This scenario is every IT professional’s worst nightmare: it’s the middle of the night, a remote site on the other side of the country has gone offline, and nobody knows why. A single minute of downtime can cost anywhere from several hundred dollars to tens of thousands of dollars, and the nearest tech is a six-hour plane ride away. Consider the recent CrowdStrike outage and the devastation caused for banks, airports, and many other organizations.
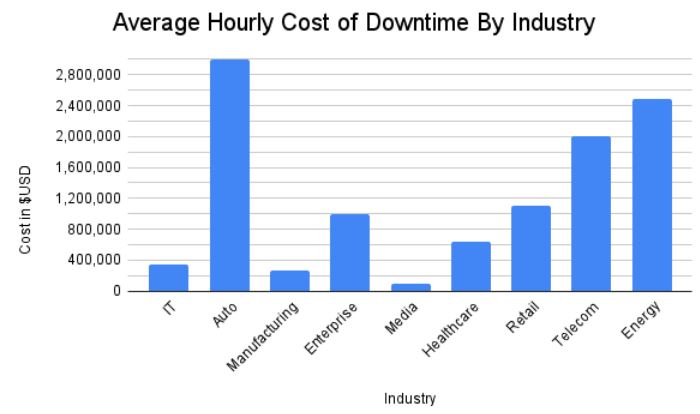
Data Source: SolarWinds
Out-of-band management offers the solution: a way for teams to access critical remote infrastructure during outages and breaches without “out-of-chair” expenses. Out-of-band management allows organizations to recover remote infrastructure faster, reducing the duration and expense of downtime.
This guide to out-of-band management answers critical questions about what this technology is, why you need it, and how to choose the right solution.
What is out-of-band management?
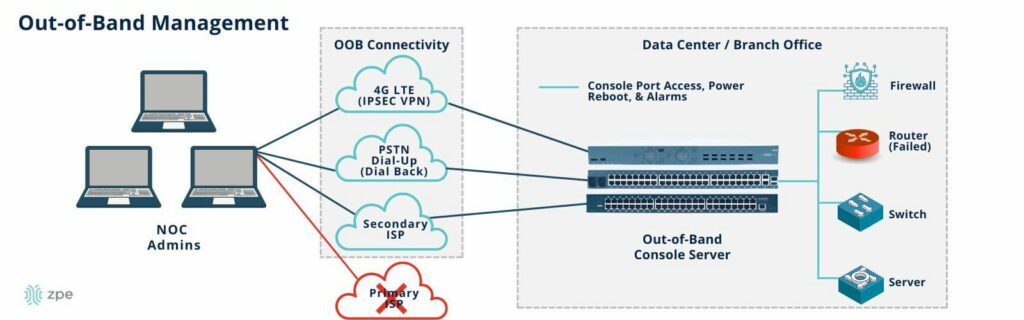
Out-of-band management (OOBM) involves controlling network infrastructure and workflows on an out-of-band network. An out-of-band network is an entirely separate network that runs parallel with your production (or in-band) network but doesn’t rely on any of the same infrastructure or services. OOBM allows teams to administer network infrastructure remotely on a dedicated connection, such as secondary Fiber or cellular LTE, that will remain available even if the in-band network goes down from an equipment failure, ISP outage, or ransomware attack.
The biggest reason to use out-of-band management is to ensure continuous, uninterrupted access to critical remote infrastructure even when the primary network is down. OOBM allows teams to recover from outages and cyberattacks faster and more cost-efficiently because they can access, troubleshoot, and restore systems without rolling trucks or hiring on-site services.
Out-of-band management provides a lifeline for teams to access critical remote infrastructure when the production network is offline. It allows them to immediately begin troubleshooting and repairing the issue to restore services ASAP. With OOBM, companies save money on recovery expenses, and minimize the duration and business impact of downtime.
What is an OOBM serial console?
Some organizations use OOBM jump boxes (or jump servers) that are connected to both the in-band and out-of-band networks, allowing administrators to “jump” from one network to the other for management. Examples of low-cost jump boxes include the Intel NUC and the Raspberry Pi. However, OOBM jump boxes are security risks because they do not effectively isolate the management infrastructure, plus they require an entire duplicate infrastructure of devices and services to create the out-of-band network. The best practice for security, resilience, and efficiency is to deploy an all-in-one, out-of-band management solution.
An out-of-band management solution uses hardware devices known as serial consoles, which connect to infrastructure devices via their management port (usually RS232 Serial, Ethernet, or USB). Serial consoles are known by lots of other names, including terminal servers, console servers, console server switches, serial routers, and serial switches.
The serial console has dedicated network interfaces to provide an Internet connection for remote management access, often fiber or 4G/5G cellular LTE, so they don’t connect to or rely upon the primary production network at all. This gives teams the ability to continuously monitor and administer critical remote infrastructure even during an ISP or WAN outage that would make a jump box inaccessible.
Administrators remotely access an OOBM serial console via this dedicated link and, from there, can view and manage all connected infrastructure from a single, convenient software platform. This software is typically deployed on-premises and runs as a VM (virtual machine) either on the serial console itself or on a separate machine, but there are some cloud-based OOBM network management software tools.
Out-of-band management software varies from provider to provider, with most offering second-generation (or Gen 2) solutions that provide some built-in automation capabilities but do not support vendor-neutral integrations with third-party tools. Newer, third-generation (or Gen 3) solutions use an open, x86 Linux-based operating system to allow easy integrations with other vendors’ software for automation, orchestration, security, monitoring, and more.
The benefits of out-of-band management
Out-of-band management can help you:
- Improve network performance: Performing resource-intensive management, automation, and orchestration workflows on the out-of-band network reduces the strain on the production network for better speed and reliability.
- Reduce your attack surface: OOBM is a core component of an isolated management infrastructure (IMI), which takes management interfaces off the production network to prevent cybercriminals from accessing them during a breach. IMI is recommended by CISA’s binding directive 23-02.
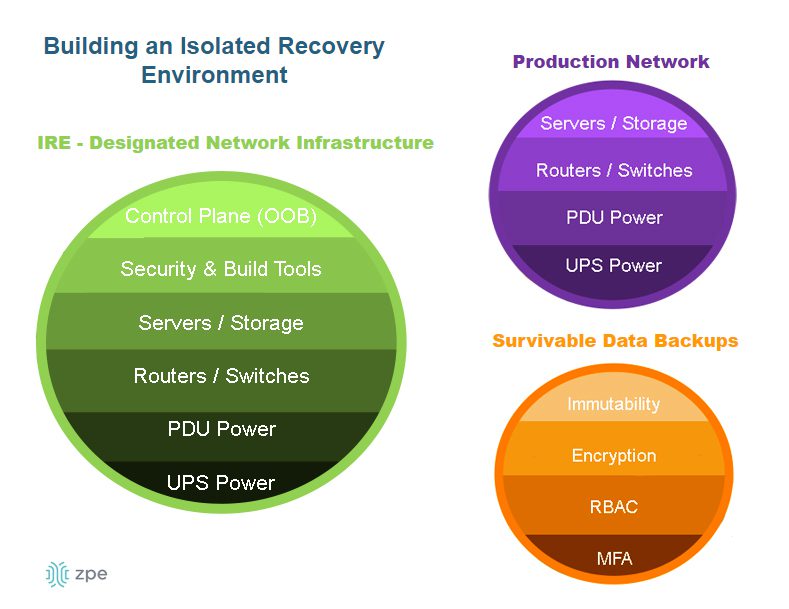
- Accelerate ransomware recovery: The OOBM network can be used to create an isolated recovery environment (IRE) where teams can safely rebuild and recover from ransomware attacks without the risk of reinfection, reducing the duration and expense of ransomware-related outages.
- Streamline repairs and rebuilds: OOBM provides the ability to deploy the tools and applications needed to isolate, cleanse, rebuild, and restore services that have been affected by failures and ransomware.
The security and resilience benefits of out-of-band management are discussed further below.
How does out-of-band management improve security and resilience?
Network breaches and ransomware attacks occur so frequently that most businesses know it’s no longer a question of “if,” but “when” they’ll be hit. Once cybercriminals compromise a device or account and can move around the network, it’s only a matter of time before they find the management interfaces and take complete control over critical infrastructure.
OOBM and management infrastructure isolation
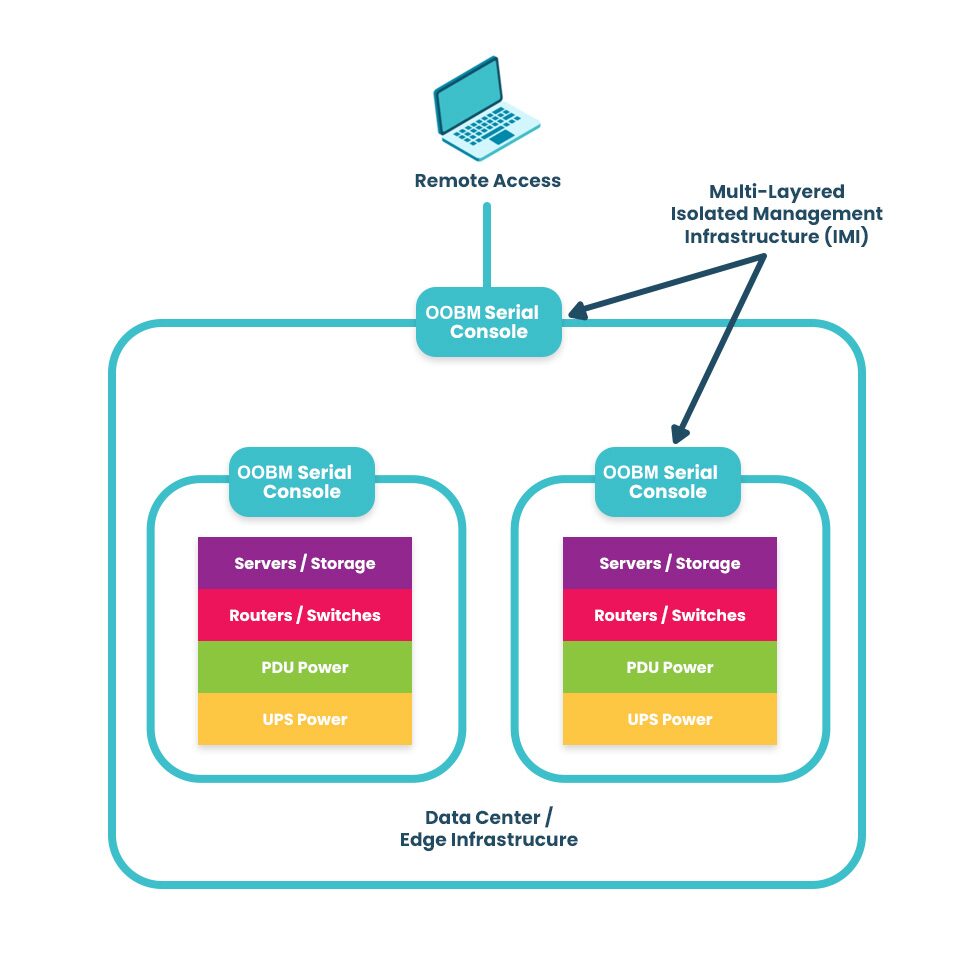
Serial consoles create an out-of-band network by directly connecting to the management port of infrastructure devices and moving all control functions off of the production LAN. This isolates the management plane from the data plane, which is part of a cybersecurity best practice known as isolated management infrastructure (IMI). An IMI further segments the management network and routes management ports to terminate on top-of-rack, OOBM serial switches, creating multiple layers of isolated management. The isolated management plane is always remotely accessible to engineers via the OOBM connection, but it remains hidden from any cybercriminals who may breach the production network.
OOBM and ransomware recovery
Out-of-band management also improves security and resilience by aiding in ransomware recovery. According to a Sophos survey, 70% of companies hit by ransomware take longer than two weeks to recover, due in no small part to the pervasive nature of the malware used and how frequently rebuilt systems and recovered data get reinfected. Today’s ransomware attacks are now pre-packaged and move at machine speed – meaning instantly – across infrastructure, bringing entire businesses down before they’ve even realized they’re under attack. The longer the business is offline, the more revenue (and customer trust) is lost, causing recovery costs to skyrocket.
An IMI using out-of-band management gives teams an isolated recovery environment (IRE) where they can recover data and rebuild systems without the risk of reinfection. The IRE allows organizations to get services back online faster to reduce the financial and reputational consequences of ransomware attacks.
Resilience is defined as the ability to continuously operate and deliver services, if in a degraded fashion, even while undergoing major failures and breaches. Out-of-band management improves resilience by ensuring that teams have continuous access to critical remote infrastructure no matter what’s going wrong with the production environment. OOBM serial consoles also isolate the management infrastructure to protect it from attackers on the primary network and provide a safe environment for teams to recover from ransomware.
Why choose Nodegrid for out-of-band management?
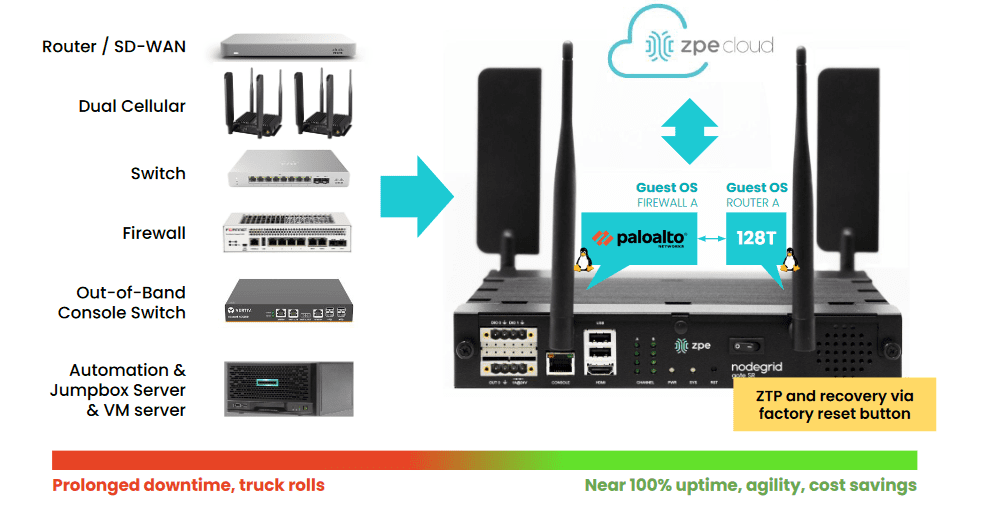
Many network teams think of out-of-band as being a huge expense and time sink. Setting up proper infrastructure for OOBM and IMI typically requires 6 or more boxes at each business site for routing, switching, firewall, storage, cellular access, and a jump box. The Nodegrid platform from ZPE Systems reduces the cost and headache of out-of-band management by combining all these functions and more into a single box. Teams can easily drop a Nodegrid box in each site at a fraction of the cost of deploying a traditional OOBM network.
The first Gen 3 OOBM solution
Nodegrid is the first and only Gen 3 out-of-band management solution. Nodegrid OOBM devices use the x86 Linux-based NodegridOS, which is capable of running VMs and Docker containers to host your choice of third-party applications for automation, orchestration, security, SD-WAN, and more. Nodegrid’s ability to host other vendors’ software ensures that teams have access to all the tools they need to troubleshoot and recover infrastructure from within the IMI environment, making it the perfect network resilience multi-tool.
Nodegrid OOBM software is available as an on-premises solution or a highly scalable cloud-based app, and both support easy integrations with tools for monitoring, automated configuration management, and more. This enables teams to consolidate and streamline their workflows, maximizing efficiency while reducing the risk of human error.
Nodegrid’s other key features include:
- Built-in 5G/4G LTE and Wi-Fi options for OOB and network failover
- OOB support over IPMI, ILO, DRAC, CIMC, vSerial, and KVM
- Robust hardware security like BIOS protection, UEFI Secure Boot, and an encrypted solid-state disk
- SAML 2.0 and two-factor authentication (2FA)
- Support for legacy and mixed-vendor infrastructure without expensive adapters
ZPE Systems offers a wide range of out-of-band management devices to fit any deployment size and use case, including the 96-port Nodegrid Serial Console Plus (NSCP) for large and hyperscale data centers, and the Nodegrid Gate SR, which combines branch gateway routing and OOB serial console functionality for remote business sites like retail stores and manufacturing plants.
Nodegrid OOB serial console comparison
Nodegrid OOB network edge router comparison
Get scalable network resilience with the only Gen 3 out-of-band management solution
Only Nodegrid OOBM delivers network control, security, automation, and resilience with a completely vendor-neutral platform. To see Nodegrid out-of-band management in action, request a free demo.