This blog discusses the five biggest benefits of edge computing, providing examples and additional resources for companies beginning their edge journey.


This blog discusses the five biggest benefits of edge computing, providing examples and additional resources for companies beginning their edge journey.
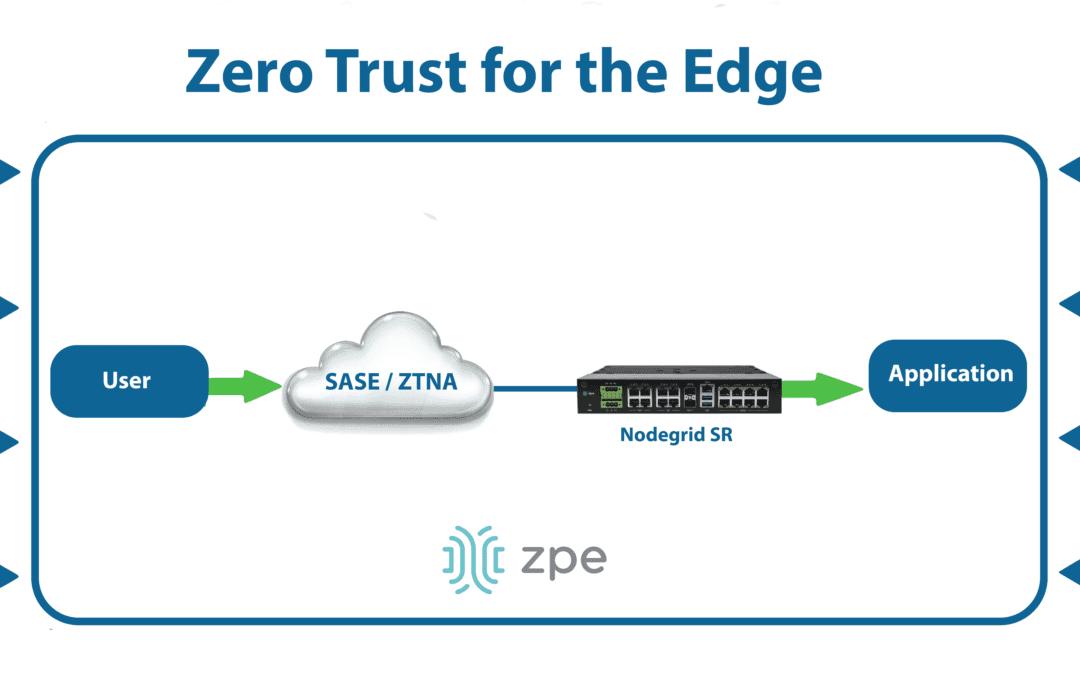
This blog provides advice for improving your zero trust security posture with a multi-layered strategy that mitigates weaknesses for complete coverage.

This guide compares the most popular edge security solutions and offers recommendations for choosing the right vendor for your use case.
This blog highlights 7 edge computing examples from across many different industries and provides tips and best practices for each use case.

This guide compares edge computing vs cloud computing to help organizations choose the right deployment model for their use case.
This edge computing architecture guide provides information and resources needed to ensure a streamlined, resilient, and cost-effective deployment.

This guide discusses the edge computing requirements for hardware, networking, availability, security, and visibility to ensure a successful deployment.

This guide discusses IT infrastructure management best practices for creating and maintaining more resilient enterprise networks.

This guide answers all your questions about terminal servers, discussing their uses and benefits before describing what to look for in the best terminal server solution.

This blog defines a hyperscale data center deployment before discussing the unique challenges involved in managing and supporting such an architecture.

A guide to resilient healthcare network design using technologies like automation, edge computing, and isolated recovery environments (IREs).

This post summarizes Gartner’s advice for building an edge computing strategy and discusses how an edge management and orchestration solution like Nodegrid can help.

This post provides an introduction to radio access networks (RAN) before discussing 5G RAN challenges, solutions, and use cases.

This guide defines OT, explains how to overcome some of the biggest operational technology security challenges, and discusses the importance of recovery in building resilience in OT.
Discussing the factors that make medical devices a cybersecurity risk before providing mitigation strategies to help healthcare organizations.

This post defines a zero trust security architecture, discusses some of the gaps typically left in such an architecture, and provides tips for avoiding these pitfalls.

Gartner’s SSE Magic Quadrant for 2023 identifies 10 key vendors currently providing secure service edge capabilities for the enterprise market. In this guide, we’ll summarize the common factors shared among leading SSE vendors, discuss what separates them from niche...

The most successful ransomware attack ever is happening right now. See why isolated management infrastructure is the only way to save your organization.

Defining Security as a Service, discussing the pros and cons, and describing an alternative solution for streamlined and scalable cybersecurity management.

This post provides a “cheat sheet” of solutions to the most common zero touch deployment challenges to help organizations streamline their automatic device provisioning.
An IoT device management system is meant to simplify and streamline the management of remote, hard-to-reach, and complex IoT devices and infrastructure.

The best cloud edge gateway solution is vendor-neutral, uses cellular for failover and OOB management, follows Zero Trust best practices, and supports major automation tools and scripting languages.

As part of a resilient network automation framework, the most important automation infrastructure components include OOBM, SD-WAN, monitoring, IaC, and immutable infrastructure.

An IT/OT convergence strategy brings information technology and operational technology together under one management umbrella to create a unified, efficient, and resilient network infrastructure.

Edge computing for machine learning places ML applications closer to remote sources of data, such as IoT devices, “smart” industrial systems, and remote healthcare systems.

Cellular failover routers, bridges, and gateways offer similar capabilities, so here’s what you need to know about all three to find the best option for your business continuity.

Vendor-agnostic platforms, SD-WAN, and automation are key tools that help organizations more effectively utilize the hybrid cloud in their digital transformation journey.

Here we dig into the causes and effects of data center outages according to the Uptime Institute report and discuss how OOB data center connectivity can help

A renewed enthusiasm for uCPE has been led by a greater interest in software-based networking and a need for hardware capable of running that software.

Software-defined wide area networking, or SD-WAN, has made it possible to efficiently control highly distributed WAN architectures using software abstraction and automation. SD-WAN adoption is increasing, partially due to the rise in remote work during the pandemic,...

How to keep colocation data center pricing in check through consolidated devices, DCIM power management, SDN, and out-of-band management.

There are challenges with managing a complex cybersecurity environment. Here is how Cybersecurity-as-a-Platform (CaaP) can help.

SASE technology connects network edge resources directly to cloud services, reducing the load on the main firewall without sacrificing security.

ZTNA is the superior choice for branch and edge networking because of its security, speed, and scalability.

Protecting modern distributed edge networks have its challenges. Discover how the Noregrid SD-WAN solution can help you.

Cybersecurity has been a hot topic for years. With many high-profile breaches, malware attacks, and pricey payouts, it’s no wonder why companies continue to add more and more protection for their IT systems. Despite this, hackers continue to succeed at exploiting...

Security Service Edge (SSE) is an emerging network security model that rolls up technologies like zero trust network access (ZTNA), cloud access security broker (CASB), secure web gateway (SWG), and next-generation firewalls/firewall as a service (FWaaS) into a...

Security service edge (SSE) is an emerging network security model, first announced by Gartner in their 2021 Hype Cycle, that stems from the need to retool the industry’s thinking about SASE (secure access service edge). SSE protects your network edge by combining...

Modern network management involves a wide variety of distributed technologies. Because of this, enterprises have progressively moved towards the Security Access Service Edge (SASE) model to provide remote users with secure cloud-based services. Even though these...