
Managing and securing operational technology (OT) is notoriously challenging because of stakeholder focus on continuity and safety. This is only becoming more difficult as OT systems and networks grow more complex and distributed. Operational technology is a rare but valuable target of cyberattacks due to the severe impact on business operations and a relative lack of cybersecurity monitoring due to physical security requirements and GRC. It is simply harder to blend cybersecurity into operational security when the stakes are high and availability and continuity are the prime focus.
Early attempts to apply IT-specific security controls to OT had mixed success. A particular tool may work well in one scenario, but fail in another project. Some solutions meant to simplify OT management, such as NMAP (or Network Mapper), could even turn into weapons in the wrong hands. For example, the AvosLocker ransomware variant uses NMAP NSE (NMAP Scripting Engine) to scan endpoints for the Log4shell vulnerability and select targets to exploit.
This guide defines OT, explains how to overcome some of the biggest operational technology security challenges, and discusses the importance of recovery in building resilience in OT.
| Table of Contents: |
What is operational technology (OT)?
Operational technology (OT) includes any equipment interacting with the real world, as well as the systems that control such equipment. Some examples of OT equipment include HVAC systems, door controls, industrial machinery, fluid system sensors, and medical robotics. Examples of OT control systems include programmable logic controllers (PLC), supervisory control and data acquisition systems (SCADA), building management systems (BMS), and building automation systems (BAS). These control systems enable a high degree of automation in fields like industrial manufacturing, water and energy utilities, building management, and medicine.
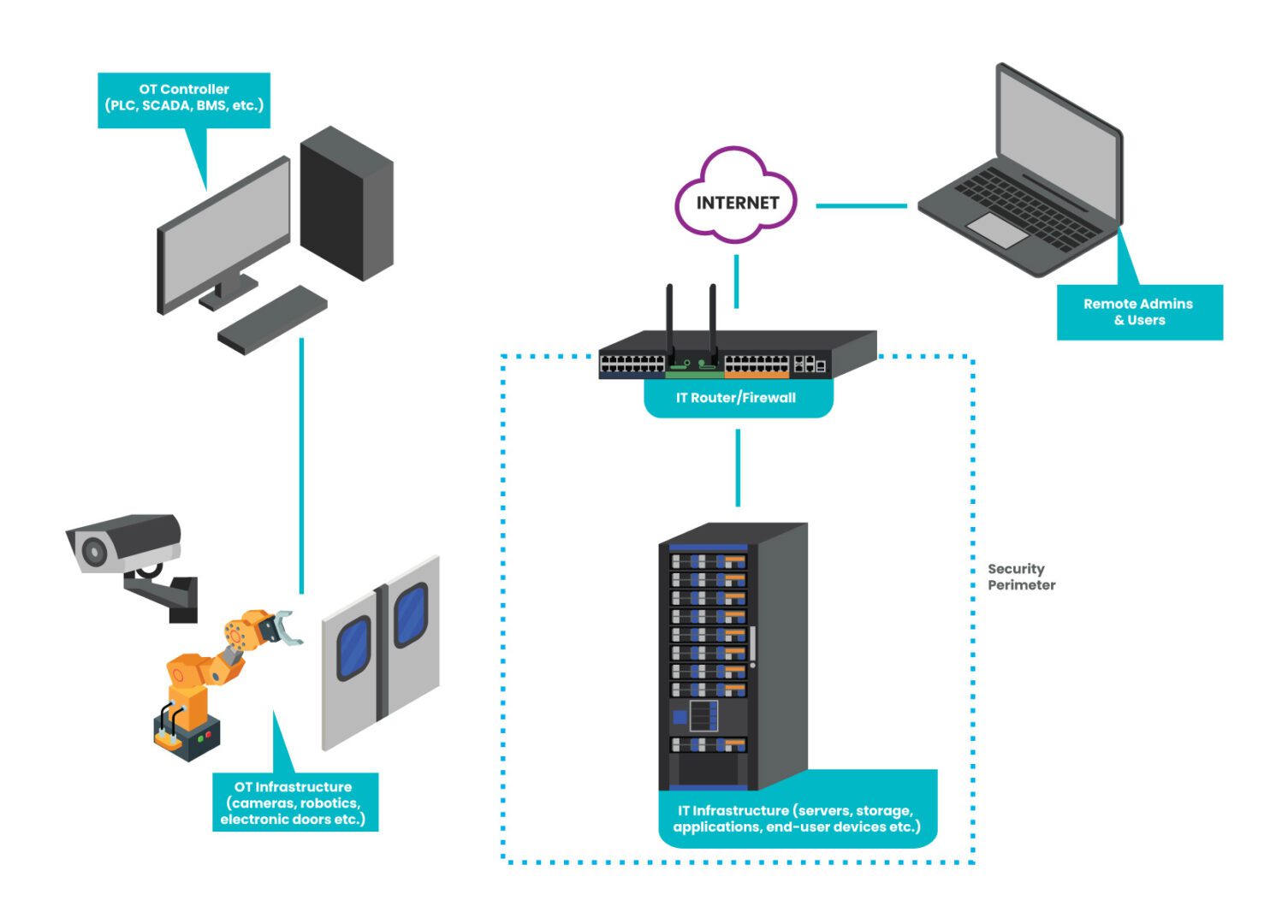
Figure: An example of how a typical OT network is isolated from the IT network & security infrastructure.
Operational technology security challenges & solutions
It’s tempting to believe that operational technology is safe from cyberattacks because it’s often isolated from the IT network—the “security through obscurity” approach. However, OT is a very tempting target for malicious actors because it’s so critical to business operations. Recent research from Barracuda Networks found that over 90 percent of manufacturing organizations experienced cyber attacks on their production or energy supply in 2021. An OT attack can completely halt manufacturing lines, interrupt oil and gas supplies, or prevent life-saving procedures from taking place.
Operational technology security is a crucial focal point, but significant challenges exist.
Challenge: OT security tools are a double-edged sword
Network Mapper, or NMAP, is a widely-used network management tool. NMAP started as a simple scanner in 1997 but evolved over the years into a solid open-source tool for OS detection, software version detection, and other network discovery features. NMAP aids in OT security by mapping exposed operational technology controls for teams to patch and secure. However, in the wrong hands, this tool could be used in intelligence gathering to attack vulnerable, out-of-date systems.
The problem with tools like NMAP is that they only discover information about systems with open ports on the same network as the tool – usually the production network. If an authorized network admin can find OS versioning information on the production network, so can an unauthorized user with stolen credentials.
Security teams need an efficient way to discover, patch, and manage operational technology without exposing these systems to cybercriminals.
Solution: Out-of-band (OOB) OT management
An out-of-band (OOB) network uses dedicated network infrastructure to create a control plane that’s completely isolated from the production network. An out-of-band serial console is the most efficient way to create an OOB network. This device directly connects to OT equipment and control systems via management ports (e.g., RS232 Serial), allowing administrators to monitor and patch vulnerabilities without exposing OS/versioning information to production.
An OOB serial console also uses alternative network interfaces—such as LTE cellular or dial-up—to ensure this management network is always remotely accessible by administrators, even when the production ISP, WAN, or LAN goes down from a failure or breach. With this added redundancy, teams can recover and restore critical OT operations much faster, even when the outage occurs in a remote or hard-to-reach location.
An out-of-band OT management solution provides efficient patch management without exposing vulnerable systems to cybercriminals. OOB also streamlines OT recovery efforts to minimize the impact of successful attacks and other failures.
| Out-of-Band (OOB) Management Learning Center |
Challenge: OT isolation hinders disaster recovery and Zero Trust
Since operational technology is often isolated from the IT network on its own LAN, there usually isn’t any way to access the control systems remotely. Operators must be on-site to use SCADA or PLC systems to monitor and control industrial processes. If on-site access is impossible, for example, due to a global pandemic or natural disaster, OT operations completely shut down. For example, increased tornadoes, floods, and other natural disasters in the midwest have forced major companies like General Motors and Amazon to close regional plants and logistics centers. When workers are sent home, operations grind to a halt unless operators have a way to access their OT control system remotely.
In addition, this separation makes it difficult to extend Zero Trust to operational technology. Without strong authentication, granular security policies, and targeted protection, there’s a significant risk of breaches. Plus, a lack of Zero Trust makes it difficult to contain the lateral movement of a malicious actor who’s using stolen credentials, which increases the blast radius and business impact of cyber incidents.
Organizations need a way to minimize operational disruptions from natural disasters and apply Zero Trust to OT networks if they want to improve their resilience.
Solution: IT/OT convergence with vendor-neutral platforms
IT/OT convergence involves bringing information technology and operational technology together under one management umbrella and securely bridging the gap between the two networks.
An IT/OT convergence strategy improves business resilience in two ways:
- It brings OT onto the same enterprise network as IT systems which facilitates the use of remote tools (like VPNs or ZTNA), giving operators access to OT control systems from off-site
- It brings OT within the purview of Zero Trust security controls like multi-factor authentication (MFA), identity and access management (IAM), and deep packet inspection (DPI)
The easiest way to achieve IT/OT convergence without gaps is to use a vendor-neutral management and orchestration platform. For example, an OOB serial console with an open OS architecture that can dig its hooks into multi-vendor OT systems will give administrators a single-pane-of-glass view of the converged IT/OT infrastructure. A platform that can host or integrate 3rd party Zero Trust solutions will also enable unified orchestration of IT and OT security.
By converging IT and OT, organizations can keep business running during natural disasters and limit the blast radius of breaches. A vendor-neutral platform also provides unified security orchestration for greater coverage and improved efficiency.
Operational technology security & resilience
A comprehensive operational technology security strategy will help improve resilience by preventing some cybersecurity incidents and reducing the impact of the rest. However, it’s impossible to ensure 100% protection, especially with ransomware attacks on the rise. That’s why it’s important to distinguish between security and resilience; security provides preventative measures, but resilience is your ability to withstand adversity and keep business flowing.
One of the best measures of resilience is how quickly you can recover from outages caused by failures and attacks. And the best way to ensure a speedy recovery, according to the experts at Gartner and the CISA, is by using isolated management infrastructure such as OOB serial consoles to create an isolated recovery environment (IRE). This gives teams a dedicated environment, insulated from ransomware and production failures, where they can rebuild and restore critical services.
Download our whitepaper 3 Steps to Ransomware Recovery for more guidance on streamlining IT/OT recovery and improving business resilience.
Building OT security & resilience with Nodegrid
The Nodegrid platform from ZPE Systems is a complete resilience solution that delivers OOB operational technology management and vendor-neutral IT/OT convergence. Using Nodegrid out-of-band solutions as your isolated management infrastructure ensures teams will have 24/7 remote access to monitor, patch, troubleshoot, and recover operational technology. The open, Linux-based Nodegrid OS supports VM and container hosting and easy integrations so you can deploy and control 3rd party applications for Zero Trust, OT management, and more from a single platform. Nodegrid can also host all the tools your team needs to recover and rebuild critical services — including to fully destroy and rebuild production networks — making it the perfect solution for building an isolated recovery environment.
Nodegrid can also run 3rd-party automation solutions such as software-defined networking (SDN)/software-defined wide area networking (SD-WAN), infrastructure as code (IaC), and artificial intelligence for IT operations (AIOps). Automating workloads helps reduce the risk of human error, while automating root-cause analysis (RCA) and security event analysis can significantly speed up recovery efforts, creating a more resilient network.
Learn how Nodegrid delivers unified orchestration and out-of-band management!
Nodegrid delivers unified orchestration and out-of-band management to help you build your zero trust security architecture. Contact ZPE Systems today to learn more.
