
Many organizations already use redundant and backup systems for disaster recovery and assume this makes them resilient. However, these measures aren’t able to withstand many major events like ransomware attacks, supply chain failures, and WAN outages. This article compares network resilience vs. redundancy and backups and describes some of the tools and best practices for ensuring resilience.
Network resilience vs. redundancy vs. backups
What are backups?
Backups are extra copies of critical data, configurations, and application code that are made in case the originals are lost or compromised. Backups are usually stored off-site so that they’ll be available if the primary data center or business location suffers an outage. The backup site communicates with the primary systems to download data on a scheduled or continuous basis to maintain a secondary copy of data at its most current state. This connection, while necessary, also allows ransomware and other malware to infect backups, which limits their usefulness in recovery operations. Additionally, if that connection is interrupted by an outage or configuration error, backups may be incomplete or inaccessible.
What is redundancy?
Redundancy involves duplicating the most critical systems, services, and applications so organizations can “failover” to them if the primary systems go down or become inaccessible. Typically, a company will have redundant systems in one or more disaster recovery sites in different locations to prevent a regional ISP outage or weather event from affecting them all at the same time. If one site goes down, teams reroute traffic to a redundant site to continue delivering services. However, each redundant site is susceptible to the same risks as the primary site, and cybercriminals and malware could potentially jump from one site to another.
What is network resilience?
Network resilience is the ability to continue operating and delivering core services – if in a degraded state – during adverse events. Backups and redundancy contribute to resilience, but there are additional pieces to the puzzle. Teams also need the ability to recover data, rebuild systems, and perform security testing without worrying about ransomware reinfection or access disruption. Additionally, organizations must be able to protect management interfaces from cybercriminals on the network, or they could become completely cut off from vital systems and services.
The best way to improve resilience is by building a resilience system containing all the infrastructure, tools, and services needed to continue delivering services and recover failed or compromised systems. It must be isolated from the production network using isolated management infrastructure (IMI) to prevent malicious actors from compromising it and ensure teams have continuous remote access even if the primary network goes down.
Read more about ransomware resilience with IMI:
Resilience systems use the following tools, technologies, and best practices to provide network resilience.
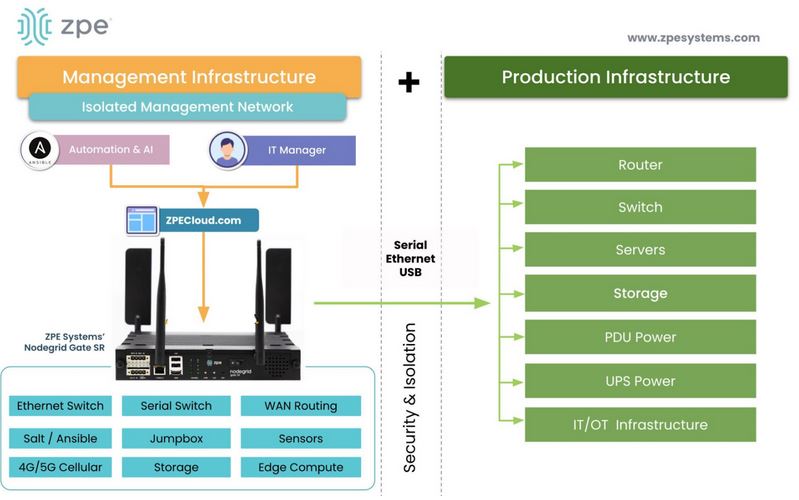
Network resilience with ZPE Systems
Want to learn more about using Nodegrid to build network resilience vs. redundancy and backups? Our Network Automation Blueprint provides a step-by-step guide to building an IMI resilience system.
