-WAN (orange ring) is what provides a second layer of isolated management, which teams can access from a central or remote location, to gain access to the OOBI-LAN and ultimately the production infrastructure.
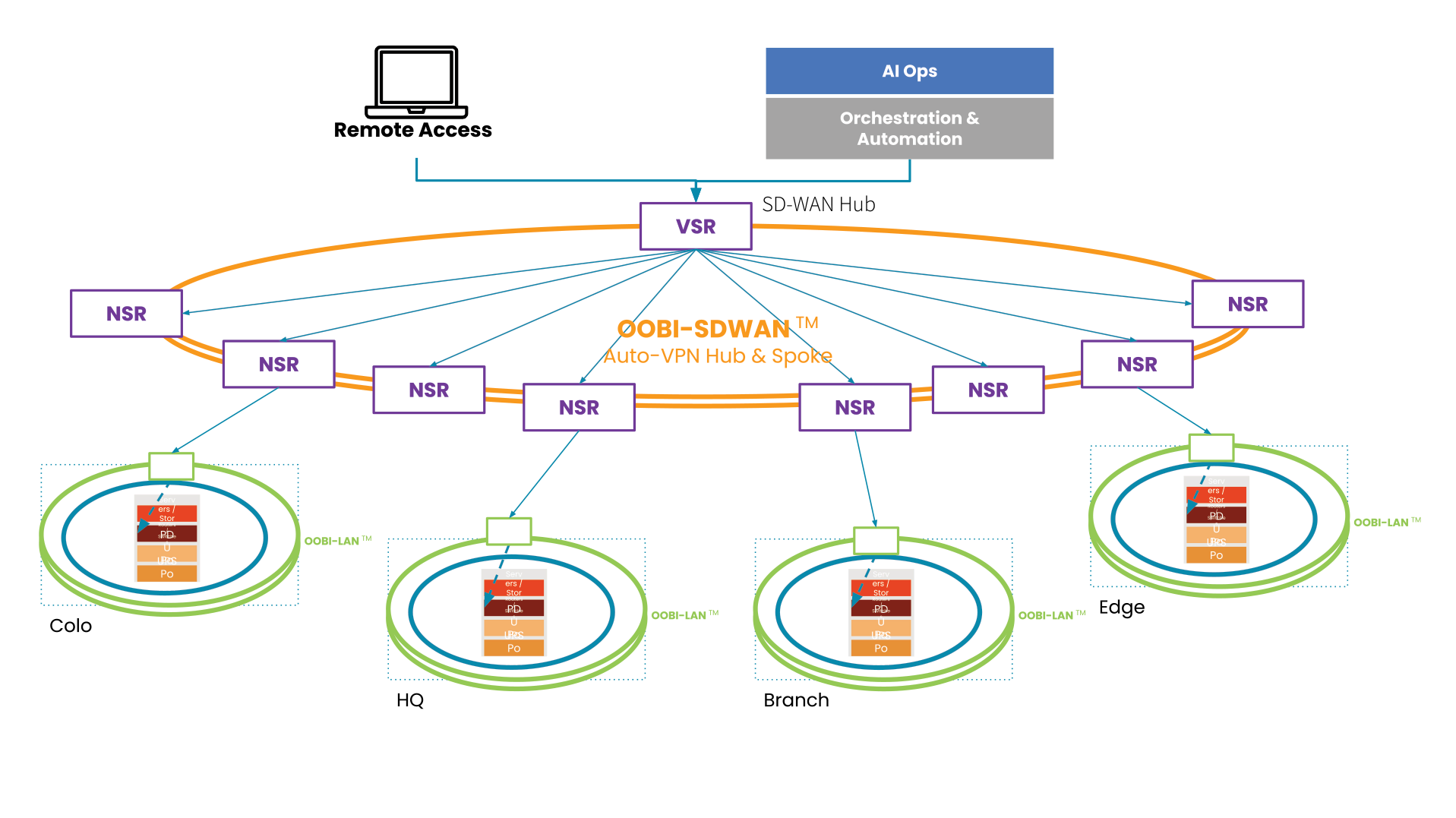
Knowing these assets and providing access across the organization can be easy and does not have to disrupt current operations.
How can IMI stop the FIN11 ransomware attack?
In the ongoing FIN11 ransomware attack, Internet-facing applications are targets of the zero-day exploit. This means that no amount of security solutions can pre-mitigate the attack (i.e., there’s nothing you can do to stop it). This is where IMI shines.
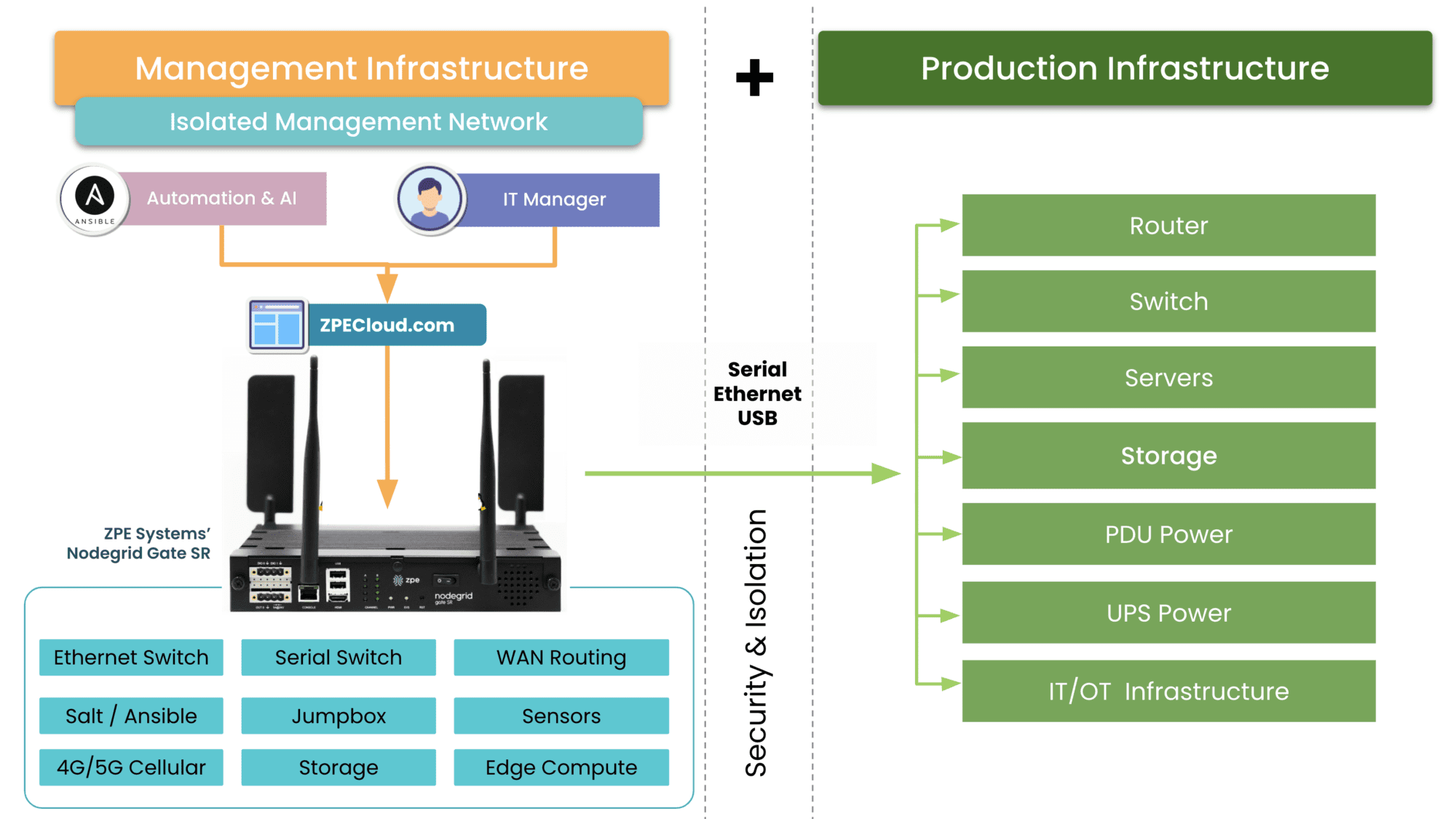
Remember the OOBI-LAN/OOBI-WAN diagram? Here’s a zoomed-in view of the isolated management infrastructure sitting beside the production infrastructure. The IMI connects via serial, Ethernet, and USB to production gear, and provides the necessary functions (routing, storing golden images, hosting jumpbox tools, etc.) to recover from attack. But how?
IT teams can use OOBI-WAN to remotely access their OOBI-LAN and production gear. They can pull affected devices offline and bring them in for forensics, which takes place in an Isolated Recovery Environment (IRE). This means these assets and networks are still reachable by analysts and responders, but isolated from other vulnerable assets. This allows an organization to quickly and even automatically deploy tools and resources inside of this environment through devices like ZPE Systems’ Nodegrid.
To combat the FIN11 attack, organizations don’t need to unplug cables or shut their devices off. They can instead deploy their IMI as the framework for closing the attack surface while maintaining access and critical data to aid in recovery.
Get the blueprint for isolated management infrastructure
Don’t wait until the next attack to shore up your defenses. ZPE Systems has worked with Big Tech for ten years developing the isolated management infrastructure. It’s now available inside the Network Automation Blueprint, and walks you through how to implement your own IMI. Download the blueprint now to stay ready for any attack.
Get in touch with me!
True security can only be achieved through resilience, and that’s my mission. If you want help shoring up your defenses, building an IMI, and implementing a Resilience System, get in touch with me. Here are links to my social media accounts:
