ZPE Cloud centralizes management of data center, branch, and remote edge network infrastructure under a single cloud interface.
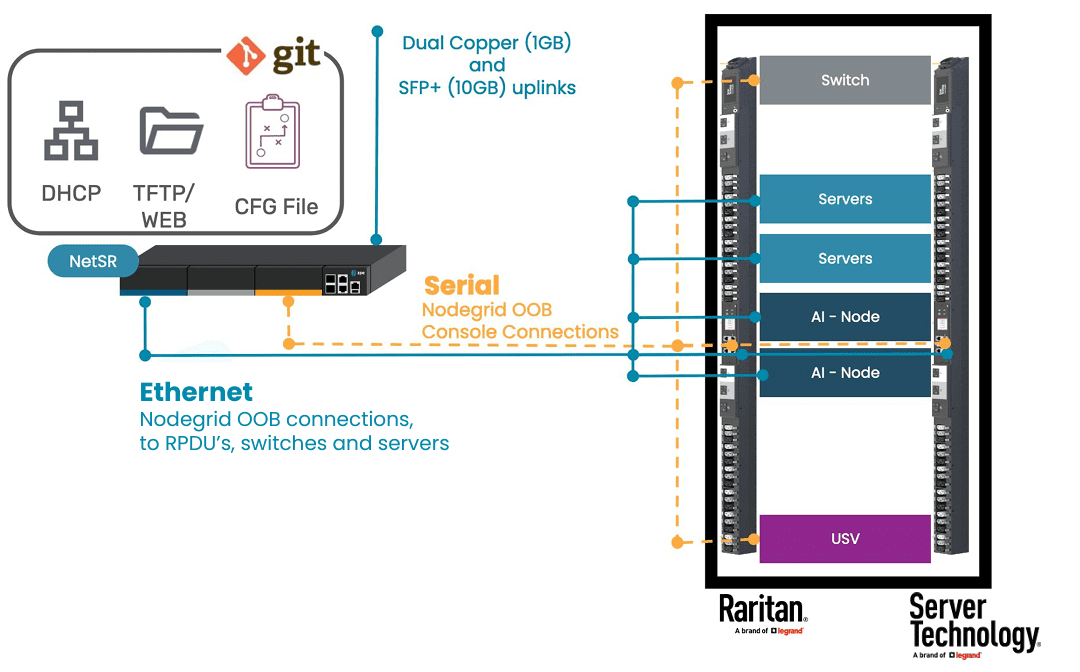

ZPE Cloud centralizes management of data center, branch, and remote edge network infrastructure under a single cloud interface.
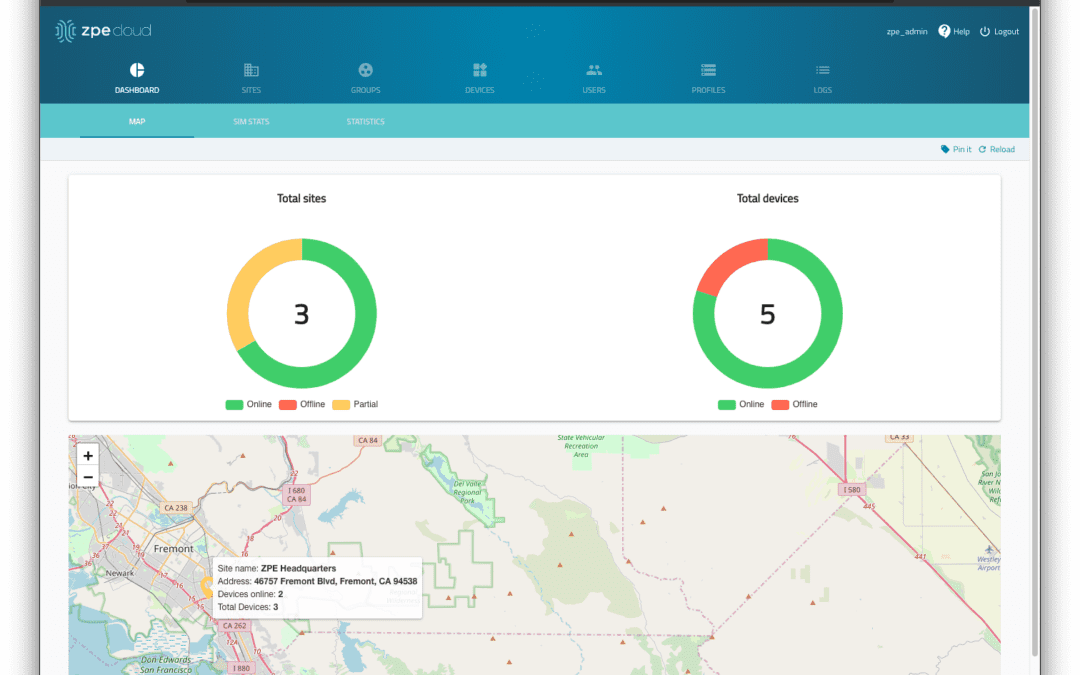
ZPE Cloud centralizes management of data center, branch, and remote edge network infrastructure under a single cloud interface.

Download this guide to see how ZPE Systems provides comprehensive hardware and software security to protect against supply chain vulnerabilities.
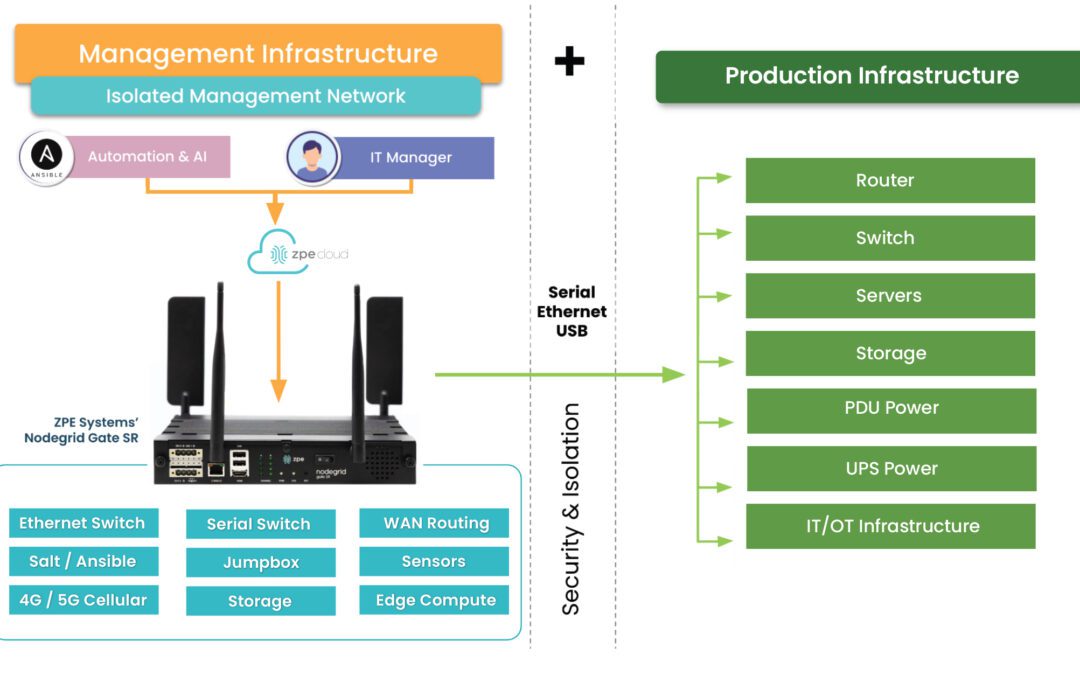
Isolated Management Infrastructure is the key to modern network resilience. Read about the gaps of existing approaches and why Big Tech trusts IMI.
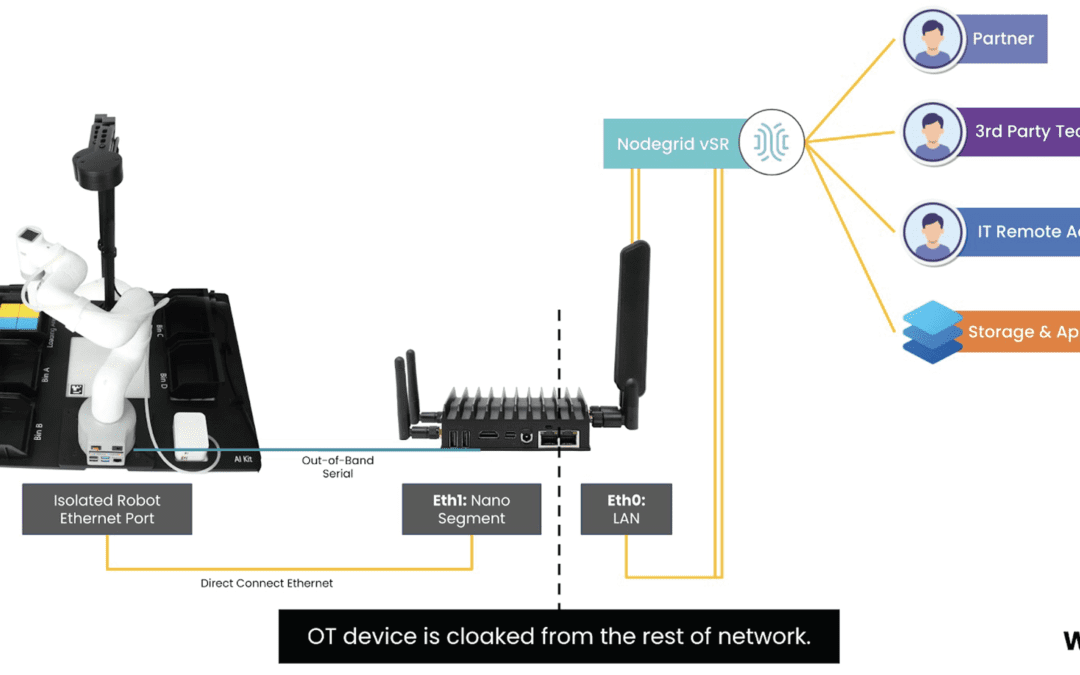
Summary With IoT and OT (operationalized technology) sprawling across the globe, organizations are able to provide more value to their customers. But for IT security teams, this presents a growing attack surface that’s easy for malicious actors to exploit. Weak...

Summary Enterprise IT teams struggle to secure their environments. One proven approach is for teams to attack their own network, a process called security penetration testing, which is executed externally or internally of the network and extends to all areas of...

Summary Cloudflare One provides Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA). This industry-leading solution is trusted worldwide to provide enterprises with secure connectivity for their distributed workforces. The challenge is that many...
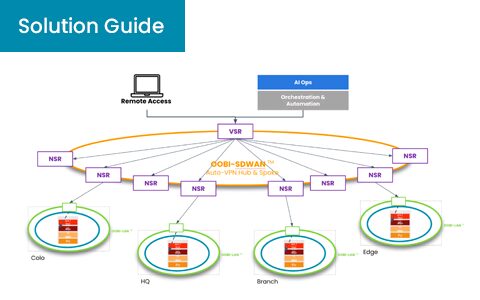
Summary Most enterprises operate a hybrid- or multi-cloud environment, which adds significant overhead, complexity, and architectural challenges. This turns networking and security into an operational battleground, where teams are ill-equipped to win against...
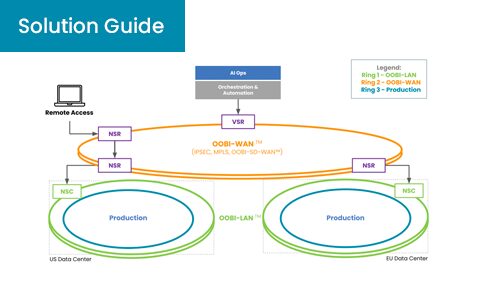
Summary Ransomware attacks continue to be successful because organizations often leave infrastructure unpatched. IT teams sit on the latest patches and updates from their solution vendors, which exposes infrastructure for the taking and leaves it vulnerable to...
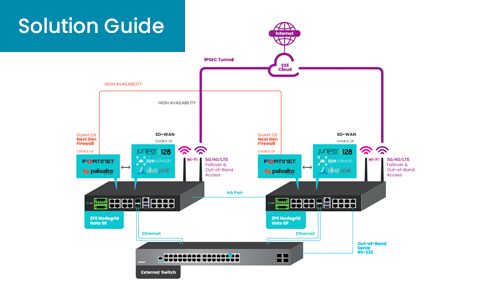
Summary Organizations struggle to manage the hundreds of products involved in enterprise security. Most NGFWs, SD-WAN, pen testers, and on-prem & cloud solutions require hardware platforms to be deployed with the rest of enterprise IT, which creates infrastructure...