This guide to out-of-band management answers critical questions about what this technology is, why you need it, and how to choose the right solution.
Month: January 2024
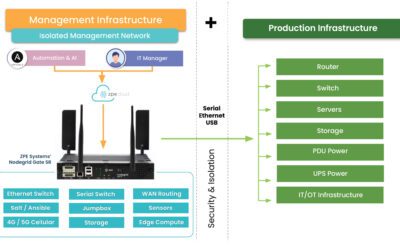
Why network resilience requires Isolated Management Infrastructure
Isolated Management Infrastructure is the key to modern network resilience. Read about the gaps of existing approaches and why Big Tech trusts IMI.
Network Resilience Doesn’t Mean What it Did 20 Years Ago
Network resilience requirements have changed. James Cabe discusses why the new standard is Isolated Management Infrastructure.
Centralized Fleet Management with Device Clustering – Tech Talk Tuesday from ZPE Systems
Todd Atherton (Channel Sales Director) and Marc Westberg (Channel Sales Engineer) walk you through Nodegrid’s device clustering capabilities that let you get convenient, centralized management of your distributed fleet.
Edge Computing Requirements
This guide discusses the edge computing requirements for hardware, networking, availability, security, and visibility to ensure a successful deployment.
IT Infrastructure Management Best Practices
This guide discusses IT infrastructure management best practices for creating and maintaining more resilient enterprise networks.
Legrand Acquires ZPE Systems, Inc.
ZPE Systems is now a brand of Legrand! Read the full press release for details about the acquisition.
Collaboration in DevOps: Strategies and Best Practices
This guide to collaboration in DevOps provides tips and best practices to bring Dev and Ops together while minimizing friction for maximum operational efficiency.
Terminal Servers: Uses, Benefits, and Examples
This guide answers all your questions about terminal servers, discussing their uses and benefits before describing what to look for in the best terminal server solution.