Discussing where the G520 falls short, why it matters, and alternative options that deliver consolidated IIoT capabilities and network resilience.


Discussing where the G520 falls short, why it matters, and alternative options that deliver consolidated IIoT capabilities and network resilience.

This guide highlights four Nodegrid models that serve as direct replacements for – or alternatives to – Opengear Lighthouse appliances.

This guide compares five terminal server alternatives that give teams reliable remote management access without unnecessary complications.

This guide to serial console PDU management explains everything you need to know to get started with remote power control and automation.

Learn the difference between end-of-row vs. top-of-rack data center architectures and how to make either deployment more resilient.

This blog explains how data center environmental sensors work and describes the ideal environmental monitoring solution for minimizing outages.

Learn about different types of network virtualization platforms, the benefits of virtualization, and best practices for maximizing efficiency.
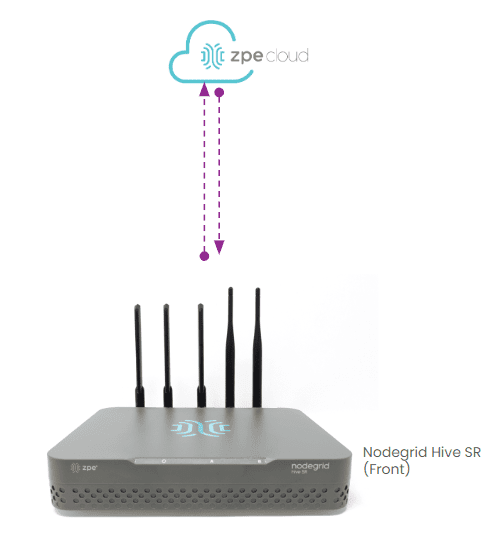
Learn how to overcome your biggest PDU remote management challenges with a centralized, vendor-neutral solution combining the Hive SR and ZPE Cloud.

Perle console server replacement options from Nodegrid are vendor-neutral to provide a fully integrated infrastructure orchestration experience.

Learn how Oxidized network backups improve resilience by mitigating human error and streamlining recovery efforts.

Serial console redirection allows sysadmins to remotely control and troubleshoot servers even when the OS isn’t available. Learn why this matters.

This guide compares the best serial consoles for Linux based on key features, automation capabilities, and security to help you choose the right solution for your enterprise.
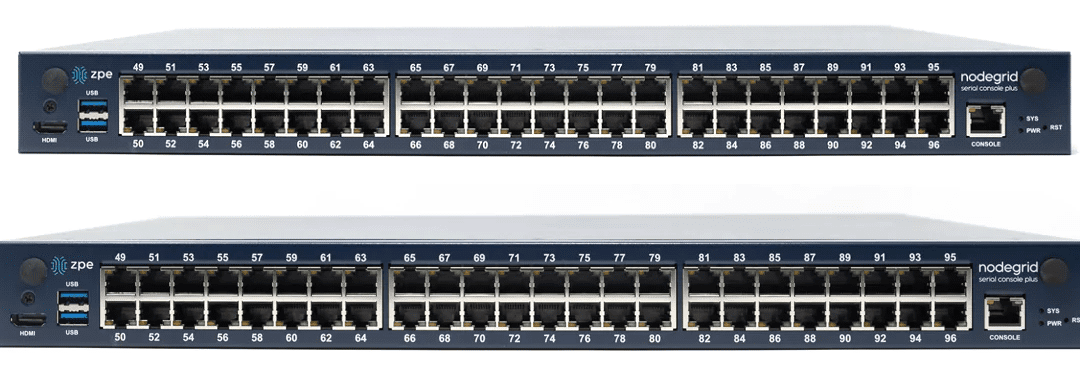
Console server hardware can vary significantly across different vendors and use cases. Learn how to find the right solution for your deployment.

This blog describes various methods for achieving data center scalability before providing tips and best practices to make scalability easier and more cost-effective to implement.

This blog defines serial console interfaces and describes their technological evolution before discussing the benefits of using a modern serial console solution.
This blog describes four edge computing use cases in banking before describing the benefits and best practices for the financial services industry.

This post describes the key components of AI data center infrastructure before providing advice for overcoming common pitfalls to improve the efficiency of AI deployments.
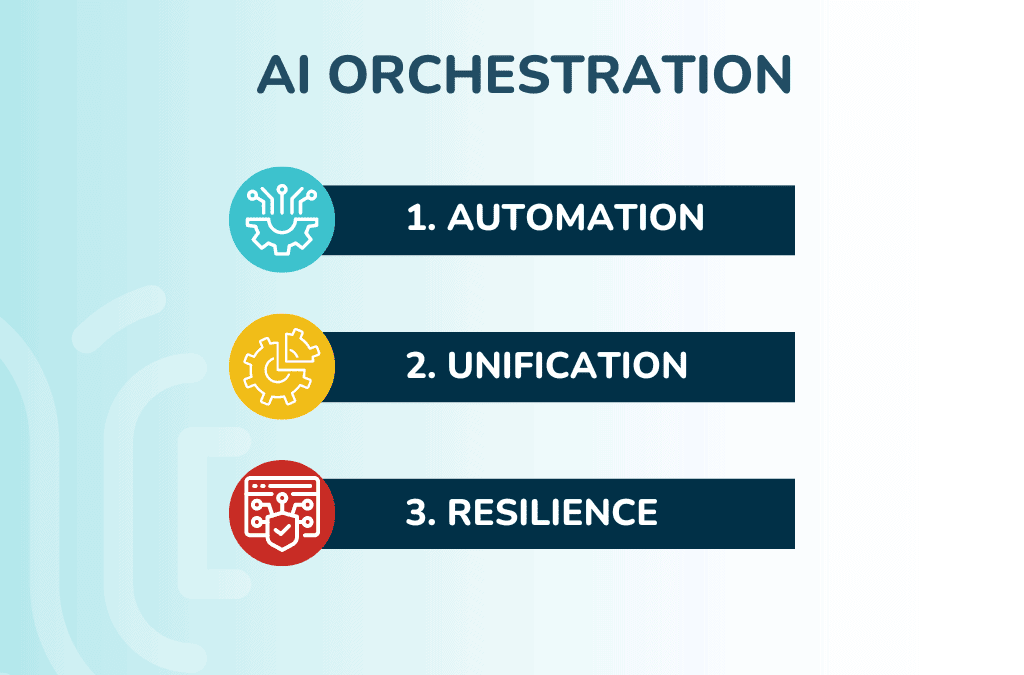
This post describes the ideal AI orchestration solution and the technologies that make it work, helping companies use artificial intelligence more efficiently.

This blog describes five potential edge computing use cases in retail and provides more information about the benefits of edge computing for the retail industry.

This blog describes five potential edge computing use cases in retail and provides more information about the benefits of edge computing for the retail industry.

This blog describes six potential edge computing use cases in healthcare that take advantage of the speed and security of an edge computing architecture.

This blog discusses the five biggest benefits of edge computing, providing examples and additional resources for companies beginning their edge journey.
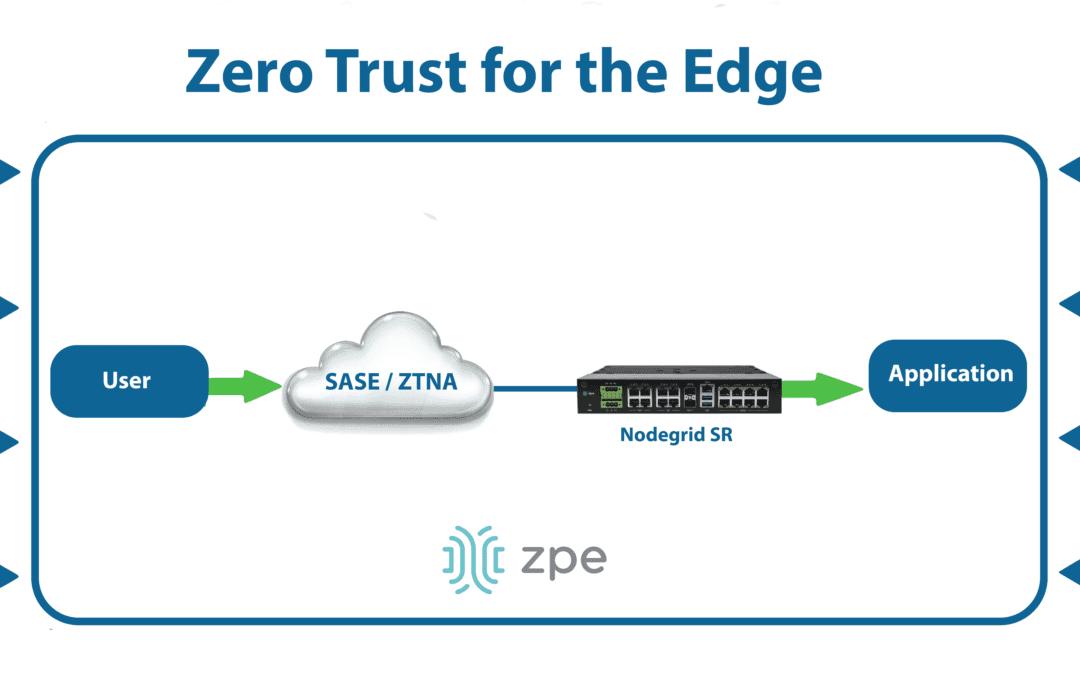
This blog provides advice for improving your zero trust security posture with a multi-layered strategy that mitigates weaknesses for complete coverage.

This guide compares the most popular edge security solutions and offers recommendations for choosing the right vendor for your use case.

This blog discusses some of the applications of edge computing for industries like finance, retail, and manufacturing and provides advice on how to get started.
This blog highlights 7 edge computing examples from across many different industries and provides tips and best practices for each use case.

This guide compares edge computing vs cloud computing to help organizations choose the right deployment model for their use case.
This edge computing architecture guide provides information and resources needed to ensure a streamlined, resilient, and cost-effective deployment.

With limited time to demonstrate compliance with the Critical Entities Resilience Directive, organizations should begin preparing now.

This guide describes the 10 minimum cybersecurity requirements mandated by NIS2 and provides tips to simplify NIS2 compliance.

This guide outlines the technical requirements for DORA compliance and provides tips and best practices to streamline implementation.
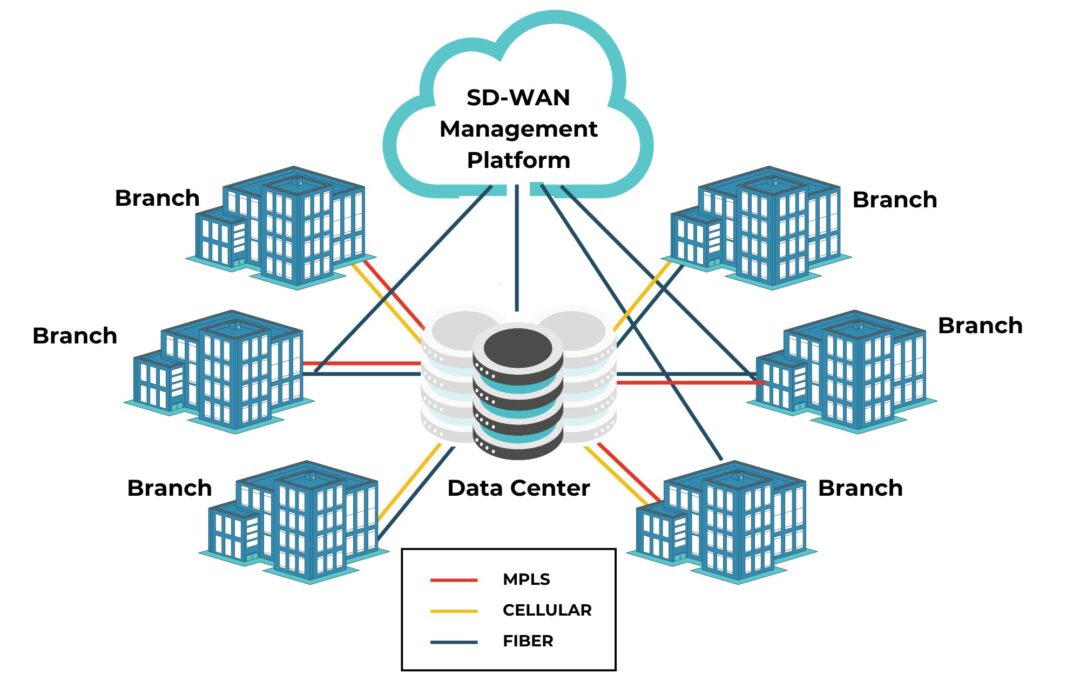
This SD-WAN management guide explains how this technology works, the potential benefits of using it, and the best practices to help you get the most out of your SD-WAN deployment.

This guide summarizes all twelve PCI DSS 4.0 requirements across six categories and describes the best practices for maintaining compliance.
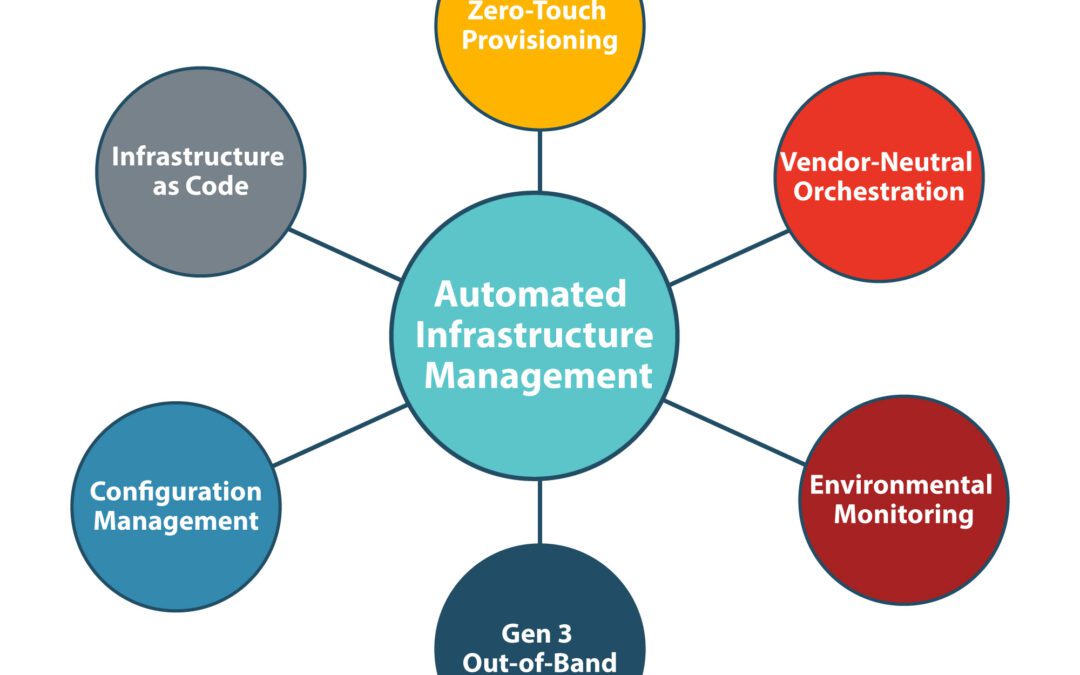
A discussion of how automated infrastructure management improves network resilience by mitigating human error, accelerating recovery, and more.
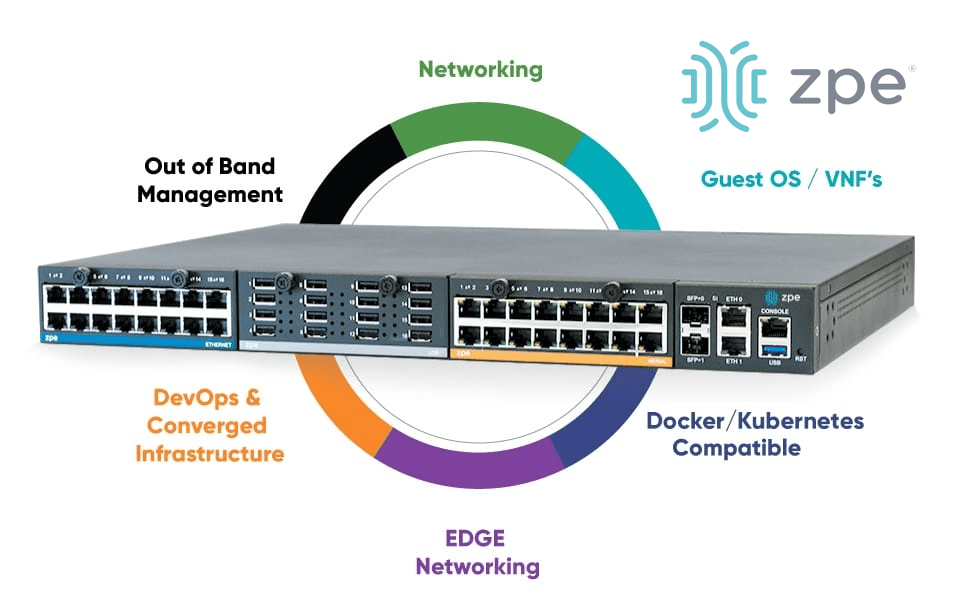
This guide compares Cisco ISR 4431 EOL replacement options and discusses the advanced features and capabilities offered by Cisco alternatives.

This guide compares Cisco 4351 EOL replacement options and discusses the innovative features and capabilities offered by Gen 3 branch networking solutions.

This report uses Gartner’s Magic Quadrant and independent analysis to compare the six SD-WAN leaders based on key factors like features and versatility.

Discussing the Opengear ACM7000 Resilience Gateway and its limitations as well as alternative options from ZPE Systems that cover these gaps for greater resilience and control.

This article compares network resilience vs. redundancy and backups and describes some of the tools and best practices for ensuring resilience.

Discussing the future of edge computing as described by leading analysts at Gartner, which relies on comprehensive strategies and centralized, vendor-neutral edge management and orchestration.
This post discusses six distributed edge computing use cases, including healthcare, finance, oil & gas, manufacturing, utilities/public services, and AI & machine learning.
This post discusses the challenges created by a fragmented edge computing market before providing edge computing ecosystem design best practices to overcome these hurdles.

This guide explains what zero trust edge solutions do and the challenges involved in using them before discussing how to build a unified ZTE platform.
This guide compares IT automation vs orchestration to clear up misconceptions and help you choose the right approach to streamlining your IT operations.
This guide defines edge computing vs on-premises computing in detail before analyzing the advantages and challenges involved with each approach.

Discussing how zero trust security benefits organizations by increasing visibility, reducing the attack radius, and providing precise security coverage.

This guide discusses the network management best practices for improving and supporting network resilience.

This guide to network resilience defines resilience systems, discusses use cases and related technologies, and describes the key components required to build them.

This guide to out-of-band management answers critical questions about what this technology is, why you need it, and how to choose the right solution.

This guide discusses the edge computing requirements for hardware, networking, availability, security, and visibility to ensure a successful deployment.

This guide discusses IT infrastructure management best practices for creating and maintaining more resilient enterprise networks.
This guide to collaboration in DevOps provides tips and best practices to bring Dev and Ops together while minimizing friction for maximum operational efficiency.

This guide answers all your questions about terminal servers, discussing their uses and benefits before describing what to look for in the best terminal server solution.
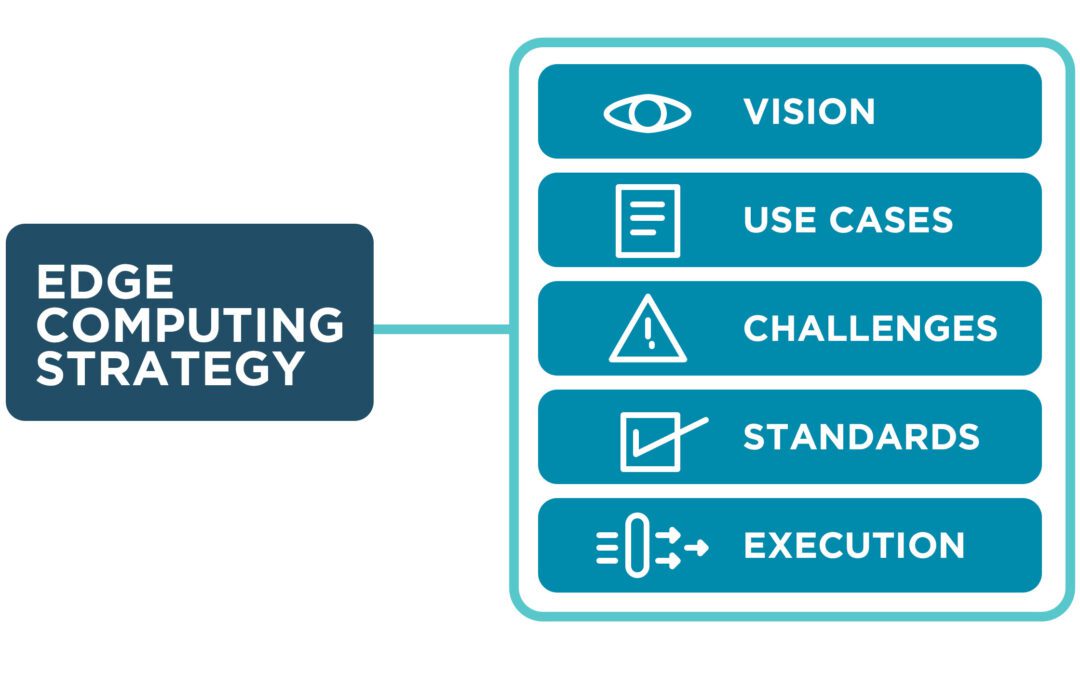
Discussing the Gartner Market Guide for Edge Computing and their recommendations for building a strategy to manage and orchestrate your edge solutions.

This blog defines a hyperscale data center deployment before discussing the unique challenges involved in managing and supporting such an architecture.

A guide to resilient healthcare network design using technologies like automation, edge computing, and isolated recovery environments (IREs).

This blog discusses the various workflows involved in the DevOps lifecycle that can be automated with the best DevOps tools.

This guide compares three of the best network performance monitoring tools by analyzing the most critical factors and discussing the pros and cons.

Comparing the four best OOB network management software tools and discussing the features, pros, and cons to help you make the best choice for your environment.

Explaining the challenges that make ISP network architectures less resilient and providing solutions for overcoming these hurdles.

This post summarizes Gartner’s advice for building an edge computing strategy and discusses how an edge management and orchestration solution like Nodegrid can help.

This post describes some of the most common Intel NUC use cases, explains the security and management issues that caused its discontinuation, and provides superior replacement options.

What is zero trust security? This post defines the term and discusses its history before providing a guide to implementing zero trust in your organization.

This post analyzes the top 5 IT infrastructure management challenges while providing potential solutions and additional resources.

This post provides an introduction to radio access networks (RAN) before discussing 5G RAN challenges, solutions, and use cases.

This data center migration checklist will help guide your planning and ensure you’re asking the right questions and preparing for any potential problems.

This guide defines OT, explains how to overcome some of the biggest operational technology security challenges, and discusses the importance of recovery in building resilience in OT.
Discussing the factors that make medical devices a cybersecurity risk before providing mitigation strategies to help healthcare organizations.

This post defines a zero trust security architecture, discusses some of the gaps typically left in such an architecture, and provides tips for avoiding these pitfalls.

Gartner’s SSE Magic Quadrant for 2023 identifies 10 key vendors currently providing secure service edge capabilities for the enterprise market. In this guide, we’ll summarize the common factors shared among leading SSE vendors, discuss what separates them from niche...

This guide defines an application delivery platform, discusses the underlying technology, and highlights a leading platform engineering solution.

Zero trust for OT uses network segmentation, strong security policies, and advanced security technologies to protect operational technology from attack.

A discussion of how SD-WAN decreases branch networking costs, including an SD-WAN ROI calculator for a more personalized estimate of the potential savings.

This post discusses how to take advantage of IoT in the finance industry by overcoming security challenges with automation, secure platforms, and vendor-neutral orchestration.

The Opengear Infrastructure Manager has a great reputation, but there are some alternatives to explore as well. This post dives into the benefits of the IM7200 as well as worthwhile alternatives.

This post discusses how to save money through automation and provides a network automation cost savings calculator for a more customized estimate of your potential ROI.
Discussing the challenges and security risks associated with Intel NUC jump boxes before providing enterprise-grade Intel NUC alternatives that solve these problems.

In this guide, we’ll compare migration options for the Cisco ISR 2900 EOL models to help you select a solution that suits your business use case, deployment size, and future growth.
The Nodegrid line of Raspberry Pi alternatives from ZPE Systems can help your organization prevent Shadow IT to reduce your attack surface and improve your security posture without increasing costs.

Defining Security as a Service, discussing the pros and cons, and describing an alternative solution for streamlined and scalable cybersecurity management.

Discussing the network management trends observed among enterprises trying to address the unique challenges faced by network teams in 2023 and beyond.
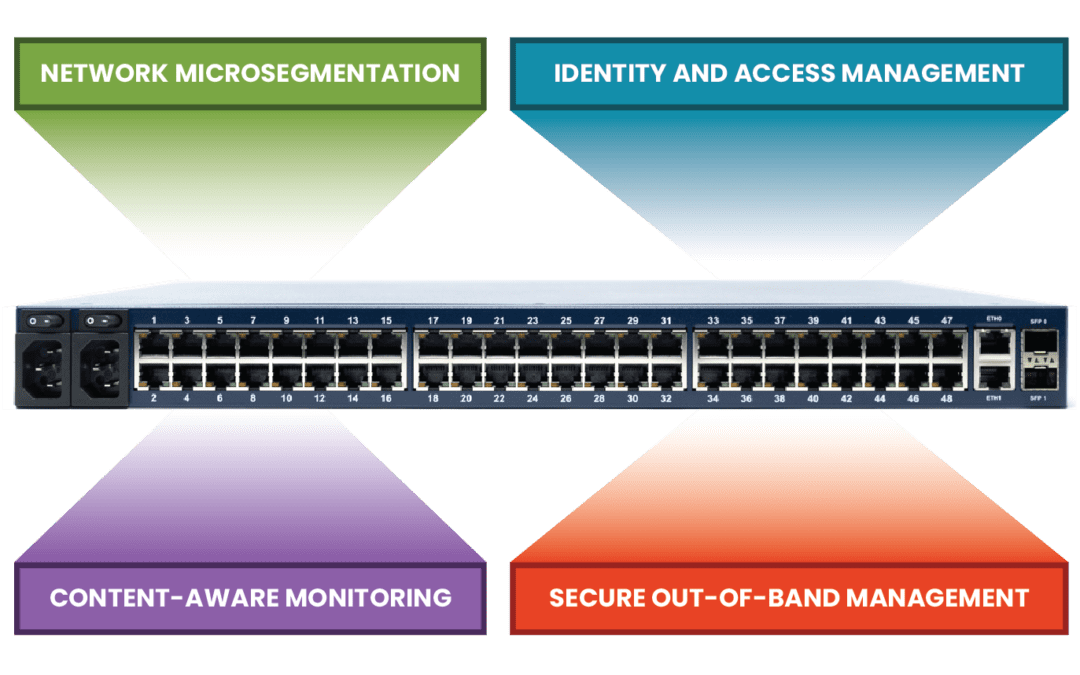
This post discusses the technologies that make up a zero trust gateway and explains how they work together to defend enterprise networks.

This post provides a “cheat sheet” of solutions to the most common zero touch deployment challenges to help organizations streamline their automatic device provisioning.
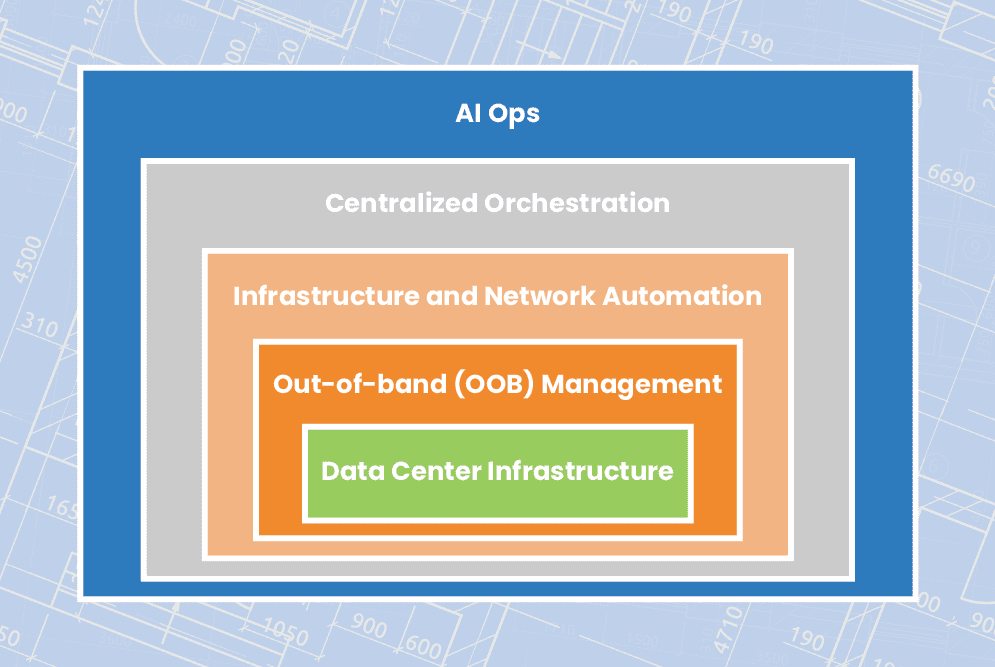
Learn how to streamline remote data center management using technologies like OOB management, automation, orchestration, and AIOps to ensure network resiliency.
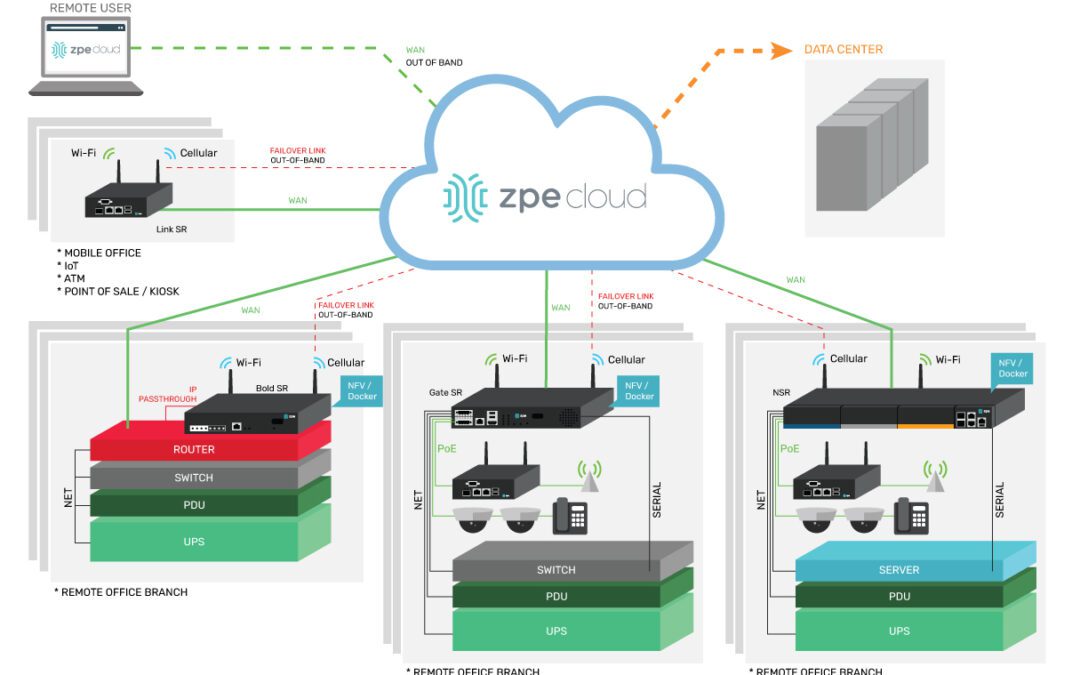
Describing the three cloud-based services involved in a cloud-delivered branch and illustrating how to implement a cloud-delivered branch with Nodegrid.
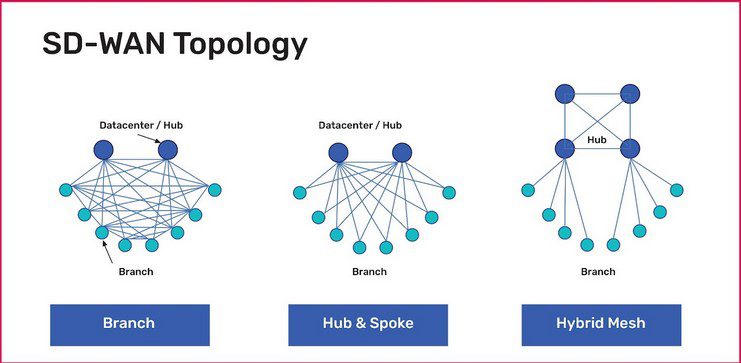
Learn about the most common SD-WAN deployment models with diagrams, pros and cons, and best practices to help organizations choose the right topology.

An isolated recovery environment (IRE) uses designated network infrastructure and survivable data to help teams recover from ransomware faster and with less impact to the business.

SD-WAN benefits organizations through MPLS cost reduction, improved WAN performance, greater automation & orchestration, and enhanced security capabilities.
Compact, all-in-one branch gateways use environmental monitoring, OOB management, and vendor-neutral platforms to simplify retail network management.
Network automation tools help organizations ensure the continued availability and performance of enterprise networks by streamlining workflows and reducing manual intervention.

A centralized, automated OOB remote site monitoring solution helps to ensure network resilience even when recessions, pandemics, and other unforeseen events affect staffing on network teams.

An environment monitoring system should include features like cloud management, vendor freedom, advanced security, and out-of-band management.

Cellular data networks can be used for LTE failover as well as remote out-of-band management, but these two technologies provide different capabilities.

Though white box networking has many advantages in theory, a lot of companies find it hard to achieve these benefits in practice. Here’s how to build a solution that avoids common pitfalls.

An out-of-band cybersecurity platform uses OOB infrastructure, vendor-neutral management software, and end-to-end automation to provide holistic network security.
An IoT device management system is meant to simplify and streamline the management of remote, hard-to-reach, and complex IoT devices and infrastructure.

The best cloud edge gateway solution is vendor-neutral, uses cellular for failover and OOB management, follows Zero Trust best practices, and supports major automation tools and scripting languages.

The LM83X is a direct replacement for the Uplogix 5000 Local Manager EOL model, which means it comes with the same base capabilities and suffers from the same limitations.

The infrastructure orchestration and automation layer contains the tools and paradigms used to efficiently manage and control an automated network.

Let’s discuss how AIOps and machine learning help teams manage their automation and orchestration—and the massive amounts of data produced by their automated systems—more efficiently.
The infrastructure orchestration and automation layer contains the tools and paradigms used to efficiently manage and control an automated network.

As part of a resilient network automation framework, the most important automation infrastructure components include OOBM, SD-WAN, monitoring, IaC, and immutable infrastructure.

An IT/OT convergence strategy brings information technology and operational technology together under one management umbrella to create a unified, efficient, and resilient network infrastructure.

Edge computing for machine learning places ML applications closer to remote sources of data, such as IoT devices, “smart” industrial systems, and remote healthcare systems.

Cellular failover routers, bridges, and gateways offer similar capabilities, so here’s what you need to know about all three to find the best option for your business continuity.

Vendor-agnostic platforms, SD-WAN, and automation are key tools that help organizations more effectively utilize the hybrid cloud in their digital transformation journey.

Here we dig into the causes and effects of data center outages according to the Uptime Institute report and discuss how OOB data center connectivity can help

A renewed enthusiasm for uCPE has been led by a greater interest in software-based networking and a need for hardware capable of running that software.

Vendor-neutral management devices, platforms, and ZTP allow you to upgrade network infrastructure with minimal business interruption.

Software-defined wide area networking, or SD-WAN, has made it possible to efficiently control highly distributed WAN architectures using software abstraction and automation. SD-WAN adoption is increasing, partially due to the rise in remote work during the pandemic,...

How to keep colocation data center pricing in check through consolidated devices, DCIM power management, SDN, and out-of-band management.

There are challenges with managing a complex cybersecurity environment. Here is how Cybersecurity-as-a-Platform (CaaP) can help.

SASE technology connects network edge resources directly to cloud services, reducing the load on the main firewall without sacrificing security.

Data center management best practices like IaC, automation, orchestration, and environmental monitoring contribute to NetDevOps. success.

Data center management best practices like IaC, automation, orchestration, and environmental monitoring contribute to NetDevOps. success.

Manage data center colocation services more efficiently through solutions like environmental monitoring and OOB serial consoles.

ZTNA is the superior choice for branch and edge networking because of its security, speed, and scalability.

Here’s how to solve remote IT infrastructure management challenges using Gen 3 OOB for high-speed remote access, environmental monitoring, and orchestration.

Here’s how data center orchestration with Gen 3 OOB management helps digital service providers achieve the reliability their customers demand.

Discussing Opengear CM7100 replacement options that deliver 24/7 availability, end-to-end automation, Zero Trust Security, and complete vendor freedom.

Wondering about Opengear ACM7000 or Opengear alternatives on the market? Read this post to find out more.

Protecting modern distributed edge networks have its challenges. Discover how the Noregrid SD-WAN solution can help you.

There’s no doubt that edge computing comes with benefits and challenges. Find out how Nodegrid helps you actualize edge computing for your enterprise.

We answer all your questions about In-band management vs Out-of-band management and more in our 2nd blog Reddit Response series.

What is a serial console’s role in modern enterprise networks? Gen 3 serial consoles provide greater control, security, and end-to-end automation.

What is hybrid cloud infrastructure, and how is it achieved? Comparing the expectations vs. reality of hybrid cloud with solutions to common problems.

This blog reviews the Operations Manager platform before discussing Opengear alternatives that provide greater automation, security, and branch networking capabilities.

Discover how Nodegrid’s cloud managed gateway routers deliver powerful edge network management for operational technology automation.

There are two basic approaches to choosing a network management platform: you can stick with a single vendor’s ecosystem of supported products, or go with a vendor agnostic platform. In this post, we’ll explain what a vendor agnostic platform is and how this approach...

Immutable infrastructure involves servers, network appliances, and other devices which are never updated or changed. In part 1 of our blog series, we discussed the most inherent challenges with the immutable infrastructure paradigm. This post will cover immutable...

Immutable infrastructure refers to the critical network resources and systems that make up your infrastructure and that are never updated, changed, or fixed in any way—they stay exactly the same. If something needs to be modified, the entire system or device is...
A supply chain attack is when cybercriminals breach your network by compromising an outside vendor or partner. Often, these attacks exploit a weak link in your trusted ecosystem of third-party software, hardware, and integrations. A hacker will, for example, use a...

An OOB (out-of-band) console server is a fundamental data center tool that allows you to view, manage, and troubleshoot critical remote infrastructure on a dedicated network connection. While the functionality of generation 1 console servers is limited, generation 2...

Your organization may feel secure now, but a disaster could occur at any moment. For example, the war in Ukraine took the world by surprise and left many organizations scrambling to protect and recover critical infrastructure, applications, and data from Ukrainian...
A hybrid network environment combines infrastructure from a public cloud with a private cloud and/or on-premises deployment. Your compute, storage, and service resources are distributed across multiple locations and platforms and connected via WAN (wide area network)....

Automation can help you streamline network management in your enterprise by reducing human error, speeding up processes, and facilitating NetDevOps. Hyperautomation takes things a step further by attempting to remove all human intervention from IT and business...

Out-of-band access gives you an alternative path to manage your critical remote infrastructure at data centers, branch offices, and other distributed locations. However, that management link creates an additional point of entry for malicious actors to breach and even...

As enterprise networks grow more complex and distributed, the need for network automation is rising. Automation can help you manage your network more efficiently, but only if you use it correctly. This article discusses the three best network automation practices as...
A branch network consists of many moving pieces that need to be remotely deployed, managed, and supported. That typically means separate devices for all the key functions like routing, switching, security, etc. However, as data and applications grow more...

Data center infrastructure management (DCIM) keeps evolving to address enterprises' changing goals, requirements, and concerns. We spoke with DCIM sales engineers to find out which pain points are on their customer’s minds, and which emerging technologies their...

The importance of network automation is clear—you can reduce human error, create more efficient workflows, and streamline operations. However, many enterprises delay their automation efforts because of how challenging the process can be. Fortunately, automating your...

Branch network management involves many moving parts. For example, you may need to remotely deploy, orchestrate, and troubleshoot the branch network without on-site IT staff. In addition, you need a way to connect your branch locations to the enterprise network and...

Vertiv discontinued their Avocent ACS6000 line of serial console servers at the end of 2018 and will stop supporting them on July 31, 2023 (or whenever your warranty expires). The Vertiv Avocent ACS EOL guide recommends the ACS8000 series as a direct replacement, but...

How critical is network security today?. According to IBM, the cost of a data breach rose to $4.24 million in 2021, and that figure continues to rise. In this blog, we’ll describe how to achieve network security through micro-segmentation, zero trust principles,...

Data lakes are a powerful tool for capturing, storing and analyzing data from many different sources. A data lake provides an inexpensive, flat storage architecture in which to house massive amounts of unstructured data, which can then be easily accessed by your data...

Temperature and humidity have a significant impact on your data center infrastructure. High temperatures can cause devices to overheat, whereas extreme low temperatures can cause mechanical and electrical failures. High humidity can lead to moisture build-up,...
Branch locations—retail stores, shipping warehouses, and satellite offices—present a big network management challenge to the engineers supporting them. Traditional remote network management requires a WAN link to each branch, but what happens if that link goes down?...
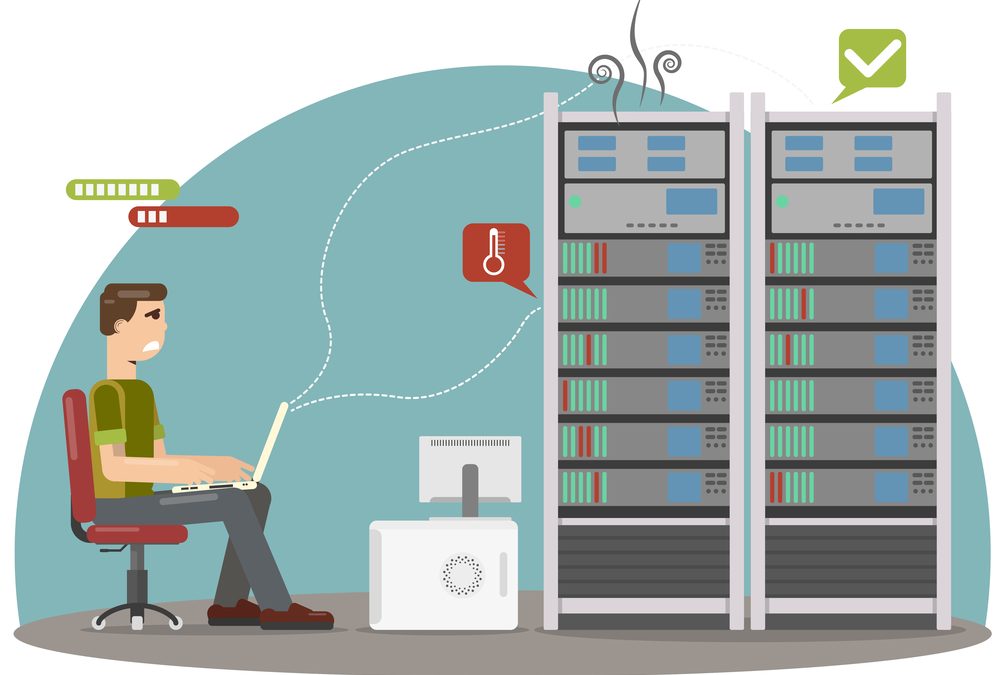
Today, many businesses are completely unable to operate without their data center infrastructure, so data center downtime is getting more and more expensive. According to Uptime Institute’s 2021 Global Data Center Survey, over 60% of respondents lost more than...
Hybrid cloud—using a combination of public and private clouds to host your data, applications, and services—is one of the most popular enterprise infrastructure models. According to Flexera’s 2021 State of the Cloud Report, 82% of enterprises have a hybrid cloud...

Environmental threats—such as heat, moisture, power, smoke, and tampering—constitute a significant cause of data center downtime. According to a recent ITIC survey, a single hour of downtime could cost over $300,000 in lost business, which means you can’t afford to...

Data center infrastructure management, or DCIM, involves monitoring and controlling the infrastructure within a data center. That means supporting the appliances and the underlying infrastructure—everything from servers and switches to power and HVAC systems. Though...

Environmental threats—such as heat, moisture, power, smoke, and tampering—constitute a significant cause of data center downtime. According to a recent ITIC survey, a single hour of downtime could cost over $300,000 in lost business, which means you can’t afford to...

NetDevOps, SecOps, and EdgeOps are crucial components of a holistic and integrated approach to network infrastructure. However, the way each practice works to achieve this objective is not immediately apparent, and understanding this paradigm can be vital to a...

Managing and orchestrating remote data centers presents a number of challenges, which is why you need the right tools for the job. Nodegrid as a data center orchestration tool is a family of hardware and software solutions that address these unique challenges. Let’s...

Over the last years, IT professionals have placed a larger focus on edge computing for businesses as they have increasingly turned to remote work in response to Covid-19. Because of this shift, network engineers are developing new use cases for edge computing in some...

One of the most prominent edge computing challenges any organization may face is deploying and managing their critical remote edge infrastructure. For instance, the lack of network edge orchestration can lead your organization to have gaps in the automation pipeline,...

Data centers face a uniquely modern challenge when it comes to climate. Government estimates place data center energy consumption at 10 to 50 times the energy per floor space of a normal commercial building. These estimates are further complicated by tenuous...

The colocation data center market saw huge growth during and after the COVID-19 pandemic, reaching a value of $76.8 billion in 2023 and showing no signs of slowing down. Companies continue to move away from on-premises deployment strategies due to the expense and...

SecOps is the blending of security and IT operations into one combined set of workflows, tools, and methodologies. This increases the speed at which new infrastructure can be spun up without impacting the quality or security of your systems. Let’s discuss what SecOps...

The NetDevOps methodology helps organizations streamline their network, development, and IT operations through automation and cross-team collaboration. This blog will explain the NetDevOps transformation process and the critical steps you need to take to implement...

Security Service Edge (SSE) is an emerging network security model that rolls up technologies like zero trust network access (ZTNA), cloud access security broker (CASB), secure web gateway (SWG), and next-generation firewalls/firewall as a service (FWaaS) into a...

Security service edge (SSE) is an emerging network security model, first announced by Gartner in their 2021 Hype Cycle, that stems from the need to retool the industry’s thinking about SASE (secure access service edge). SSE protects your network edge by combining...

Modern network management involves a wide variety of distributed technologies. Because of this, enterprises have progressively moved towards the Security Access Service Edge (SASE) model to provide remote users with secure cloud-based services. Even though these...

Large enterprises rely on the management and administration of their networks to continue their daily operations. In recent years, networking trends have pointed towards using automated processes to regulate and administer enterprise networks. Automated networks free...

Zero trust security is not a new concept, but it has gained popularity in recent years. As companies become increasingly distributed, they must offer flexible network access without putting sensitive data at risk. That’s where zero trust security comes in. What is...

Data center infrastructure adds an extra layer of complexity to enterprise networks since you need to remotely manage hardware at scale. The network perimeter needs to extend across a geographical distance—which could be several miles or several continents—while...

The rapid development of data center infrastructure management (DCIM) tools leaves most software quickly becoming outdated. Consequently, it is replaced by the next trend on the market, after a short time. The use of such software following its “expiration” creates...

How do secure access service edge (SASE) and zero trust work together to improve network security? Simply put, SASE works by deploying security via the cloud, and zero trust deploys security in the least privileged access method. Networking trends have heavily shifted...

SASE—which stands for secure access service edge—is a relatively new framework that converges wide-area networking with security into one cloud-based service stack. SASE uses software-defined wide area network (SD-WAN) technology to directly connect branch offices and...

As workloads, applications, and data move to the cloud and business operations expand to include branch offices, remote data centers, and work-from-home staff, how do you define your network security perimeter? With zero trust networks, you don’t have to. Zero trust...

Ransomware is one of the biggest threats to enterprise network security. Recent findings show that 37% of organizations were affected by ransomware attacks in 2020 alone. These attacks can be financially devastating, costing companies an average of $1.85 million in...

Perimeter-based security is no longer sufficient for today’s enterprise network. You may even struggle to define your network perimeter anymore, mainly if you use cloud infrastructure, have remote data centers and branch offices, or rely on “Internet of Things” (IoT)...

Though every business network is unique, they all broadly fall under one of the following architecture categories: centralized (or decentralized using server clusters) and distributed. Let's discuss how centralized vs. distributed network management models work,...

SASE—secure access service edge—combines SD-WAN technology with network security functionality into a single cloud-native solution. SASE uses SD-WAN’s intelligent routing to connect remote and branch users directly to cloud services, improving network and application...

Out-of-band network management gives enterprises secure and remote access to critical network infrastructure, even during outages and service interruptions. It separates your production network from your management plane, allowing you to remotely troubleshoot,...

Secure access service edge (SASE) is the recommended architecture for security and connectivity. SASE combines wide area network (WAN) technology for robust onramp to cloud and network security services into one cloud-delivered connectivity and security software...