Vishal Gupta discusses traditional out-of-band management solutions and shows how ZPE Systems’ Nodegrid combines OOB infrastructure into one device.


Vishal Gupta discusses traditional out-of-band management solutions and shows how ZPE Systems’ Nodegrid combines OOB infrastructure into one device.

Ahmed Algam discusses three real-world incidents and gives practical advice to avoid outages.

Mike Sale explains how ransomware makes traditional access useless, and how Gen 3 out-of-band management cuts the killchain.

ZPE’s IT and Systems Administrator Ahmed Algam shows how out-of-band management helps you recover when your rollback fails.

Mike Sale discusses why Gen 3 out-of-band management is a strategic weapon that helps you get better ROI on your IT investments.

ZPE’s Network and Systems Administrator Ahmed Algam discusses outage recovery and how out-of-band management helped quickly restore services.
Compare out-of-band vs Isolated Management Infrastructure (IMI) to learn about the important distinction regarding operational resilience.

AI system reliability is about ensuring AI is available even when things go wrong. Here’s why secure remote network management is key.
Discover the best practices to make PDU management simple and scalable without the need for on-site visits. Download the guide here.

Organizations are rethinking their cloud strategy. Our article covers why a hybrid cloud approach can maximize efficiency and control.

Organizations: “How do we get the most out of our AI infrastructure investment?” Get the answer & AI best practices in our article.
This guide breaks down the differences and best use cases for KVM switches and serial consoles, with advice on how to choose the right option.

Out-of-band monitoring improves network resilience. Read this post to see how it brings a proactive approach to management.

Read why we need data centers to be built cheaper and faster, and why lights-out operations are key to bringing this vision to life.

Out-of-band management makes AI infrastructure resilient and efficient. Read our post and download our whitepaper to see how it works.

This post explains FIPS 140-3 security certification, and why it matters to organizations and their customers.

This post covers the 7 security benefits of implementing FIPS 140-3 for out-of-band management networks.

The American Water cyberattack shows why resilience is key to critical services. Here’s how the attack unfolded and how to stop it.

Don’t make these five common data center mistakes. This article walks you through the pitfalls and how to avoid them along the way.

Perle console server replacement options from Nodegrid are vendor-neutral to provide a fully integrated infrastructure orchestration experience.
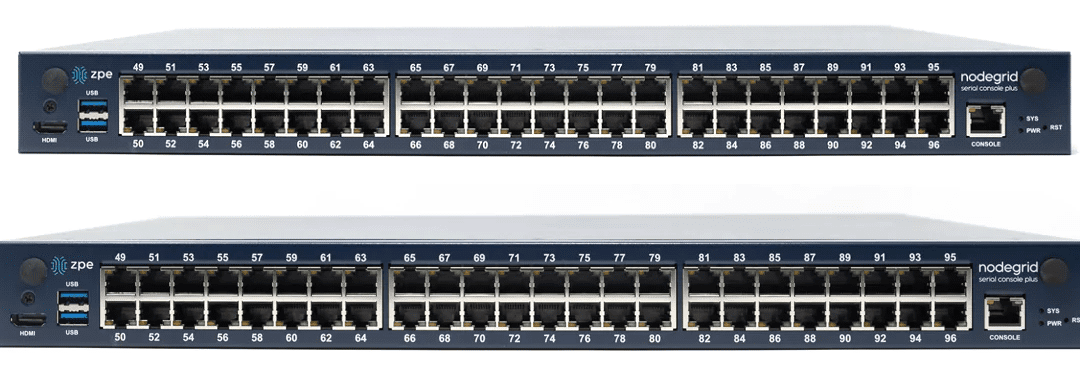
Console server hardware can vary significantly across different vendors and use cases. Learn how to find the right solution for your deployment.

This blog describes various methods for achieving data center scalability before providing tips and best practices to make scalability easier and more cost-effective to implement.

This blog defines serial console interfaces and describes their technological evolution before discussing the benefits of using a modern serial console solution.
This blog describes four edge computing use cases in banking before describing the benefits and best practices for the financial services industry.

This post describes the key components of AI data center infrastructure before providing advice for overcoming common pitfalls to improve the efficiency of AI deployments.
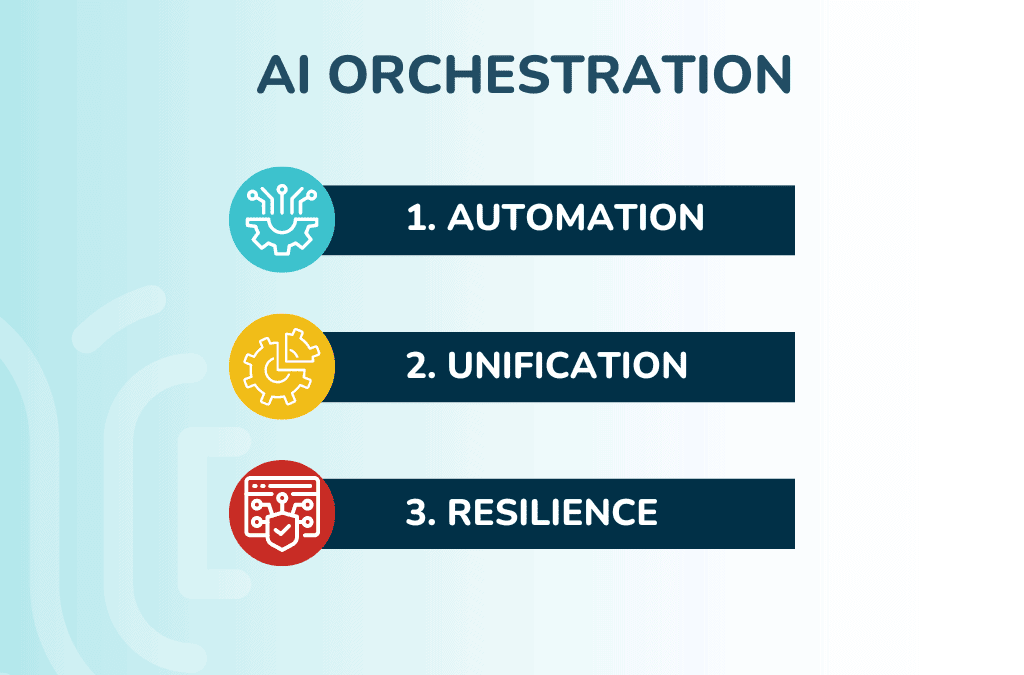
This post describes the ideal AI orchestration solution and the technologies that make it work, helping companies use artificial intelligence more efficiently.

This blog describes five potential edge computing use cases in retail and provides more information about the benefits of edge computing for the retail industry.

This blog describes five potential edge computing use cases in retail and provides more information about the benefits of edge computing for the retail industry.

Rene Neumann, Director of Solution Engineering, discusses why it’s crucial to replace end-of-life console servers to protect IT.

This blog describes six potential edge computing use cases in healthcare that take advantage of the speed and security of an edge computing architecture.

The CrowdStrike outage on July 19, 2024 affected millions of critical organizations. Here’s how to recover fast and avoid the next outage.

This blog discusses the five biggest benefits of edge computing, providing examples and additional resources for companies beginning their edge journey.
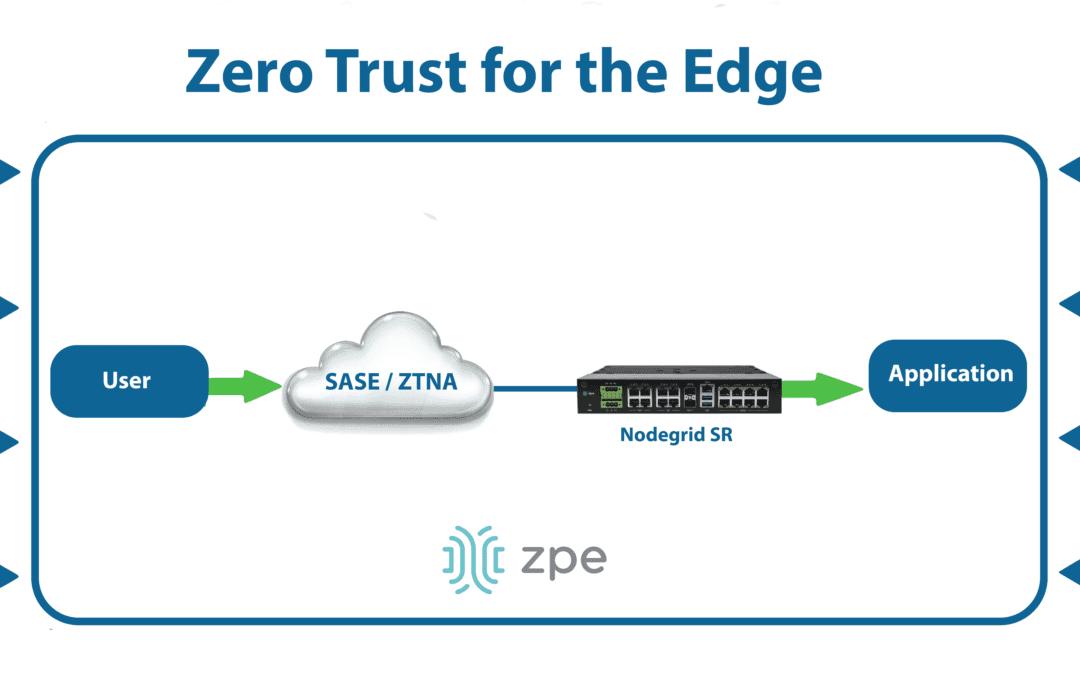
This blog provides advice for improving your zero trust security posture with a multi-layered strategy that mitigates weaknesses for complete coverage.

This guide compares edge computing vs cloud computing to help organizations choose the right deployment model for their use case.
This edge computing architecture guide provides information and resources needed to ensure a streamlined, resilient, and cost-effective deployment.

With limited time to demonstrate compliance with the Critical Entities Resilience Directive, organizations should begin preparing now.

This guide summarizes all twelve PCI DSS 4.0 requirements across six categories and describes the best practices for maintaining compliance.
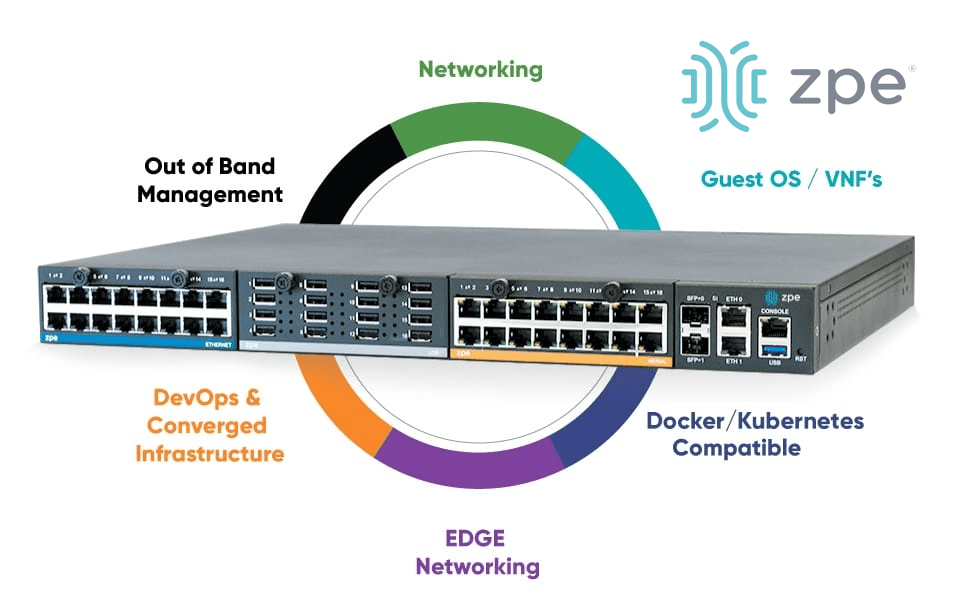
This guide compares Cisco ISR 4431 EOL replacement options and discusses the advanced features and capabilities offered by Cisco alternatives.

This guide compares Cisco 4351 EOL replacement options and discusses the innovative features and capabilities offered by Gen 3 branch networking solutions.

Discussing the future of edge computing as described by leading analysts at Gartner, which relies on comprehensive strategies and centralized, vendor-neutral edge management and orchestration.

The Digital Operational Resilience Act (DORA Act) outlines significant resilience changes for the financial sector. See how to comply here.

Cybersecurity expert James Cabe discusses what to do if you’re on the receiving end of a ransomware attack, including isolating systems.

Discussing how zero trust security benefits organizations by increasing visibility, reducing the attack radius, and providing precise security coverage.

This guide to network resilience defines resilience systems, discusses use cases and related technologies, and describes the key components required to build them.

Network resilience requirements have changed. James Cabe discusses why the new standard is Isolated Management Infrastructure.

This guide discusses IT infrastructure management best practices for creating and maintaining more resilient enterprise networks.
This guide to collaboration in DevOps provides tips and best practices to bring Dev and Ops together while minimizing friction for maximum operational efficiency.

This guide answers all your questions about terminal servers, discussing their uses and benefits before describing what to look for in the best terminal server solution.

Many organizations suffered Ragnar Locker cyberattacks in 2023. 30-year cybersecurity expert James Cabe discusses the problem and solution.

Casino giants in the US were hit by ransomware in September 2023. Cyber expert James Cabe breaks down the attack & how to recover.

This post describes some of the most common Intel NUC use cases, explains the security and management issues that caused its discontinuation, and provides superior replacement options.

What is zero trust security? This post defines the term and discusses its history before providing a guide to implementing zero trust in your organization.

This guide defines OT, explains how to overcome some of the biggest operational technology security challenges, and discusses the importance of recovery in building resilience in OT.
Discussing the factors that make medical devices a cybersecurity risk before providing mitigation strategies to help healthcare organizations.

This post defines a zero trust security architecture, discusses some of the gaps typically left in such an architecture, and provides tips for avoiding these pitfalls.

Gartner’s SSE Magic Quadrant for 2023 identifies 10 key vendors currently providing secure service edge capabilities for the enterprise market. In this guide, we’ll summarize the common factors shared among leading SSE vendors, discuss what separates them from niche...

The most successful ransomware attack ever is happening right now. See why isolated management infrastructure is the only way to save your organization.

Zero trust for OT uses network segmentation, strong security policies, and advanced security technologies to protect operational technology from attack.

This post discusses how to take advantage of IoT in the finance industry by overcoming security challenges with automation, secure platforms, and vendor-neutral orchestration.

In this guest post, Atsign CTO & Co-Founder Colin Constable discusses how their IoT security solutions just work with ZPE Systems.
Discussing the challenges and security risks associated with Intel NUC jump boxes before providing enterprise-grade Intel NUC alternatives that solve these problems.
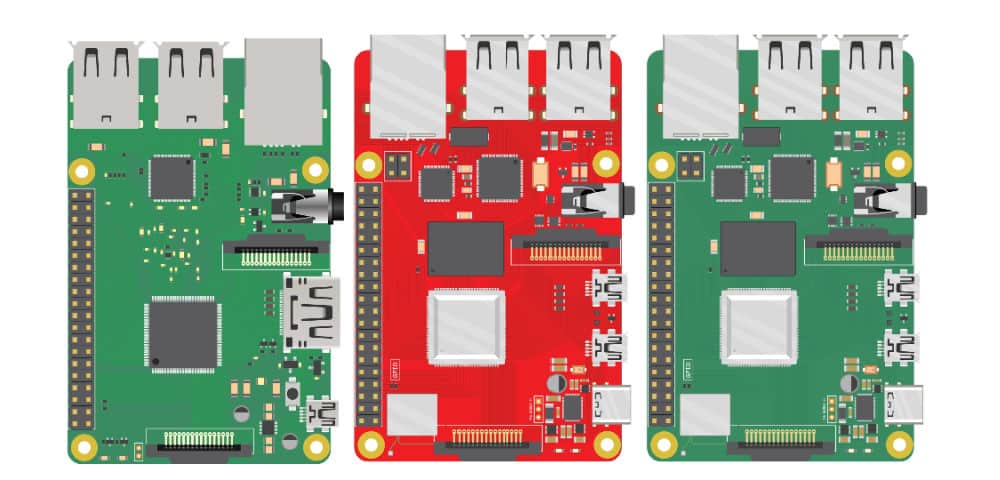
The Nodegrid line of Raspberry Pi alternatives from ZPE Systems can help your organization prevent Shadow IT to reduce your attack surface and improve your security posture without increasing costs.

Defining Security as a Service, discussing the pros and cons, and describing an alternative solution for streamlined and scalable cybersecurity management.
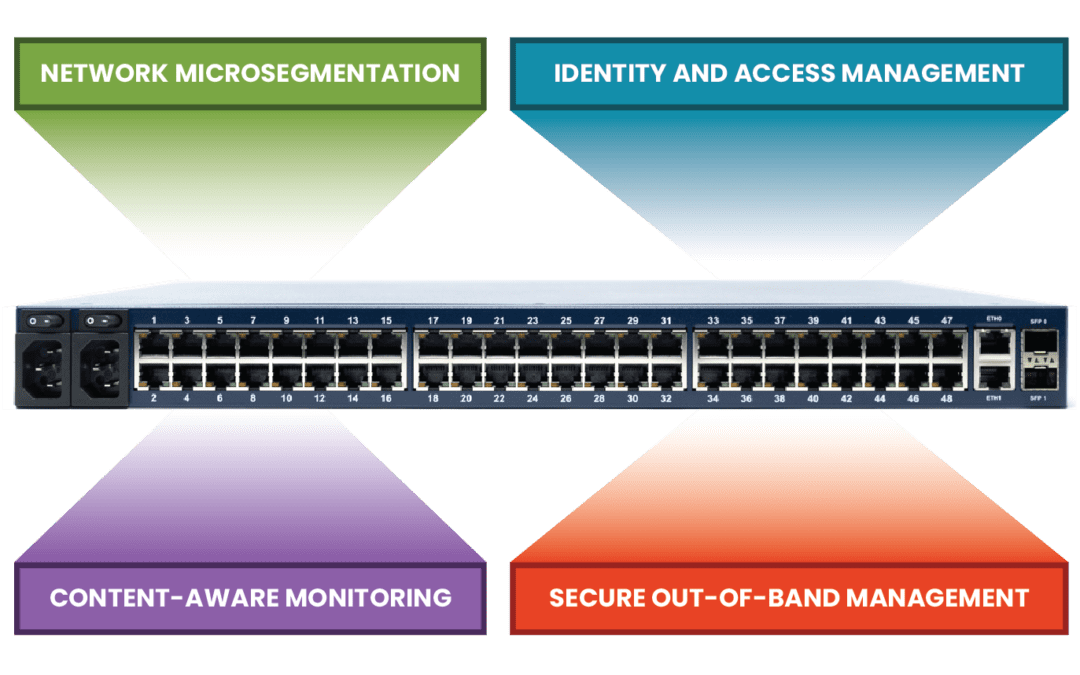
This post discusses the technologies that make up a zero trust gateway and explains how they work together to defend enterprise networks.
Today’s IT teams must maintain a growing infrastructure of on-prem and cloud solutions. These range from physical routers, out-of-band devices, and firewalls, to Zero Trust Security solutions, micro-segmentation tools, and network automation integrations. Despite an...

Network engineers need to make the most of their tools during a slow economy. Read on for five must-have tools for keeping services online.

Software-defined wide area networking, or SD-WAN, has made it possible to efficiently control highly distributed WAN architectures using software abstraction and automation. SD-WAN adoption is increasing, partially due to the rise in remote work during the pandemic,...

IT teams will face three big gaps this winter. Read on to see what they are & how to close them for good with a proven network blueprint.

There are challenges with managing a complex cybersecurity environment. Here is how Cybersecurity-as-a-Platform (CaaP) can help.

ZTNA is the superior choice for branch and edge networking because of its security, speed, and scalability.

CIOs: How will you make it through the winter recession? Read on for three key questions to answer & discover the blueprint for a proven resilience strategy.

Protecting modern distributed edge networks have its challenges. Discover how the Noregrid SD-WAN solution can help you.

Cybersecurity has been a hot topic for years. With many high-profile breaches, malware attacks, and pricey payouts, it’s no wonder why companies continue to add more and more protection for their IT systems. Despite this, hackers continue to succeed at exploiting...
A supply chain attack is when cybercriminals breach your network by compromising an outside vendor or partner. Often, these attacks exploit a weak link in your trusted ecosystem of third-party software, hardware, and integrations. A hacker will, for example, use a...

How to implement zero trust security is a growing focus of organizations across the globe. With cyber attacks frequently hitting some of the largest companies and threatening entire economies, it’s no wonder why comprehensive network security is a top priority among...

Zero trust security is not a new concept, but it has gained popularity in recent years. As companies become increasingly distributed, they must offer flexible network access without putting sensitive data at risk. That’s where zero trust security comes in. What is...

How do secure access service edge (SASE) and zero trust work together to improve network security? Simply put, SASE works by deploying security via the cloud, and zero trust deploys security in the least privileged access method. Networking trends have heavily shifted...

As workloads, applications, and data move to the cloud and business operations expand to include branch offices, remote data centers, and work-from-home staff, how do you define your network security perimeter? With zero trust networks, you don’t have to. Zero trust...

Perimeter-based security is no longer sufficient for today’s enterprise network. You may even struggle to define your network perimeter anymore, mainly if you use cloud infrastructure, have remote data centers and branch offices, or rely on “Internet of Things” (IoT)...

Large enterprises may be hesitant to adopt zero trust security because it may seem too disruptive to their business. However, cyberattacks on businesses continue to increase, costing affected enterprises an average of $3.92 million per breach, so it’s clear that...

The internet of things (IoT) is driving companies to rethink how they secure their networks. When you introduce unmanaged, internet-connected smart devices to your network, you’re also introducing many new potential access points for malicious actors to breach your...
Without a zero trust architecture in place, your business might suffer a setback of $4 million or more due to cybercrime. That’s how much the Colonial Pipeline recently paid out after hackers shut down their oil delivery infrastructure and held its restoration for...
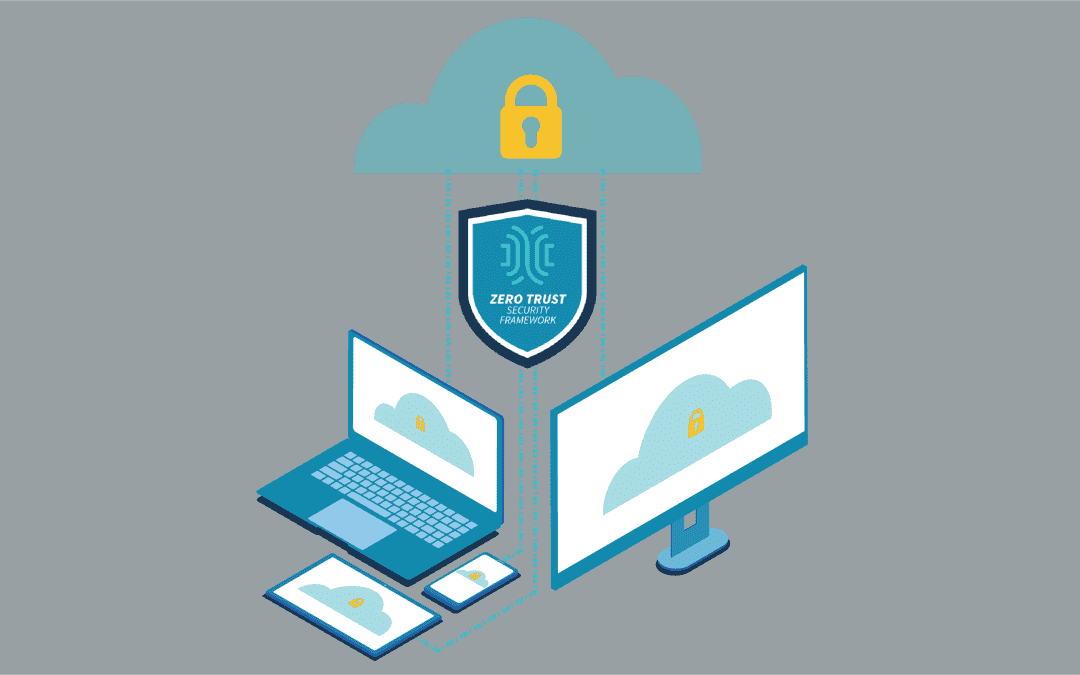
Zero Trust Security protects your enterprise inside and out. By safeguarding connections with approaches like traffic segmentation and multi-factor authentication, you can ensure total network security. But implementing and maintaining a zero trust posture poses...

Intel® CPUs power many of the computers we use today. These include everything from personal desktops and laptops, to high performance computing clusters that aggregate power to solve major global issues. So when choosing a suitable processor to build into our...

Zero trust security is not a new concept, however it has gained popularity in recent years. As companies become increasingly distributed, they must offer network access that’s flexible, without putting sensitive data at risk. This is where zero trust security comes...