
Out-of-band management (OOBM) is a network resilience strategy that involves moving the control plane of critical infrastructure, such as routers, switches, and servers, to a separate network. Doing so isolates the control plane from the production network so it won’t be negatively affected by equipment failures, ISP outages, or ransomware attacks.
This guide describes two out-of-band deployment types and highlights three key best practices to maximize network resilience.
Out-of-band deployment types
✔ Lower cost
✔ Reduced management complexity
✘ EoR device is a single point of failure for the row
✘ Cable management is messier
✘ Less flexibility
✔ Eliminates a single point of failure
✔ Provides greater flexibility to modify, upgrade, or scale
✘ Requires more OOBM switches
✘ Additional switches could affect throughput, power draw, and cost
✘ Increases management complexity
End-of-row OOBM deployments
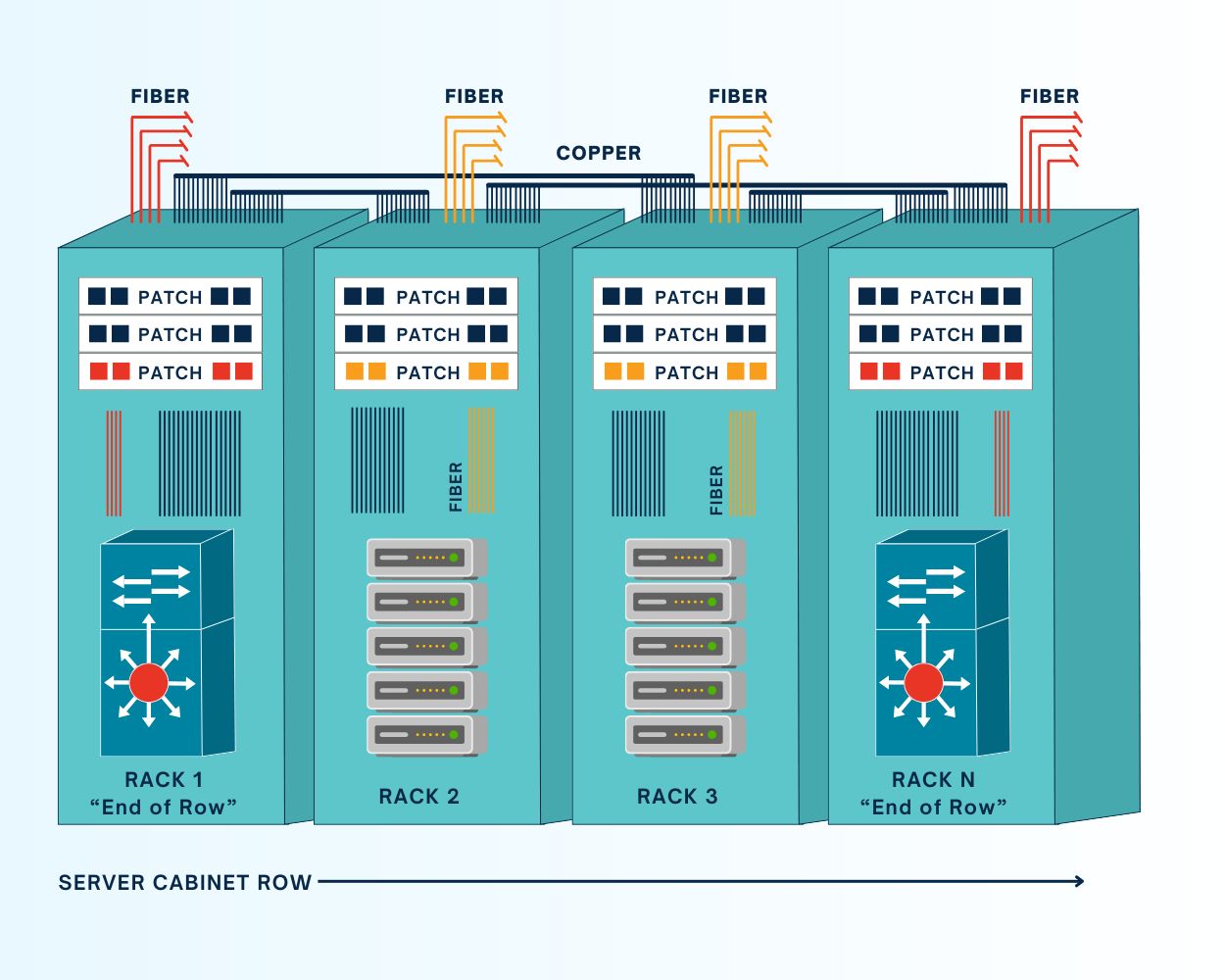
In an end-of-row (EoR) out-of-band deployment, one or more OOBM switches are installed in every row of data center infrastructure, rather than in every single rack. All the serial cables for infrastructure devices in a particular row are run to wherever the OOBM switch (also known as a serial console or console server) is located, which is typically at the end of the row.
An EoR deployment requires fewer OOBM devices than a ToR deployment, which reduces costs and management complexity. It also simplifies scaling, as new racks full of infrastructure could be added to the row without requiring additional OOBM serial consoles.
On the other hand, that one serial console becomes a single point of failure for the entire row’s OOBM functionality. If that device becomes unavailable because of a botched update or malware attack, management teams lose OOBM access to the entire row. Cable management is also more difficult because serial cables must run from every device in every cabinet to the EoR console server. Plus, EoR deployments are less flexible, because upgrading or swapping out a single OOBM device affects an entire row of infrastructure.
Top-of-rack OOBM deployments
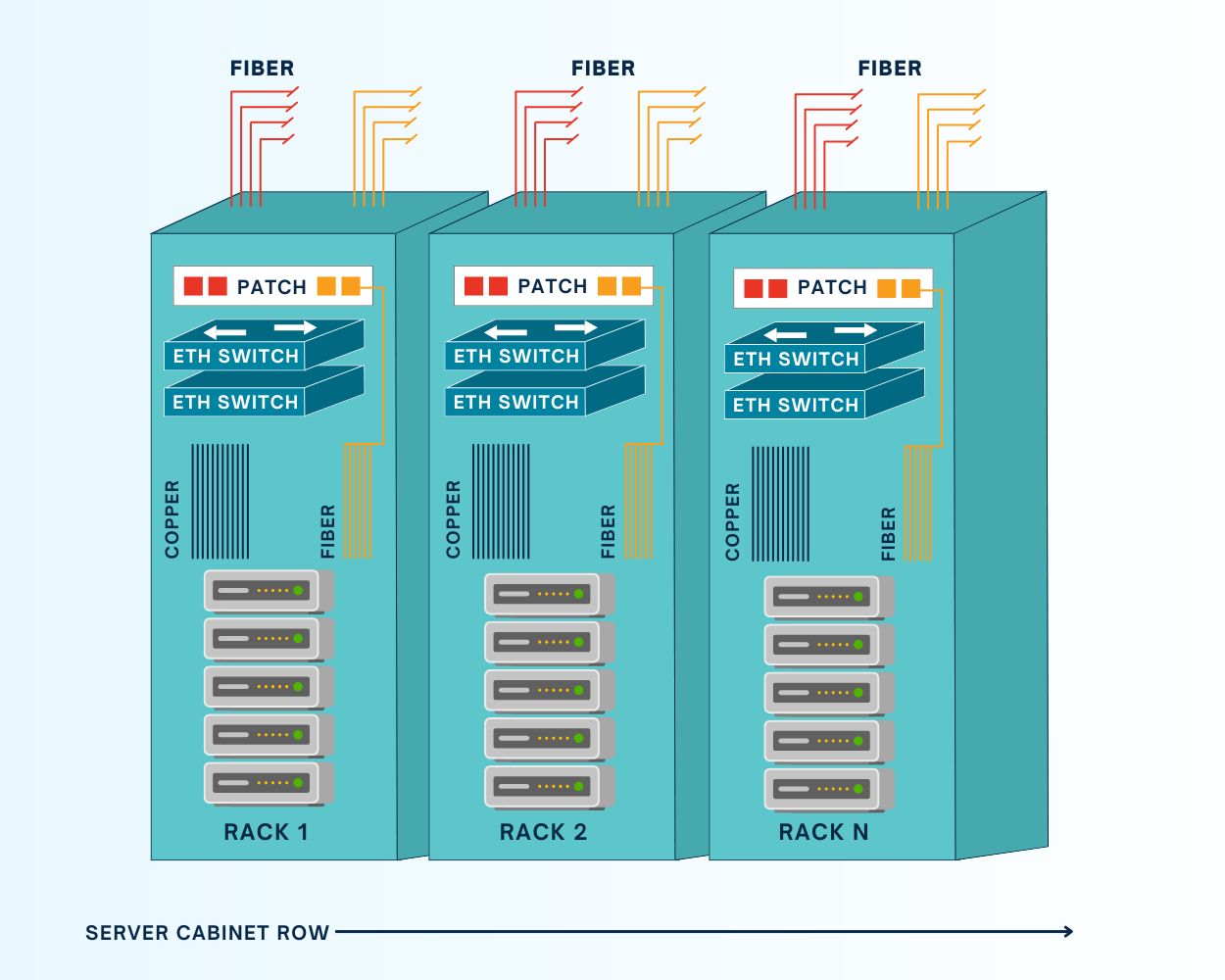
In a top-of-rack (ToR) out-of-band deployment, one or more OOBM switches are installed in every single rack in the data center. This keeps all serial cables inside the rack, which simplifies cable management. Instead of a single point of failure for the whole row, each serial console only affects one rack, enhancing resilience. Teams can also upgrade or swap out devices without worrying about what’ll happen to the entire row, making ToR deployments a little more flexible.
The main drawback of a top-of-rack deployment is that it requires more OOBM console servers than an EoR architecture. This makes OOBM deployments more expensive and adds more devices for teams to manage and monitor. It also increases the power draw in the data center, further driving up costs (and carbon footprints), and adds more network hops to local traffic, which could affect throughput.
Multi-layered OOBM deployments
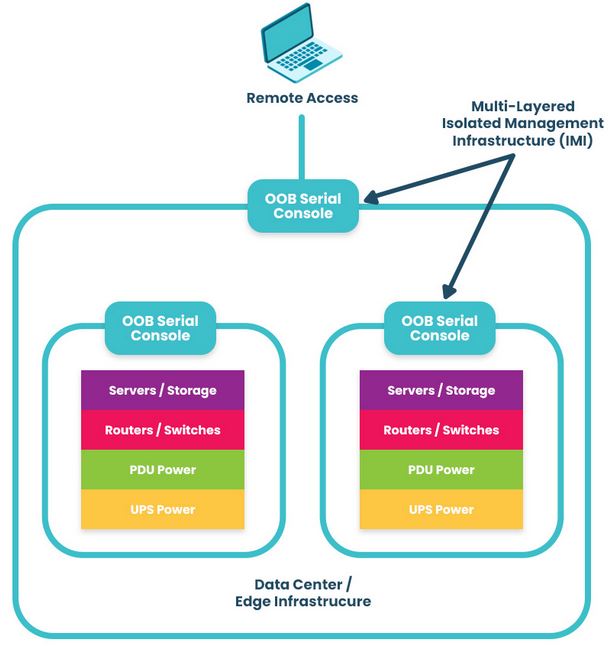
A third, less common approach is to deploy OOBM devices both top-of-rack and end-of-row. This makes the OOBM network highly resilient to both outages and ransomware attacks, providing a completely isolated management environment while maintaining the flexibility of a ToR deployment.
Out-of-band deployment best practices
The following best practices can help improve the flexibility, security, scalability, and resilience of out-of-band deployments.
Vendor-neutral platforms
Using vendor-neutral OOBM console servers helps consolidate data center management in a single platform. These devices can manage infrastructure from any vendor and integrate with third-party solutions for security, automation, troubleshooting, and more. Vendor-neutral OOBM deployments reduce management complexity and costs, while ensuring easy scalability.
OOBM security
OOBM devices and networks must be protected against compromise to keep bad actors from commandeering the control plane. The best practice is to use OOBM switches with strong hardware security, SAML integrations for multi-factor authentication (MFA) and single sign-on (SSO), embedded firewalls, and frequent firmware/software updates to patch new vulnerabilities.
Infrastructure automation
OOBM serial consoles should support automation to improve scalability and efficiency, while reducing complexity and recovery times. At a minimum, they need zero-touch provisioning (ZTP) to automatically configure new infrastructure devices over the network. Advanced solutions like the Nodegrid Serial Console Plus can also host or integrate third-party automation for things like configuration management, security monitoring, troubleshooting, and even AIOps.
Streamline your out-of-band deployment with Nodegrid
Nodegrid OOBM switches can be deployed top-of-rack, end-of-row, or both to improve the resilience of any data center architecture. They have an open architecture that can integrate and host other vendors’ software and virtualized network functions for security, automation, and much more. Nodegrid serial consoles and all connected devices can be remotely managed from a single, on-premises or cloud-based software platform, significantly reducing management complexity. Plus, Nodegrid is frequently patched and comes back with security features like BIOS protection, UEFI Secure Boot, self-encrypted disk (SED), Trusted Platform Module (TPM) 2.0, an embedded firewall, and SAML 2.0 integrations.
Reach out to ZPE Systems for more help comparing end-of-row vs. top-of-rack deployments or to see a demo of the Nodegrid platform in action.
