Our way of life relies on networking infrastructure. Financial transactions, healthcare communications, national security, and everything in between depends on an interconnected web of networking and IT services. As end users, we reap the benefits of instant communications and information at our fingertips. However, this web presents an almost immeasurable amount of supply chain security risk that must be addressed, a job that’s more complex with every solution that enters the ecosystem.
What are the Impacts of Inadequate Supply Chain Security?
Insecure supply chains can lead to widespread and long-lasting consequences. We’ve seen this with backdoor vulnerabilities in firewall hardware, zero-day exploits of popular software products, and many attacks targeting the network’s control plane. The impacts can range from simple data leaks to entire regions being cut off from critical resources due to ransomware attacks.
- Economic Losses: Cyberattacks on insecure supply chains can lead to significant financial losses, both directly through theft or fraud, and indirectly through damage to reputation and customer trust.
- National Security Threats: Critical infrastructure such as power grids, transportation systems, and communication networks are prime targets for nation-state actors. Compromised networking hardware or software in these sectors can have severe implications for national security.
- Global Impact: The interconnected nature of global supply chains means that a vulnerability’s impact can ripple across the world. For example, a compromised component in one region could lead to a cascading failure in networks across multiple countries.
What Do Supply Chain Security Vulnerabilities Look Like?
When talking about supply chain security vulnerabilities in networking, this refers to different ways attackers can exploit hardware and software during manufacturing, distribution, and maintenance. These systems are essentially vulnerable during their entire lifespan – from the time their motherboards are installed and code is written, to when they’re in-transit to the customer, to when IT teams are administering regular updates and troubleshooting. But, what do these vulnerabilities look like?
Hardware Vulnerabilities
Networking infrastructure relies on hardware. Illegitimate or counterfeit components can be inserted into the supply chain and make their way into hardware manufacturing processes. This can cause equipment failures, degraded performance, or even deliberate backdoors that allow unauthorized access.
- Physical Backdoors: Malicious actors can introduce hardware backdoors during the manufacturing process, allowing unauthorized access to the network. These backdoors are difficult to detect and can remain hidden until activated.
- Long-Term Vulnerabilities: Once a compromised piece of hardware is deployed, it can remain a vulnerability for years, especially in critical infrastructure where hardware lifecycles are longer. Replacing hardware is often costly and logistically challenging.
- Trust and Reliability: Networking hardware is the first line of defense against cyber threats. Compromised hardware can lead to a loss of trust, not only in the network but also in the organizations responsible for its deployment and maintenance.
Software Vulnerabilities
Hardware provides the physical framework, while software controls and manages the flow of data within the network. Malicious code or compromised firmware can be introduced at any point in the software development lifecycle, while some software even ships with zero-day exploits (as with the MOVEit ransomware attack), leading to severe security breaches.
- Firmware Integrity: Firmware is the software that directly interfaces with hardware. If compromised, it can be used to control or disable hardware components, leading to catastrophic network failures.
- Regular Updates and Patches: Software vulnerabilities are often discovered post-deployment. Having a robust process for regular updates and patches is crucial in mitigating these risks. However, if the update process itself is compromised, malicious actors can introduce vulnerabilities under the guise of legitimate updates.
- End-to-End Encryption: Secure software ensures that data transmitted across the network is encrypted, reducing the risk of interception or tampering. This is especially critical in protecting sensitive information from being accessed by unauthorized entities.
- Third-Party & Open Source Software: Third-party and open source software are used throughout networking infrastructure. When this software is integrated into the ecosystem, it can introduce vulnerabilities and code quality risks, especially if the organization doesn’t have access to the underlying code.
Third-Party and Insider Threats
Most companies rely on third-party vendors and suppliers, whether for hardware manufacturing, procurement and logistics, or software development. This adds layers of complexity. If any of these third parties are compromised, the impact can ripple throughout the entire supply chain and contaminate the end products.
Employees or contractors can also put infrastructure integrity at risk. When these employees are trusted with access to sensitive parts of the supply chain, they can compromise overall security, even unintentionally.
How ZPE Systems Shrinks Supply Chain Security Risks
ZPE Systems provides the network management infrastructure that’s essential to managing critical IT for organizations across industries. Although there are many network management infrastructure vendors, most lack a holistic approach to security. Hardware components may be sourced from untrusted manufacturers, and software development may be loosely-controlled and inadequately tested. These parts of the supply chain introduce vulnerabilities that can put customers at much more risk than they realize.
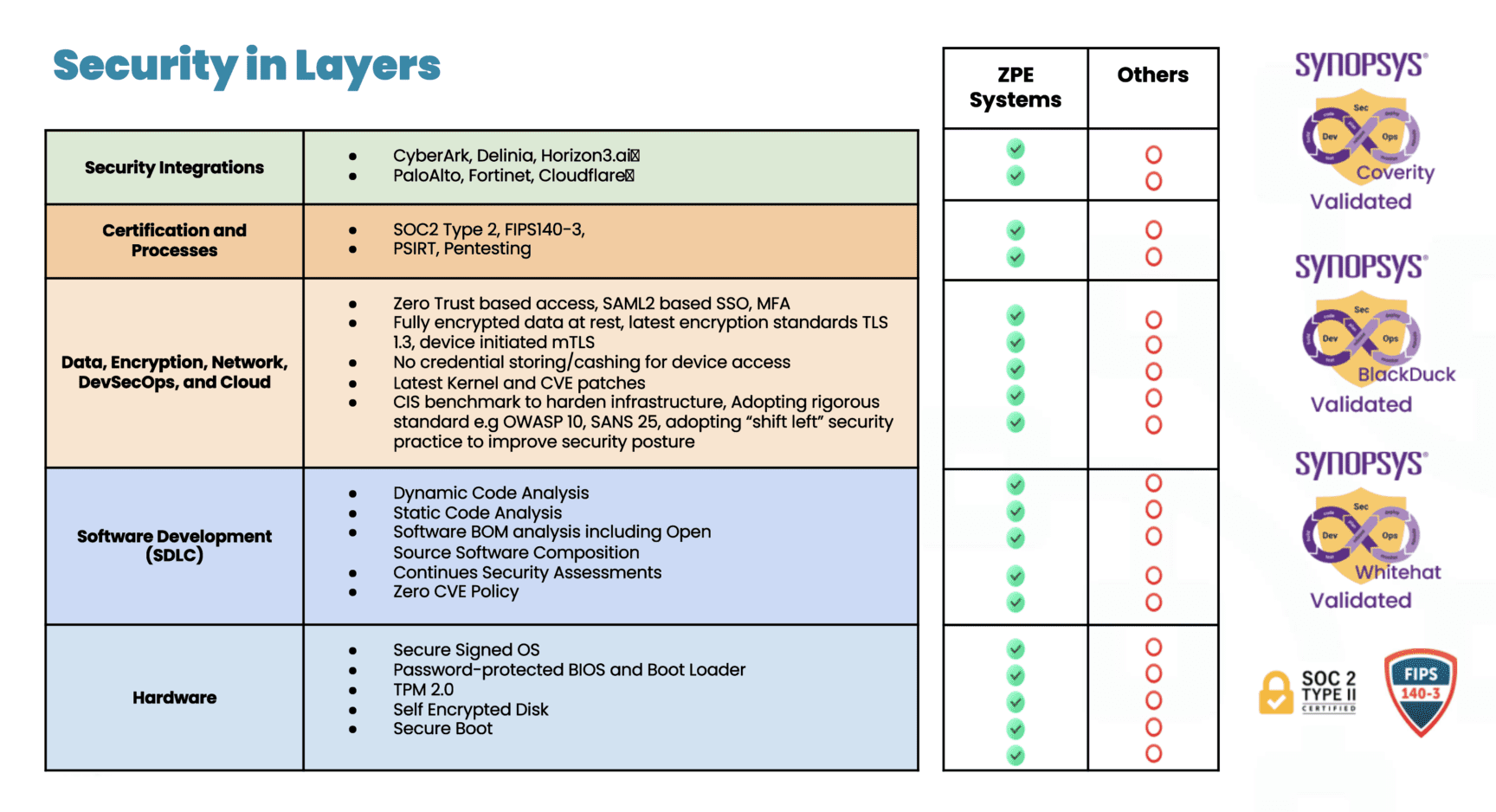
ZPE takes a security-centric approach and offers the industry’s most secure out-of-band management platform. This includes dozens of hardware security features, a Synopsys-validated software development lifecycle, and the most third-party certifications and validations, including FIPS 140-3, SOC 2 Type 2, ISO 27001, and others.
Get the full breakdown of our end-to-end supply chain security approach by downloading the pdf below.
Learn More About Cybersecurity With This Video
James Cabe, a 30-year cybersecurity expert, presented at the 9th America Digital expo in Mexico City. He talked about the three main threat actors from around the world, and showed how organizations can bring more resilience to their critical IT using something called Isolated Management Infrastructure (IMI). Watch James’ full presentation below and get practical advice for implementing IMI.