As enterprise networks increase in complexity and distribution, and the frequency and severity of cybersecurity incidents also continue to grow, organizations must rethink traditional approaches to network security. That’s where the zero-trust methodology comes in.
What is zero trust security, you ask? This post defines the term and discusses its history before providing a guide to implementing zero trust security in your organization.
Table of Contents |
What is zero trust security?
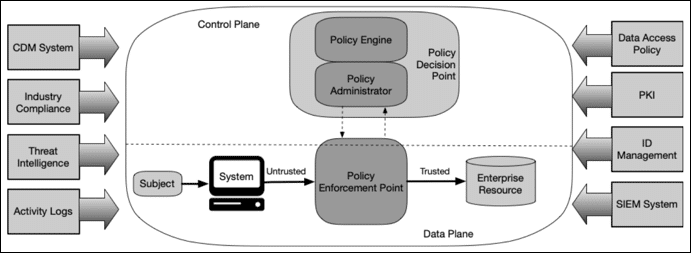
Zero trust is a network security protocol that embraces two main principles. The first lends its name and stipulates that networks must “never trust, always verify” any device or account, including those already within the network perimeter. As a result, a zero trust security framework requires any entity accessing network resources to successfully authenticate through a root-of-trust and strong authentication method (e.g., one-time passwords or 2-factor authentication).
The second pillar of a zero trust network is micro-segmentation. Instead of a singular, all-encompassing security perimeter, a zero trust approach uses the same strong authentication and highly specific security policies to establish trust at checkpoints along smaller, segmented perimeters. This combination limits the lateral movement of compromised accounts, which minimizes the impact of breaches and aids in protection, governance, and compliance.
The history of zero trust security
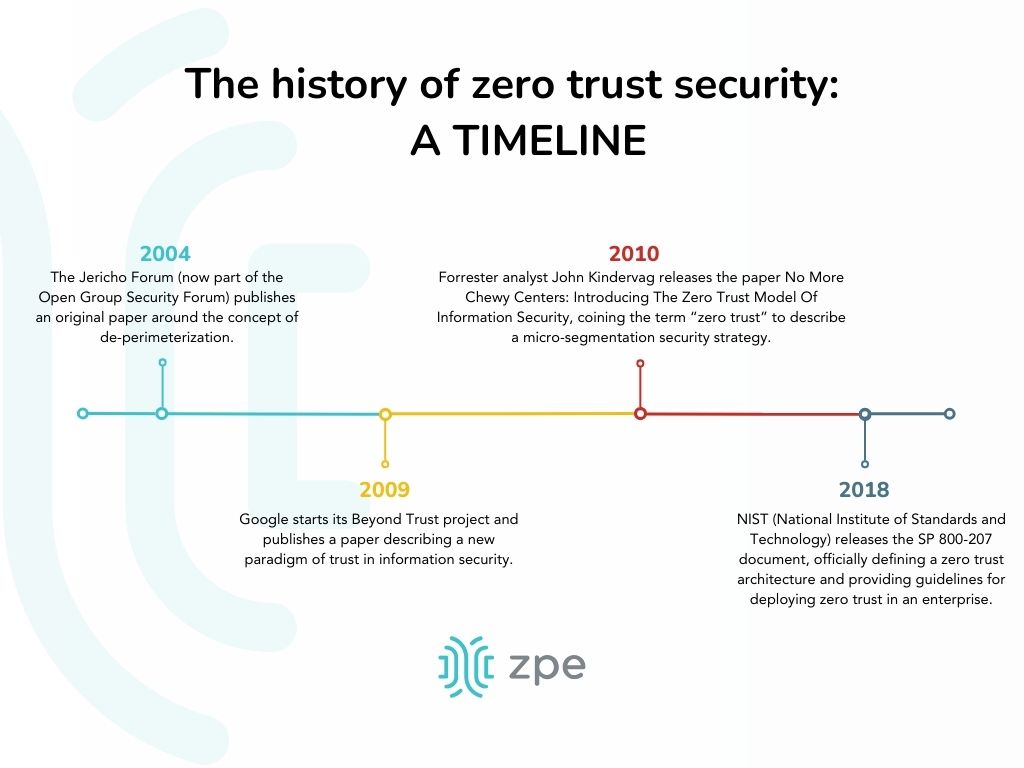
The NIST publication answered the question, “What is zero trust security?” using seven core tenets.
| 7 tenets of zero trust security |
|
Zero trust security benefits
One of networking’s fundamental goals is to allow information to flow between computers, people, and organizations. However, that information is more decentralized now than ever before and must be relayed through various applications, partners, and third-party channels, increasing risk. Plus, the frequency of ransomware attacks and other highly sophisticated cybercrimes makes it a near certainty that a breach will occur even with the best protection strategies.
The zero trust security model operates under the assumption that a breach is already in progress, meaning an account or device is already compromised and accessing the network. It works to restrict an attacker’s movement on the network by erecting security checkpoints around each potential target and forcing them to re-establish trust. Limiting the blast radius of a cyberattack decreases the duration and cost of recovery operations so organizations can minimize the impact on their revenue and reputation.
| 4 benefits of zero trust security |
|
Zero trust security use cases and examples
Organizations across any industry can benefit from the zero trust approach to network security. For example:
- Ransomware often exploits vulnerabilities in unpatched software to compromise enterprise systems and move around the network, encrypting critical resources along the way. Establishing zero trust checkpoints at each micro-perimeter can help identify compromised resources and prevent their lateral movement, limiting the impact of ransomware and expediting recovery.
- Operational Technology (OT) is used to automate machines that interact with the real world, such as HVAC systems or industrial robotics, which makes OT-related cyberattacks uniquely devastating. With recent reports indicating these attacks are on the rise, many organizations are using zero trust policies and controls to secure both their OT and their IT networks.
- Many organizations use Internet of Things (IoT) devices to collect data, provide mobile services, automate critical operations, and more. However, these devices are a huge cybersecurity risk if not managed properly, especially in the financial sector and the medical industry. Zero trust security helps mitigate the risk by making it easier to identify compromised IoT devices and deny access to sensitive resources.
How to implement zero trust security
With an understanding of what zero trust security is, where it came from, and how it can be used, you can create an implementation plan that includes all the tools and processes you must deploy to achieve the zero trust model. There are four key questions to answer:
- How will we establish trust?
- How will we control and secure user access to resources?
- How will we identify and manage our attack surface?
- How will we enforce zero trust and detect attackers on the network?
Let’s discuss the best way to answer each of these questions and the natural progression to establishing a zero trust implementation plan.
1. Establishing trust
As the core of the zero trust strategy, this must be addressed before moving on to any subsequent steps. Establishing trust requires four things, implemented in this order:
- Roots of Trust (RoTs) – Roots of Trust are hardware security mechanisms that provide cryptographic functions, key management, and other important features. An example would be a Trusted Platform Module (TPM). RoTs are inherently trusted and provide the foundation on which to build a zero trust security architecture, so it’s critical to choose solutions that provide the best and most up-to-date security features.
- Identity and Access Management (IAM) – An IAM solution provides policy creation and deployment, identity verification, and trust assessment functionality. It acts as the gateway at each micro-perimeter, forcing accounts to verify their identity and re-establish trust before accessing enterprise resources.
- Strong authentication – A password alone isn’t enough to prove someone’s identity, so strong authentication requires a secondary form of proof. Examples include one-time passwords (OTPs), authentication app keys, physical keys like USBs or smart cards, and biometric scans.
- Privileged Access Management (PAM) – Similar to IAM, privileged access management focuses specifically on accounts with special access rights, such as sysadmin or service accounts.
2. Controlling access to resources
The next step is to establish control over who can access network resources and ensure that access is secured. The four areas to focus on, in order, are:
- Access control policies – Zero trust requires highly specific policies that are custom-tailored to the resources being protected. The best practice is to use role-based access control (RBAC) instead of assigning individualized permissions to each account.
- Threat intelligence – Threat intelligence refers to the information used by organizations and cybersecurity vendors to learn about threats to the network. This knowledge is used to determine which security solutions and controls are needed to defend specific network micro-perimeters.
- Risk management – Risk management involves using threat intelligence and other sources of information to determine how risky it is to deploy particular technology solutions, work with specific third-party partners, or allow access to particular areas of the network.
- Zero Trust Network Access (ZTNA) – ZTNA provides secure remote access to enterprise resources, similar to (but better than) a VPN. ZTNA connects remote users directly with the specific resource they’re requesting to access without letting them see or interact with anything else on the enterprise network.
3. Managing the attack surface
Creating effective micro-perimeters is impossible without a clear understanding of what’s being protected and what the potential risks are. This involves four components:
- Asset management – You must have a total accounting of all the assets on the network, including information about software versioning, patch schedules, hardware security capabilities, and location.
- Vulnerability management – Vulnerability management involves monitoring, discovering, reporting, and resolving software vulnerabilities. A robust vulnerability management strategy is required to prevent malicious actors from using software exploits (like the unpatched Accellion vulnerability) to bypass zero trust security controls.
- Software Bill of Materials (SBOM) – A software bill of materials lists all the various third-party and open-source components present in a given software product. An SBOM is required to gain a full understanding of the risks associated with a particular solution and determine which policies and controls are required to defend it.
- Attack surface management – Attack surface management involves identifying all the potential targets of a cyberattack, implementing policies and controls to defend those targets, and continuously monitoring for new threats. Effective attack surface management requires robust asset & vulnerability management as well as SBOMs for all software, so all previous processes must already be in place prior to this step.
4. Enforcing zero trust and detecting attacks
The final stage of zero trust implementation involves enforcing policies, detecting threats on the network, and dealing with those threats. These processes, in order, include:
- Zero trust enforcement – You enforce zero trust policies using all the tools, processes, and information from previous steps. Many organizations adopt artificial intelligence (AI) and machine learning (ML) technologies for greater visibility into account activity. For example, User and Entity Behavior Analytics (UEBA) solutions monitor and analyze behavior so they can better detect anomalous account activity.
- Threat detection – Threat detection involves monitoring the network to identify signs of attack, like malware execution, data exfiltration, repeated failed access requests, and unapproved registry changes.
- Deception – Zero trust deception technology uses an overlay of “false” attack targets to lure malicious actors into revealing themselves and their motives without allowing them access to any real resources.
Source: NIST Special Publication 800-207 (Zero Trust Architecture)
It’s important to note that all of the steps and processes listed above must be followed chronologically because each successive stage builds upon the one before. It isn’t until all these steps are complete that an organization has achieved the zero trust security model.
Zero trust on the control plane
The management interfaces used by administrators to control network infrastructure are often excluded from zero trust implementation plans because end-users don’t typically access them. That means a compromised sysadmin account could potentially hijack the control plane and bring down critical infrastructure.
Organizations must apply zero trust security principles, policies, and controls to management infrastructure. The best practice, according to a recent CISA directive, is to keep the control plane on an isolated, out-of-band (OOB) network – also known as an Isolated Management Infrastructure (IMI). Isolating the management interfaces on a dedicated network prevents lateral movement to or from the production LAN. It also gives administrators a safe environment in which to recover from ransomware or other cyberattacks without risking reinfection; this is known as an isolated recovery environment (IRE).
The easiest and most effective way to implement an IMI is with OOB serial console servers. Ideally, these devices should have robust Root of Trust technology like TPM 2.0, use alternative network interfaces like 5G/4G cellular to ensure isolation and continuous access, and integrate with zero trust solutions such as IAM and PAM for consistent policy enforcement.
| Learn more about zero trust on the control plane |
Zero trust security simplified
What is zero trust security? It’s both a mindset and a set of innovative technologies and cybersecurity methods that address the current threat landscape of frequent, sophisticated, and disruptive attacks on networks of all sizes. By following the principle of “never trust, always verify,” and using the implementation steps outlined above, you can defend your network and streamline recovery operations.
Are you looking for a way to simplify zero trust without sacrificing security? The Nodegrid platform from ZPE Systems includes a range of all-in-one solutions that combine LAN/WAN/Branch networking, out-of-band (OOB) management, zero touch provisioning (ZTP), and more. Nodegrid solutions are vendor-neutral and can run or integrate your choice of third-party zero trust solutions like IAM and ZTNA, reducing the number of security devices to deploy at each office or branch. Nodegrid boxes are protected by strong Root of Trust technology like TPM 2.0 and employ innovative security features like geofencing to form a robust foundation for your zero trust implementation.
What is zero trust security?
Learn more or request a demo of the Nodegrid solution by contacting ZPE Systems today.