Vishal Gupta discusses traditional out-of-band management solutions and shows how ZPE Systems’ Nodegrid combines OOB infrastructure into one device.


Vishal Gupta discusses traditional out-of-band management solutions and shows how ZPE Systems’ Nodegrid combines OOB infrastructure into one device.

Ahmed Algam discusses three real-world incidents and gives practical advice to avoid outages.

Mike Sale explains how ransomware makes traditional access useless, and how Gen 3 out-of-band management cuts the killchain.
This out-of-band management vendor comparison breaks down solutions from Opengear, Perle, Lantronix, and ZPE Systems.

ZPE’s IT and Systems Administrator Ahmed Algam shows how out-of-band management helps you recover when your rollback fails.

Mike Sale discusses why Gen 3 out-of-band management is a strategic weapon that helps you get better ROI on your IT investments.

ZPE’s Network and Systems Administrator Ahmed Algam discusses outage recovery and how out-of-band management helped quickly restore services.
Compare out-of-band vs Isolated Management Infrastructure (IMI) to learn about the important distinction regarding operational resilience.

AI system reliability is about ensuring AI is available even when things go wrong. Here’s why secure remote network management is key.
Discover the best practices to make PDU management simple and scalable without the need for on-site visits. Download the guide here.

Organizations are rethinking their cloud strategy. Our article covers why a hybrid cloud approach can maximize efficiency and control.

Organizations: “How do we get the most out of our AI infrastructure investment?” Get the answer & AI best practices in our article.
This guide breaks down the differences and best use cases for KVM switches and serial consoles, with advice on how to choose the right option.

Out-of-band monitoring improves network resilience. Read this post to see how it brings a proactive approach to management.

Read why we need data centers to be built cheaper and faster, and why lights-out operations are key to bringing this vision to life.

Out-of-band management makes AI infrastructure resilient and efficient. Read our post and download our whitepaper to see how it works.

Discussing where the G520 falls short, why it matters, and alternative options that deliver consolidated IIoT capabilities and network resilience.

This guide highlights four Nodegrid models that serve as direct replacements for – or alternatives to – Opengear Lighthouse appliances.

This post explains FIPS 140-3 security certification, and why it matters to organizations and their customers.

This post covers the 7 security benefits of implementing FIPS 140-3 for out-of-band management networks.

This guide compares five terminal server alternatives that give teams reliable remote management access without unnecessary complications.
Read our post for the latest insights about edge computing from Gartner. We cover edge computing platforms and how to address the challenges.

Zombie servers drain energy and cost billions of dollars per year. Here’s how to stop this nightmare from lurking in your data center.

The American Water cyberattack shows why resilience is key to critical services. Here’s how the attack unfolded and how to stop it.

Learn about different types of network virtualization platforms, the benefits of virtualization, and best practices for maximizing efficiency.

Perle console server replacement options from Nodegrid are vendor-neutral to provide a fully integrated infrastructure orchestration experience.

A lack of supply chain security introduces risks that affect network infrastructure. See how to shrink these risks with ZPE’s secure hardware and software.
This blog describes four edge computing use cases in banking before describing the benefits and best practices for the financial services industry.

This post describes the key components of AI data center infrastructure before providing advice for overcoming common pitfalls to improve the efficiency of AI deployments.
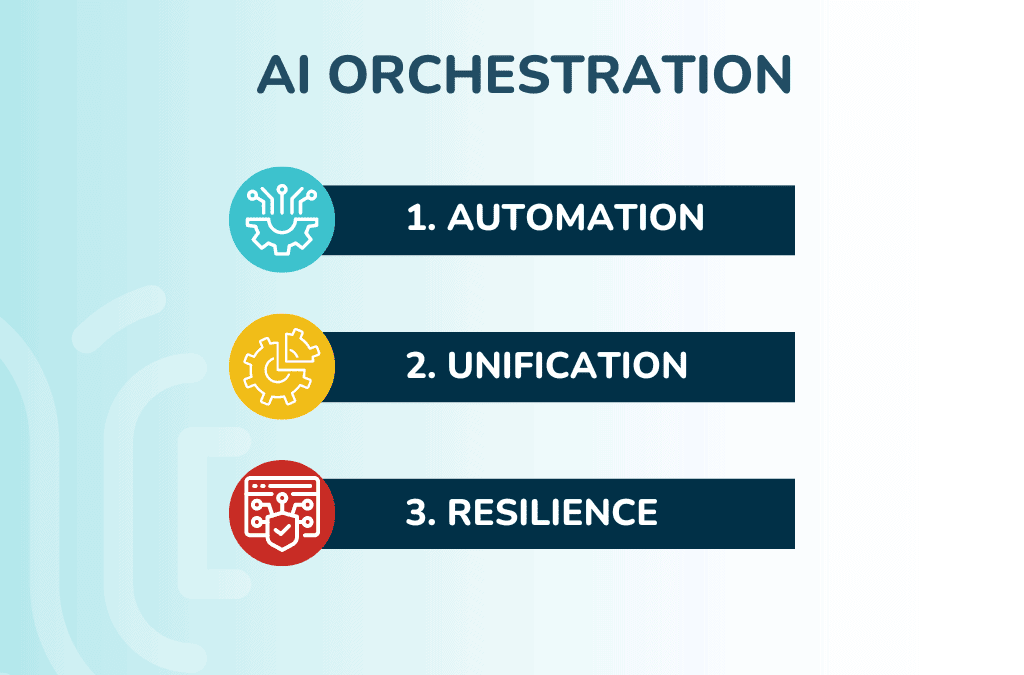
This post describes the ideal AI orchestration solution and the technologies that make it work, helping companies use artificial intelligence more efficiently.

This blog describes five potential edge computing use cases in retail and provides more information about the benefits of edge computing for the retail industry.

This blog describes five potential edge computing use cases in retail and provides more information about the benefits of edge computing for the retail industry.

Rene Neumann, Director of Solution Engineering, discusses why it’s crucial to replace end-of-life console servers to protect IT.

This blog describes six potential edge computing use cases in healthcare that take advantage of the speed and security of an edge computing architecture.

The CrowdStrike outage on July 19, 2024 affected millions of critical organizations. Here’s how to recover fast and avoid the next outage.

This blog discusses the five biggest benefits of edge computing, providing examples and additional resources for companies beginning their edge journey.
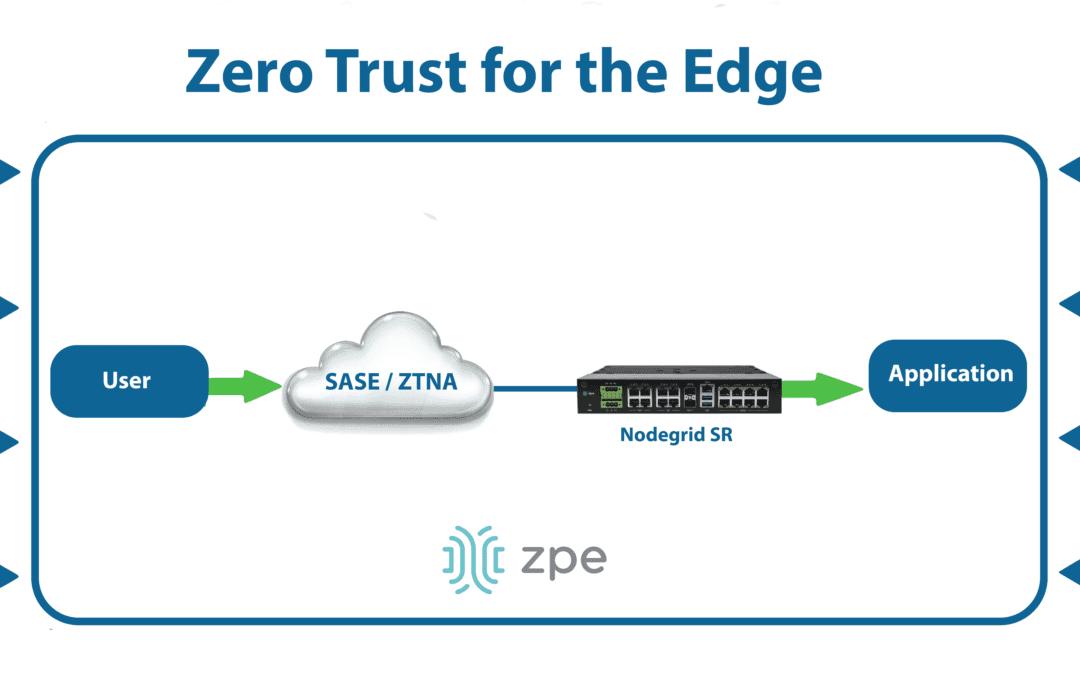
This blog provides advice for improving your zero trust security posture with a multi-layered strategy that mitigates weaknesses for complete coverage.

This guide compares the most popular edge security solutions and offers recommendations for choosing the right vendor for your use case.

This blog discusses some of the applications of edge computing for industries like finance, retail, and manufacturing and provides advice on how to get started.
This blog highlights 7 edge computing examples from across many different industries and provides tips and best practices for each use case.

This guide compares edge computing vs cloud computing to help organizations choose the right deployment model for their use case.
This edge computing architecture guide provides information and resources needed to ensure a streamlined, resilient, and cost-effective deployment.

With limited time to demonstrate compliance with the Critical Entities Resilience Directive, organizations should begin preparing now.

This guide describes the 10 minimum cybersecurity requirements mandated by NIS2 and provides tips to simplify NIS2 compliance.

Organizations can protect their IT and Nvidia AI investments using the Core Edition console server and dual-CPU Jetson module.

This guide outlines the technical requirements for DORA compliance and provides tips and best practices to streamline implementation.
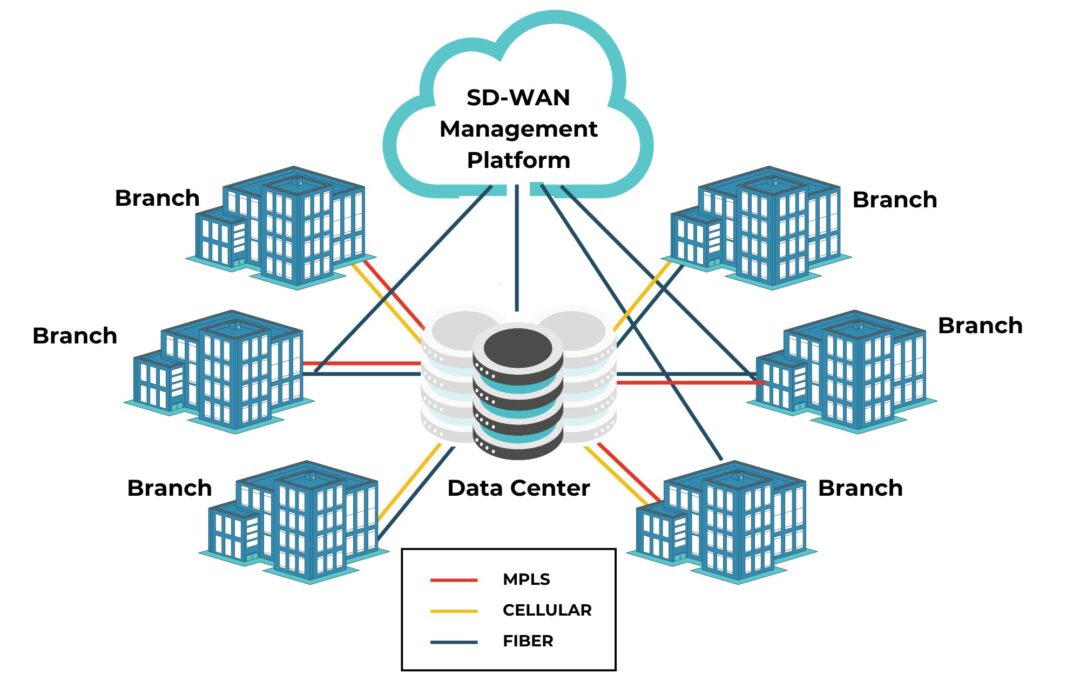
This SD-WAN management guide explains how this technology works, the potential benefits of using it, and the best practices to help you get the most out of your SD-WAN deployment.

This guide summarizes all twelve PCI DSS 4.0 requirements across six categories and describes the best practices for maintaining compliance.

Organizations using discontinued console servers can secure their infrastructure using ZPE’s new comprehensive solution. Get details here.

This guide compares Cisco 4351 EOL replacement options and discusses the innovative features and capabilities offered by Gen 3 branch networking solutions.

This blog reviews the Operations Manager platform before discussing Opengear alternatives that provide greater automation, security, and branch networking capabilities.

This report uses Gartner’s Magic Quadrant and independent analysis to compare the six SD-WAN leaders based on key factors like features and versatility.

The Digital Operational Resilience Act (DORA Act) outlines significant resilience changes for the financial sector. See how to comply here.

Cybersecurity expert James Cabe discusses what to do if you’re on the receiving end of a ransomware attack, including isolating systems.

Discussing how zero trust security benefits organizations by increasing visibility, reducing the attack radius, and providing precise security coverage.

This guide discusses the network management best practices for improving and supporting network resilience.

This guide to network resilience defines resilience systems, discusses use cases and related technologies, and describes the key components required to build them.

This guide to out-of-band management answers critical questions about what this technology is, why you need it, and how to choose the right solution.

Network resilience requirements have changed. James Cabe discusses why the new standard is Isolated Management Infrastructure.

This guide discusses the edge computing requirements for hardware, networking, availability, security, and visibility to ensure a successful deployment.

This guide discusses IT infrastructure management best practices for creating and maintaining more resilient enterprise networks.
This guide to collaboration in DevOps provides tips and best practices to bring Dev and Ops together while minimizing friction for maximum operational efficiency.

This guide answers all your questions about terminal servers, discussing their uses and benefits before describing what to look for in the best terminal server solution.

This blog defines a hyperscale data center deployment before discussing the unique challenges involved in managing and supporting such an architecture.

A guide to resilient healthcare network design using technologies like automation, edge computing, and isolated recovery environments (IREs).

This guide compares three of the best network performance monitoring tools by analyzing the most critical factors and discussing the pros and cons.

Many organizations suffered Ragnar Locker cyberattacks in 2023. 30-year cybersecurity expert James Cabe discusses the problem and solution.

ZPE Systems achieves the industry’s highest security level by incorporating Synopsys code-quality measures. Read the details here.

Comparing the four best OOB network management software tools and discussing the features, pros, and cons to help you make the best choice for your environment.

Download the case study to see how Living Spaces cut costs by $300,000 per year and scaled across the U.S. with only 3 network staff.

Explaining the challenges that make ISP network architectures less resilient and providing solutions for overcoming these hurdles.

This post summarizes Gartner’s advice for building an edge computing strategy and discusses how an edge management and orchestration solution like Nodegrid can help.

Casino giants in the US were hit by ransomware in September 2023. Cyber expert James Cabe breaks down the attack & how to recover.

This post describes some of the most common Intel NUC use cases, explains the security and management issues that caused its discontinuation, and provides superior replacement options.

What is zero trust security? This post defines the term and discusses its history before providing a guide to implementing zero trust in your organization.

This post analyzes the top 5 IT infrastructure management challenges while providing potential solutions and additional resources.

This post provides an introduction to radio access networks (RAN) before discussing 5G RAN challenges, solutions, and use cases.

This guide defines OT, explains how to overcome some of the biggest operational technology security challenges, and discusses the importance of recovery in building resilience in OT.
Discussing the factors that make medical devices a cybersecurity risk before providing mitigation strategies to help healthcare organizations.

This post defines a zero trust security architecture, discusses some of the gaps typically left in such an architecture, and provides tips for avoiding these pitfalls.

Gartner’s SSE Magic Quadrant for 2023 identifies 10 key vendors currently providing secure service edge capabilities for the enterprise market. In this guide, we’ll summarize the common factors shared among leading SSE vendors, discuss what separates them from niche...

This guide defines an application delivery platform, discusses the underlying technology, and highlights a leading platform engineering solution.

The most successful ransomware attack ever is happening right now. See why isolated management infrastructure is the only way to save your organization.

Zero trust for OT uses network segmentation, strong security policies, and advanced security technologies to protect operational technology from attack.

A discussion of how SD-WAN decreases branch networking costs, including an SD-WAN ROI calculator for a more personalized estimate of the potential savings.

This post discusses how to take advantage of IoT in the finance industry by overcoming security challenges with automation, secure platforms, and vendor-neutral orchestration.

In this guest post, Atsign CTO & Co-Founder Colin Constable discusses how their IoT security solutions just work with ZPE Systems.
Discussing the challenges and security risks associated with Intel NUC jump boxes before providing enterprise-grade Intel NUC alternatives that solve these problems.

In this guide, we’ll compare migration options for the Cisco ISR 2900 EOL models to help you select a solution that suits your business use case, deployment size, and future growth.
The Nodegrid line of Raspberry Pi alternatives from ZPE Systems can help your organization prevent Shadow IT to reduce your attack surface and improve your security posture without increasing costs.

Defining Security as a Service, discussing the pros and cons, and describing an alternative solution for streamlined and scalable cybersecurity management.
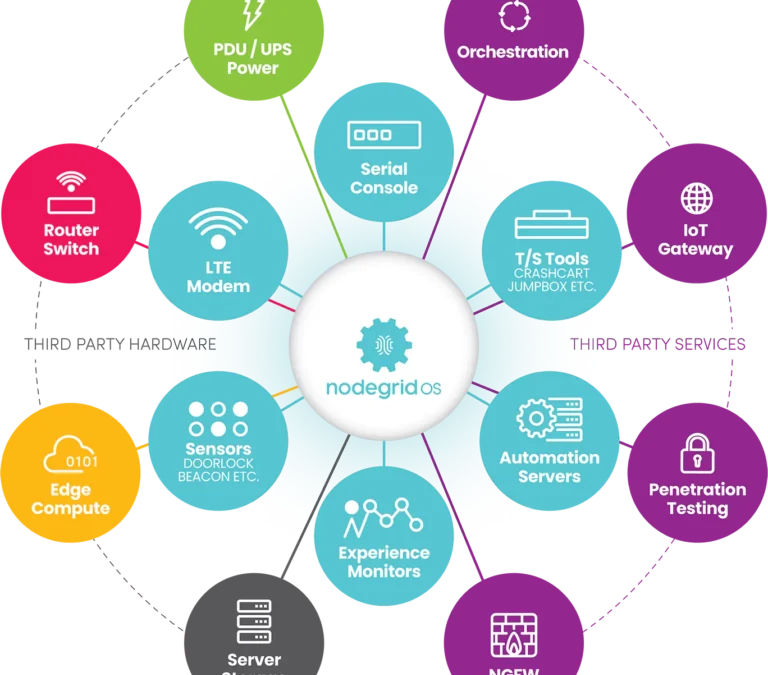
ZPE Systems’ Services Delivery Platform accelerates time-to-market with any app, anytime, anywhere IT teams can deliver instant business value with the on-demand services delivery architecture Fremont, CA, April 25, 2023 — ZPE Systems’ Services Delivery Platform is...

This post provides a “cheat sheet” of solutions to the most common zero touch deployment challenges to help organizations streamline their automatic device provisioning.
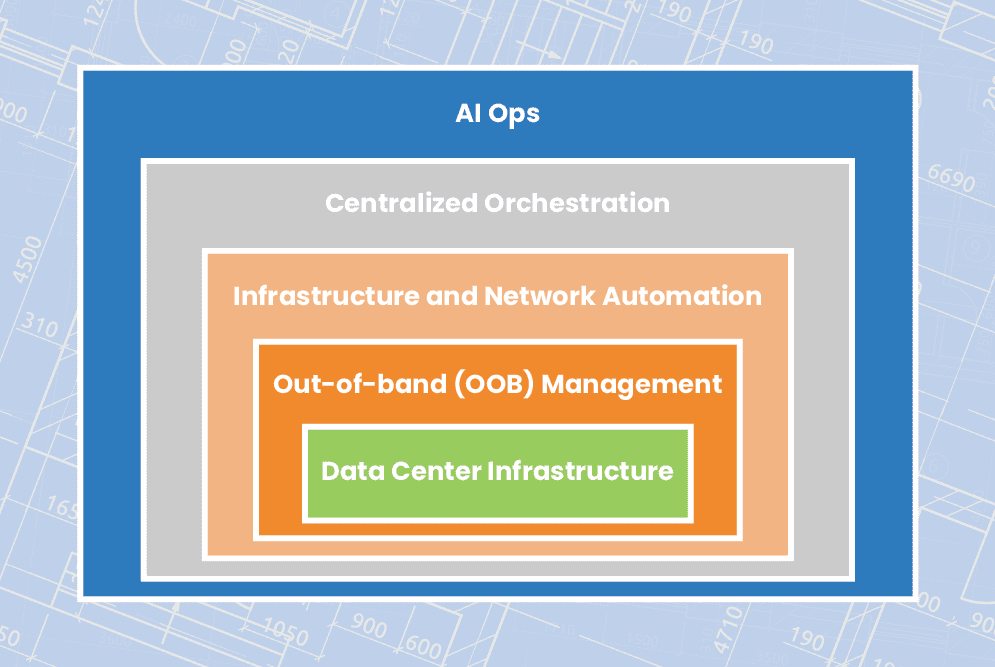
Learn how to streamline remote data center management using technologies like OOB management, automation, orchestration, and AIOps to ensure network resiliency.
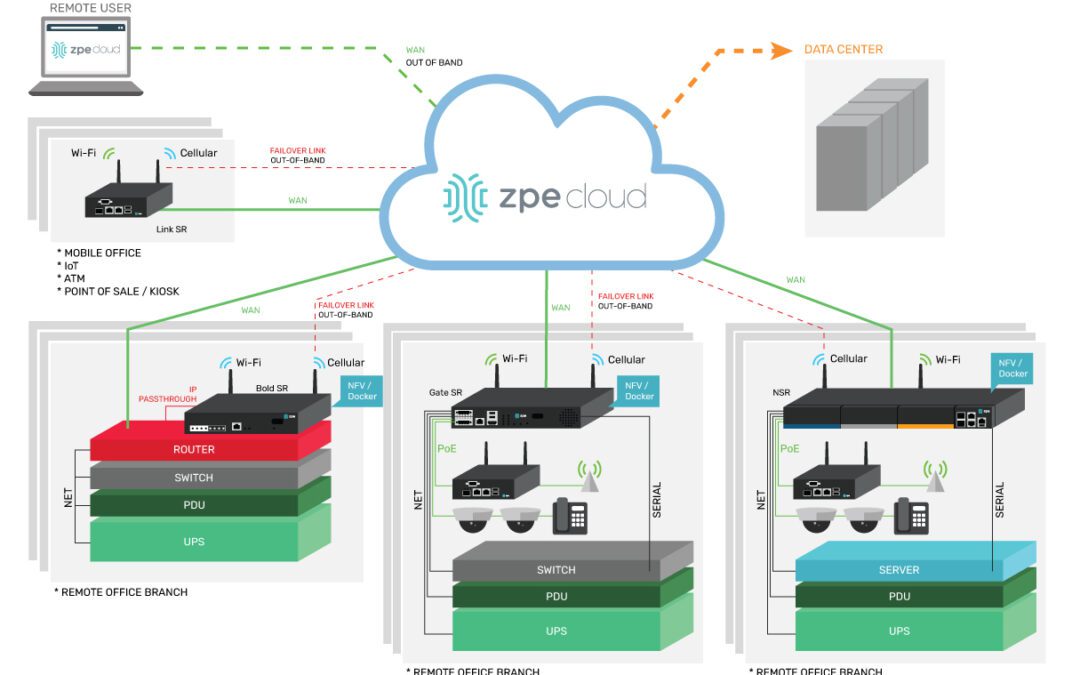
Describing the three cloud-based services involved in a cloud-delivered branch and illustrating how to implement a cloud-delivered branch with Nodegrid.
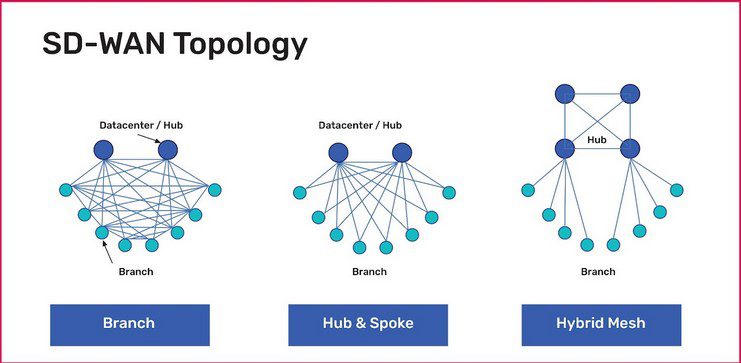
Learn about the most common SD-WAN deployment models with diagrams, pros and cons, and best practices to help organizations choose the right topology.

SD-WAN benefits organizations through MPLS cost reduction, improved WAN performance, greater automation & orchestration, and enhanced security capabilities.
Compact, all-in-one branch gateways use environmental monitoring, OOB management, and vendor-neutral platforms to simplify retail network management.

A centralized, automated OOB remote site monitoring solution helps to ensure network resilience even when recessions, pandemics, and other unforeseen events affect staffing on network teams.

Though white box networking has many advantages in theory, a lot of companies find it hard to achieve these benefits in practice. Here’s how to build a solution that avoids common pitfalls.

An out-of-band cybersecurity platform uses OOB infrastructure, vendor-neutral management software, and end-to-end automation to provide holistic network security.
An IoT device management system is meant to simplify and streamline the management of remote, hard-to-reach, and complex IoT devices and infrastructure.

The best cloud edge gateway solution is vendor-neutral, uses cellular for failover and OOB management, follows Zero Trust best practices, and supports major automation tools and scripting languages.

As part of a resilient network automation framework, the most important automation infrastructure components include OOBM, SD-WAN, monitoring, IaC, and immutable infrastructure.

An IT/OT convergence strategy brings information technology and operational technology together under one management umbrella to create a unified, efficient, and resilient network infrastructure.

Edge computing for machine learning places ML applications closer to remote sources of data, such as IoT devices, “smart” industrial systems, and remote healthcare systems.

Cellular failover routers, bridges, and gateways offer similar capabilities, so here’s what you need to know about all three to find the best option for your business continuity.

Vendor-agnostic platforms, SD-WAN, and automation are key tools that help organizations more effectively utilize the hybrid cloud in their digital transformation journey.

Here we dig into the causes and effects of data center outages according to the Uptime Institute report and discuss how OOB data center connectivity can help

A renewed enthusiasm for uCPE has been led by a greater interest in software-based networking and a need for hardware capable of running that software.

Vendor-neutral management devices, platforms, and ZTP allow you to upgrade network infrastructure with minimal business interruption.

Software-defined wide area networking, or SD-WAN, has made it possible to efficiently control highly distributed WAN architectures using software abstraction and automation. SD-WAN adoption is increasing, partially due to the rise in remote work during the pandemic,...

How to keep colocation data center pricing in check through consolidated devices, DCIM power management, SDN, and out-of-band management.

There are challenges with managing a complex cybersecurity environment. Here is how Cybersecurity-as-a-Platform (CaaP) can help.

SASE technology connects network edge resources directly to cloud services, reducing the load on the main firewall without sacrificing security.

ZTNA is the superior choice for branch and edge networking because of its security, speed, and scalability.

Here’s how to solve remote IT infrastructure management challenges using Gen 3 OOB for high-speed remote access, environmental monitoring, and orchestration.

ZPE Systems is featured in L’Informaticien Magazine. Read the translation here and check out the original source content.

Protecting modern distributed edge networks have its challenges. Discover how the Noregrid SD-WAN solution can help you.

There’s no doubt that edge computing comes with benefits and challenges. Find out how Nodegrid helps you actualize edge computing for your enterprise.

What is hybrid cloud infrastructure, and how is it achieved? Comparing the expectations vs. reality of hybrid cloud with solutions to common problems.

Immutable infrastructure involves servers, network appliances, and other devices which are never updated or changed. In part 1 of our blog series, we discussed the most inherent challenges with the immutable infrastructure paradigm. This post will cover immutable...

Immutable infrastructure refers to the critical network resources and systems that make up your infrastructure and that are never updated, changed, or fixed in any way—they stay exactly the same. If something needs to be modified, the entire system or device is...

Cybersecurity has been a hot topic for years. With many high-profile breaches, malware attacks, and pricey payouts, it’s no wonder why companies continue to add more and more protection for their IT systems. Despite this, hackers continue to succeed at exploiting...
A supply chain attack is when cybercriminals breach your network by compromising an outside vendor or partner. Often, these attacks exploit a weak link in your trusted ecosystem of third-party software, hardware, and integrations. A hacker will, for example, use a...

Your organization may feel secure now, but a disaster could occur at any moment. For example, the war in Ukraine took the world by surprise and left many organizations scrambling to protect and recover critical infrastructure, applications, and data from Ukrainian...
A branch network consists of many moving pieces that need to be remotely deployed, managed, and supported. That typically means separate devices for all the key functions like routing, switching, security, etc. However, as data and applications grow more...

Data center infrastructure management (DCIM) keeps evolving to address enterprises' changing goals, requirements, and concerns. We spoke with DCIM sales engineers to find out which pain points are on their customer’s minds, and which emerging technologies their...

The importance of network automation is clear—you can reduce human error, create more efficient workflows, and streamline operations. However, many enterprises delay their automation efforts because of how challenging the process can be. Fortunately, automating your...

How autonomous decommissioning via out-of-band has become essential to disaster recovery for edge deployments in uncertain geographies To say there’s instability in Eastern Europe would be a drastic understatement. Russia continues its attacks on many fronts in...
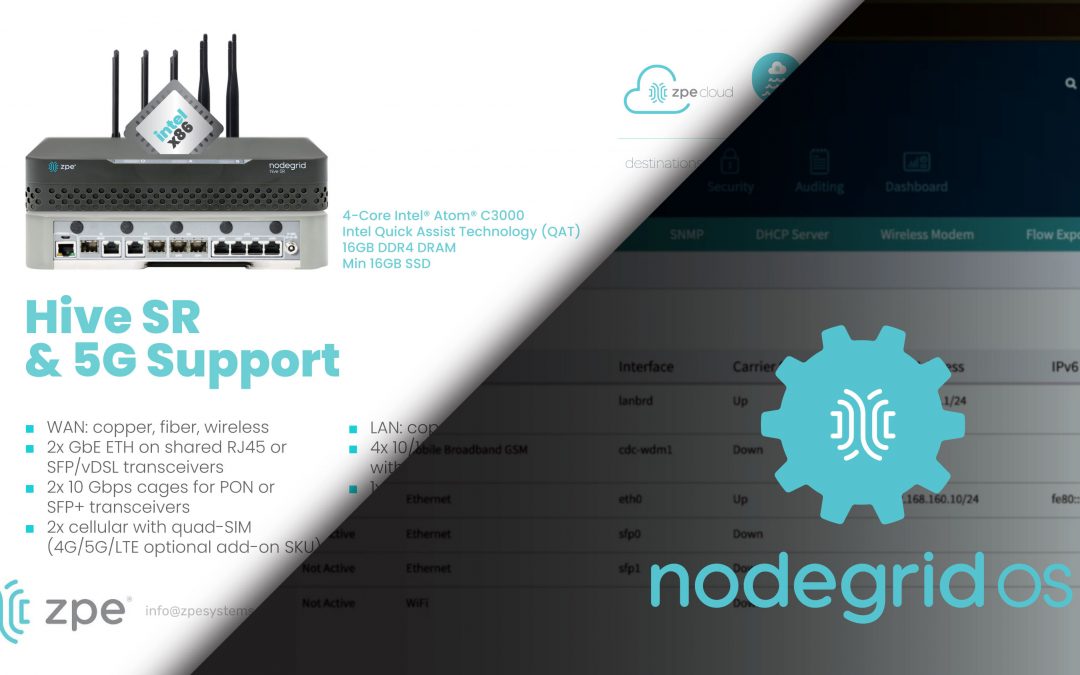
Sales Engineering Manager Rene Neumann walks you through the new features in Nodegrid OS v5.4. Don’t miss these out-of-band and security updates.
Hybrid cloud—using a combination of public and private clouds to host your data, applications, and services—is one of the most popular enterprise infrastructure models. According to Flexera’s 2021 State of the Cloud Report, 82% of enterprises have a hybrid cloud...

Security Service Edge (SSE) is an emerging network security model that rolls up technologies like zero trust network access (ZTNA), cloud access security broker (CASB), secure web gateway (SWG), and next-generation firewalls/firewall as a service (FWaaS) into a...

Security service edge (SSE) is an emerging network security model, first announced by Gartner in their 2021 Hype Cycle, that stems from the need to retool the industry’s thinking about SASE (secure access service edge). SSE protects your network edge by combining...

Modern network management involves a wide variety of distributed technologies. Because of this, enterprises have progressively moved towards the Security Access Service Edge (SASE) model to provide remote users with secure cloud-based services. Even though these...

How to implement zero trust security is a growing focus of organizations across the globe. With cyber attacks frequently hitting some of the largest companies and threatening entire economies, it’s no wonder why comprehensive network security is a top priority among...

How do secure access service edge (SASE) and zero trust work together to improve network security? Simply put, SASE works by deploying security via the cloud, and zero trust deploys security in the least privileged access method. Networking trends have heavily shifted...

Security Service Edge. Is it just another fancy networking term? After all, we’ve already got SASE (Secure Access Service Edge), so why throw another buzzword into the mix? The truth is, there’s a big difference between Security Service Edge (SSE) and SASE. SSE is a...

SASE—which stands for secure access service edge—is a relatively new framework that converges wide-area networking with security into one cloud-based service stack. SASE uses software-defined wide area network (SD-WAN) technology to directly connect branch offices and...

Ransomware is one of the biggest threats to enterprise network security. Recent findings show that 37% of organizations were affected by ransomware attacks in 2020 alone. These attacks can be financially devastating, costing companies an average of $1.85 million in...

SASE—secure access service edge—combines SD-WAN technology with network security functionality into a single cloud-native solution. SASE uses SD-WAN’s intelligent routing to connect remote and branch users directly to cloud services, improving network and application...

Fremont, CA, August 10, 2021 – ZPE Systems launches a new applications marketplace, along with a portfolio of USB-type environmental sensors, meant to help organizations leverage valuable data generated by their IT components. As networks and users become more...

Secure access service edge (SASE) is the recommended architecture for security and connectivity. SASE combines wide area network (WAN) technology for robust onramp to cloud and network security services into one cloud-delivered connectivity and security software...
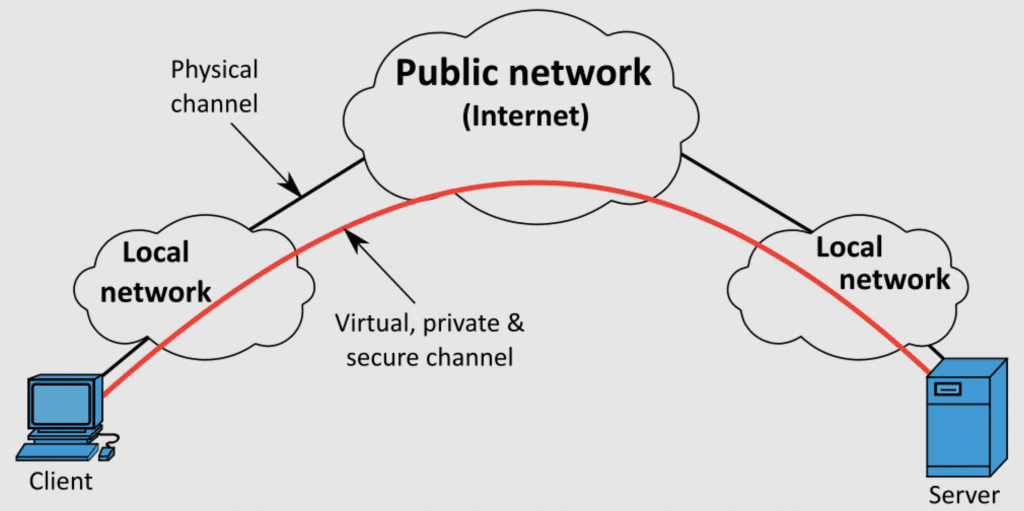
Do you know what to avoid when choosing a VPN? These virtual private networks are commonly promoted as the key to online privacy and security, as they employ dedicated point-to-point connections, tunneling protocols, and encryption. With the sharp increase in...
It’s easy to imagine all the ways that downtime can throw a wrench into your critical remote infrastructure operations. Things like scaling, service outages, and tedious management are just part of the job. No matter how much these stand in the way of business,...
Without a zero trust architecture in place, your business might suffer a setback of $4 million or more due to cybercrime. That’s how much the Colonial Pipeline recently paid out after hackers shut down their oil delivery infrastructure and held its restoration for...

What is the network edge? The network edge consists of systems that are not part of the data center. Think of a typical enterprise network: the data center is at the core, and then there are locations distributed across a market, area, or region, or even across the...
Zero Trust Security protects your enterprise inside and out. By safeguarding connections with approaches like traffic segmentation and multi-factor authentication, you can ensure total network security. But implementing and maintaining a zero trust posture poses...

Edge networking continues to grow as a vital component to business. With more people working remotely, whether from home, in the field, or on the road, it’s now critical to have a network that goes wherever your people go. And achieving that kind of connectivity is...

Intel® CPUs power many of the computers we use today. These include everything from personal desktops and laptops, to high performance computing clusters that aggregate power to solve major global issues. So when choosing a suitable processor to build into our...

Zero trust security is not a new concept, however it has gained popularity in recent years. As companies become increasingly distributed, they must offer network access that’s flexible, without putting sensitive data at risk. This is where zero trust security comes...

Many companies have found it difficult to adjust to remote work. In the face of drastic changes brought on by pandemics, natural disasters, and other challenges, untethering your workforce from the office can be a big ask. Your success relies on one crucial component:...
Secure Access Service Edge is a new concept that’s transforming the edge network. SASE delivers more flexible and secure network access, so your business can adapt to drastic changes and accommodate a distributed workforce. Want to see it in action? Here’s a 90-second...

Fremont, CA, September 17, 2020 – Today, ZPE Systems, Inc., a leading provider of network infrastructure management solutions, and 128 Technology, Inc. (128T), a leading provider of software-defined networking solutions, announced a strategic partnership to offer...

SD-Branch delivers some major advantages over traditional SD-WAN capabilities. Where typical software-defined approaches fall short at the branch level, SD-Branch picks up the slack to help you see and do much more. In case you need to catch up, here’s a 90-second...

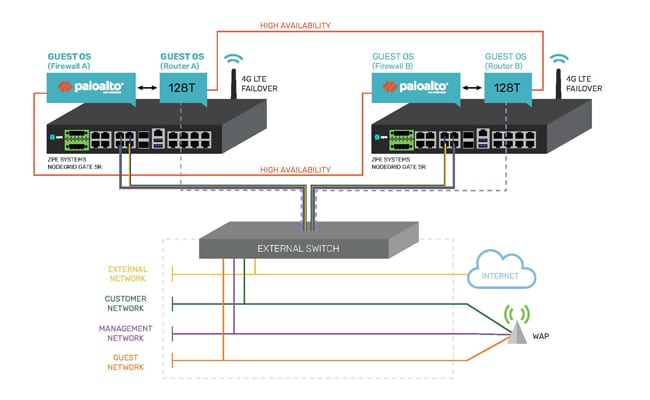
Fremont, CA, August 21, 2020 – Today, ZPE Systems, Inc., a leading solutions provider for network infrastructure management solutions, announced an integration with Palo Alto Networks to provide enhanced networking, out-of-band management and security capabilities to...

Secure Access Service Edge (SASE): It’s one of those new-ish IT acronyms that many folks have heard about, but far fewer have actually used or really even understand it. But if you have remote and branch office (ROBO) infrastructure as part of your operations, you...
Even if you’re familiar with these 10 things to consider when choosing a branch solution, you might not be sure about how to overcome the challenges of deploying branch networks. Here are some of those challenges. Deploying Your Branch Network is a Physical Ordeal...

Secure Access Service Edge transforms edge networking. See how ZPE Systems — a leading innovator in network infrastructure management — introduces even more capabilities to this cloud-based solution. What is Secure Access Service Edge? Secure Access Service...

It Happened Overnight. One day it was business as usual. The next, we were scrambling to set up our home offices. COVID-19 meant even the largest companies had to figure out remote work. And they had to adjust fast, not only to stay afloat and maintain business...

Secure Access Service Edge (SASE) is quickly evolving how enterprises offer secure connectivity. As the modern workforce becomes increasingly distributed, you need to accommodate more branch locations and remote workers. This is especially important given the global...

Managing many network devices and applications can be a chore, and a lot of this stems from having to manually authenticate with each. You typically need to keep a spreadsheet containing your different credentials (or run the risk associated with having one set of...
In recent years, SD-WAN has addressed enterprise networking challenges by virtualizing the components of traditional WANs. This software-defined approach offers greater reliability by using augmented connection types, improved traffic routing through increased network...

When you’re the one responsible for critical infrastructure assets within the data center, you’ve got to be quick to respond and readily available to take care of any issues that might surface. What if something goes wrong? Without Nodegrid’s Data Logging features,...