This blog describes five potential edge computing use cases in retail and provides more information about the benefits of edge computing for the retail industry.
User Management
Why Securing IT Means Replacing End-of-Life Console Servers
Rene Neumann, Director of Solution Engineering, discusses why it’s crucial to replace end-of-life console servers to protect IT.
The CrowdStrike Outage: How to Recover Fast and Avoid the Next Outage
The CrowdStrike outage on July 19, 2024 affected millions of critical organizations. Here’s how to recover fast and avoid the next outage.
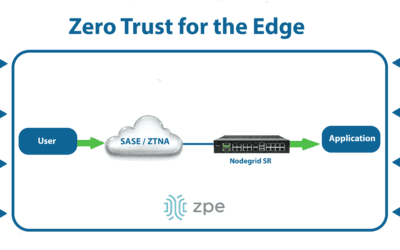
Improving Your Zero Trust Security Posture
This blog provides advice for improving your zero trust security posture with a multi-layered strategy that mitigates weaknesses for complete coverage.
DORA Act: 5 Takeaways For The Financial Sector
The Digital Operational Resilience Act (DORA Act) outlines significant resilience changes for the financial sector. See how to comply here.
What to do if You’re Ransomware’d: A Healthcare Example
Cybersecurity expert James Cabe discusses what to do if you’re on the receiving end of a ransomware attack, including isolating systems.
Best Network Performance Monitoring Tools
This guide compares three of the best network performance monitoring tools by analyzing the most critical factors and discussing the pros and cons.
Breaking Down The 2023 Ragnar Locker Cyberattacks
Many organizations suffered Ragnar Locker cyberattacks in 2023. 30-year cybersecurity expert James Cabe discusses the problem and solution.
Dissecting the MGM Cyberattack: Lions, Tigers, & Bears, Oh My!
Casino giants in the US were hit by ransomware in September 2023. Cyber expert James Cabe breaks down the attack & how to recover.
What is a radio access network (RAN)?
This post provides an introduction to radio access networks (RAN) before discussing 5G RAN challenges, solutions, and use cases.