How to implement zero trust security is a growing focus of organizations across the globe. With cyber attacks frequently hitting some of the largest companies and threatening entire economies, it’s no wonder why comprehensive network security is a top priority among public- and private-sector entities.
In this post, we’ll show you what you need to implement zero trust security, from big-picture items to individual technologies.
But first, here’s a recap of zero trust security and why your business won’t be safe without it.
Why you need Zero Trust Security
Imagine bringing in a new hire to your department. Soon after, you notice suspicious computer slowdowns and applications that don’t respond as usual. You dive into your program files and discover an unknown .exe file, and you dive deeper to discover attackers actively exploiting your resources. You quickly pull your team together to lock down your network, sanitize every computer and connection, and send out a company-wide instruction to have every employee reset their password.
It turns out, your newest employee unknowingly clicked a bad link and opened the door for a trojan horse attack. But because of your quick response, no significant damage was done and you can rest easy again.
Months later, you come in for your normal workday only to find all your systems locked and unresponsive. Dave, a senior engineer, retired on the day of the attack and never reset his password. The hackers stole his credentials and have gone unnoticed for months. Now your company and its customers are compromised, and the consumer markets you serve are in a frenzy due to a shortage of goods. You can’t help but feel somewhat responsible for the entire ordeal.
This example mimics recent real-world cyberattacks and highlights the importance of moving away from traditional security approaches.
Traditional architecture uses the castle-and-moat security approach. Once a user gains access (crosses the moat), they become trusted to use your organization’s resources (the castle). Aside from the occasional password reset or other authentication protocol, this approach leaves plenty of opportunities for outsider and insider attacks. Zero trust security, however, places a moat around every node and user. This means that no matter how often a system or user needs to access a resource, they always have to verify their identity and intent.
In other words: never trust, always verify. In our example above, implementing simple two-factor authentication could have alerted Dave to his stolen credentials, which would have prevented the attack.
The need for zero trust is due to the explosion of distributed networking. Communications used to be straightforward and centralized: a trusted user using a trusted device would connect from a trusted office location to the data center. Apps and data were securely transmitted between parties, and sealing out attackers could be as simple as deploying a new point solution or product. But user expectations changed all this; now, they need to connect from anywhere using a variety of devices, which means the modern network includes SaaS, cloud, and third-party platforms. This hybrid infrastructure means there are now more nodes and lines of communication than ever — and each is vulnerable to attack.
If the recent attacks on SolarWinds, Microsoft Exchange, and Colonial Pipeline aren’t convincing enough, consider the latest hack involving Kaseya, an American company that specializes in IT and network management software. By exploiting the virtual systems/server administrator (VSA), attackers were able to compromise up to 1,500 of Kaseya’s customers, shutting down educational services, law firms, and an outpatient surgical center in South Carolina.
Pervasive attacks like these have prompted political action, with the President signing a cybersecurity executive order this past May. Read our breakdown of the legislation and how it aims to improve cybersecurity across public and private sectors.
Now that you know why you need better security, how do you implement zero trust?
How to implement Zero Trust: The big picture
Zero trust is merely a concept, however implementing Zero Trust Network Access (ZTNA) means putting this concept to work. Implementing ZTNA involves two parts:
- The processes, which we covered in a previous post, and
- The technologies, which we’ll talk about in this post
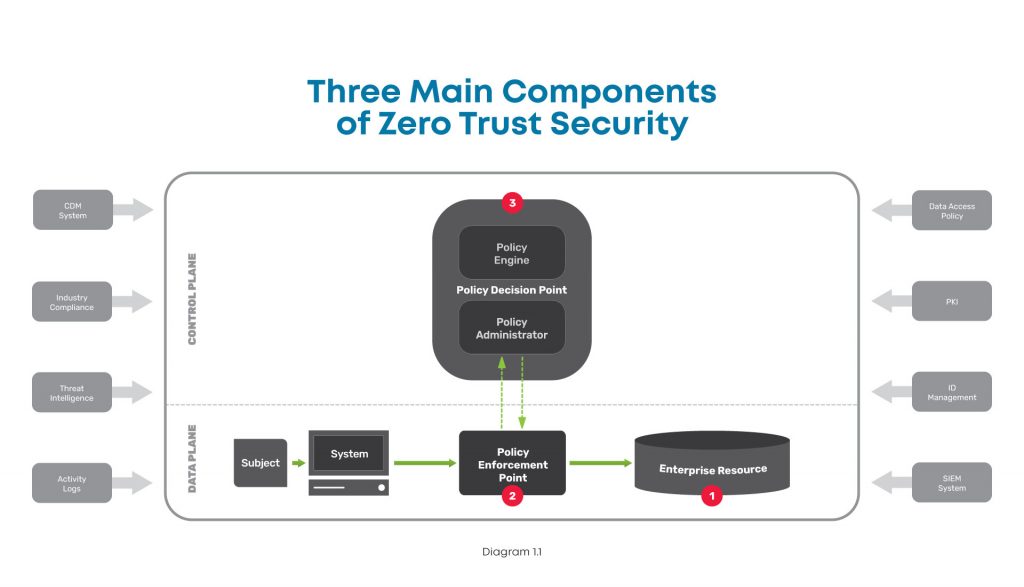
At a high level, this diagram shows the components you need when considering how to implement zero trust.
There are three major components to look at in the big picture of zero trust security:
- Enterprise resource — This includes all the IT stuff you need to protect and that your business relies on, like hardware, software, and network equipment. In simple terms, this is like the gold that you keep carefully guarded in the center of your castle.
- Policy enforcement point — This is the datapath element that enables, monitors, and terminates connections between users / devices / applications and enterprise resources. Simply put, this is like the guard that accompanies those wishing to access your gold.
- Policy decision point — This is the layer that decides who / what is safe and grants / revokes access accordingly. In other words, this is the gatekeeper who determines who is allowed into your castle.
To better understand these, here’s a closer look at each:
Enterprise resource
This component is pretty straightforward, and consists of elements you need to operate and manage IT environments. These elements can include hardware like computers and data storage devices; software such as web servers, content management systems, and operating systems; and network equipment like servers, routers, firewalls, and out-of-band devices.
Policy enforcement point
This component consists of the datapath elements that enable, monitor, and terminate connections between subjects (users / devices / applications) and your enterprise resources. Though this is represented as one component, it is comprised of two parts that are both typically used in deployments. These parts are:
- A client-side agent, usually deployed on a laptop or server.
- A resource-side gateway, which controls access in cases where a client-side agent is not used. Examples where gateways are used include regulated healthcare equipment, ATM machines, and operational technology equipment.
Policy decision point
This component is the management and orchestration layer. This layer essentially checks identities to verify who is safe, and assigns policies to determine who gets access and to what. This is also represented as one component but is comprised of two parts:
- Policy engine — This is the engine that decides whether a machine or web traffic is safe. To accomplish this, the engine uses a variety of data sources when making its determination, such as PKIs and identity management providers, CDM systems, and activity logs.
- Policy administrator — This administrator uses the policy engine’s determination to grant or revoke access to a machine or web traffic.
There are many tools available to help you monitor and visualize traffic, so you can create policies and configure your policy decision point to meet your zero trust outcomes.
In order to create your zero trust configuration, you need to deploy several essential technologies.
How to implement Zero Trust: Essential technologies
Zero trust is a complete re-imagining of network security and can be a daunting task. But when you add its fundamental technologies to your toolkit, you can effectively build the three components described above and achieve Zero Trust Network Access (ZTNA). Here are the essential technologies you need to accomplish this.
Identity and access management
Such a big part of zero trust security relies on verifying that a device or user really is who they say they are. For this, you need an identity management solution from a trusted provider and public key infrastructure (PKI). This allows you to essentially create and issue a digital fingerprint for every user, and includes information such as their username, role, and other unique data. Multi-factor authentication is a critical component of identity verification, which requires users to present two or more pieces of identification/verification before granting access.
Additionally, access management is an important piece that determines a user’s authorization level, or in other words, which resources they can access. Identity and access management both feed information into your zero trust model’s policy engine.
Policy management
Another essential technology to have is a policy management solution. This is integrated into your security stack and serves as a single policy creation point. This allows you to define access and authentication policies for your entire organization.
You can specify data access rules for users, devices, and roles, which is vital to achieving micro-segmentation, limiting lateral movement, and enforcing least-privilege access. All of these feed into your policy engine and are used by your policy enforcement point to validate whether a session is allowed to continue.
Zero trust equipment and applications
Tying everything together requires equipment and applications that are able to enforce your policies. These are physical or virtual solutions that sit in front of servers and serve as your enforcement points. For example, this could be your next-gen firewall (NGFW) that initiates the multi-factor authentication protocol, verifies a user’s identity, and uses your defined policies to restrict the user’s access to a specific segment of your network.
Where can you get these essential Zero Trust technologies?
When considering how to implement zero trust, keep in mind that there are many vendors who can provide you with the essential technologies.
- Obtaining an identity and access management solution is the easiest task when implementing zero trust. Many organizations offer an identity store, such as Azure Active Directory or Google Cloud Identity. You can also use companies dedicated to identity management, such as Duo, Okta, or Ping Identity. Keep in mind that if you need to control third-party access, such as for customers or equipment management contractors, you’ll need a solution that can access multiple identity stores simultaneously.
- Obtaining a policy management solution requires careful consideration and should be part of your overall security stack. Look for a solution that allows you to create policies and set up datapath enforcement points. An adequate framework enables you to create authentication and post-authentication access rules, with an enforcement point that segments your network and continuously authenticates sessions. This security stack can be an on-prem NGFW, or delivered via the cloud using a Secure Access Service Edge (SASE) model, both of which are available from trusted providers like Palo Alto Networks.
- Regardless of whether you use an on-prem or SASE model, you need an edge infrastructure platform to sit in front of servers and host the enforcement point. For on-prem, this platform must be able to host an NGFW to secure network segments and VLANs. For SASE, this platform must be able to create VPN tunnels to your SASE platform, which can be used for inline inspection and policy enforcement. Either approach requires powerful computing capabilities and a flexible operating system to accommodate workloads for detecting, analyzing, and automatically responding to threats, which few vendors offer.
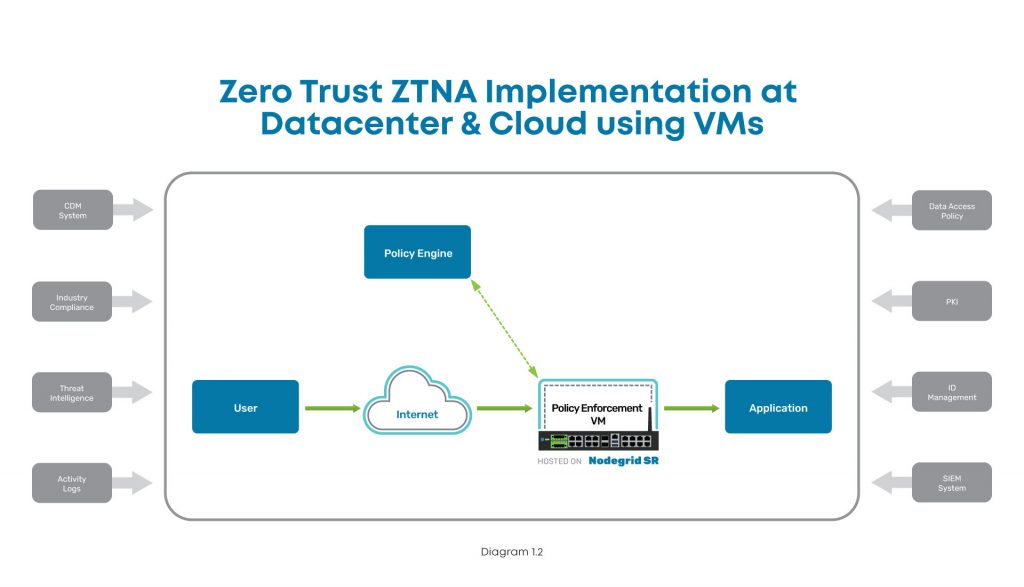
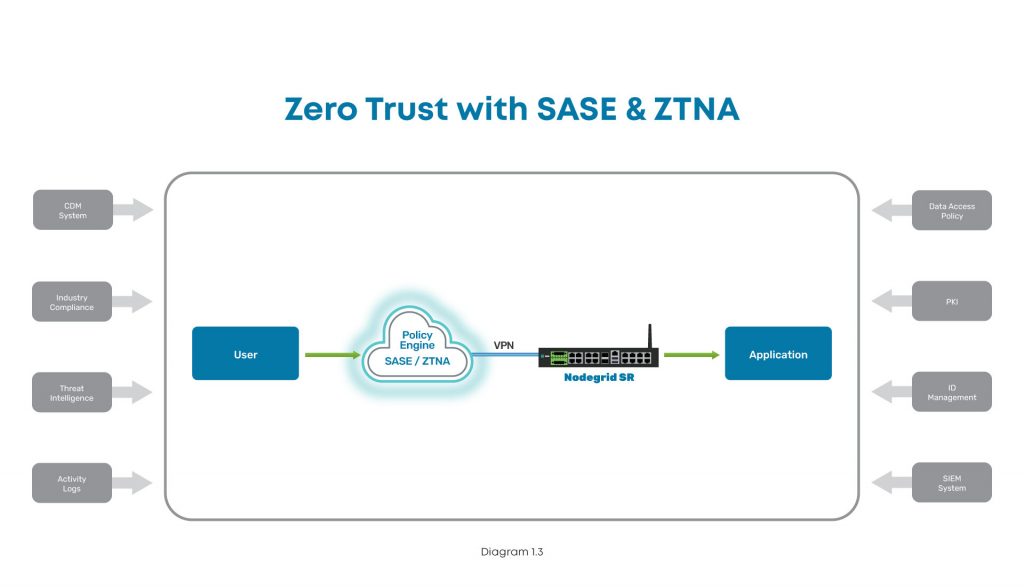
Here are examples of what proper zero trust implementations look like, with ZPE Systems’ Nodegrid as the edge infrastructure platform:
In this diagram, you can see where ZTNA and Nodegrid fit into the scheme at the data center. The user connects via Internet, and the Nodegrid SR device serves as the Policy Enforcement Point hosting a VM. This VM communicates with the Policy Engine to authenticate the user, and then grants access to the data center application.
In this diagram, the user tries to connect to an application at a branch, edge, or other distributed location. The user connects via Internet, where SASE and ZTNA provide secure connectivity. The Nodegrid SR device connects via VPN to the Policy Engine for authentication, and then grants access to the branch application.
How to implement Zero Trust: A recap
To protect your organization, implementing zero trust requires you to build out the main components. With the policy decision point and policy enforcement point in place, you can secure your enterprise resources from outsider and insider attacks. Ensuring these components work like a well-oiled machine means you need the proper identity and access management tools, a complete policy management solution built into your security stack, and equipment and applications that can enforce your zero trust security policies.
Because user expectations have caused infrastructure to become incredibly distributed and complex, the attack surface has increased dramatically. The traditional castle-and-moat approach to security is no longer adequate, and recent newsworthy cyberattacks showcase the network vulnerabilities that even the largest companies still struggle to address. The President’s latest cybersecurity executive order is a step in the right direction to bolster infrastructure protection for public and private sector entities, and you can use this blog as a starting point to begin your zero trust journey.
Don’t get caught without these 5 security must-haves
Watch our webinar, Cyberattacks: 5 Security Must-Haves for Hybrid Infrastructure Gateways, and learn how to lay a solid foundation that makes implementing zero trust easier. Our experts will talk you through how to:
- Keep edge networks and users fully protected
- Make smart buying decisions
- Get complete security and control for years of serviceability
Watch now to protect your business from growing cybercrime.